Shopping for Credentials with Cmdkey.exe
A lot of my work is done from a standalone computer, in other words one that doesn’t belong to a domain. But, I often need to access things in my test lab domain. If it is PowerShell related, I can often get by using a –Credential parameter if the cmdlet I want to use happens to support it. In other situations, applying alternate credentials can be tedious. But there is a useful command-line tool that makes it easy to shop for the credentials you need. I’m pretty sure there is a graphical alternative, but the command line is so much faster.
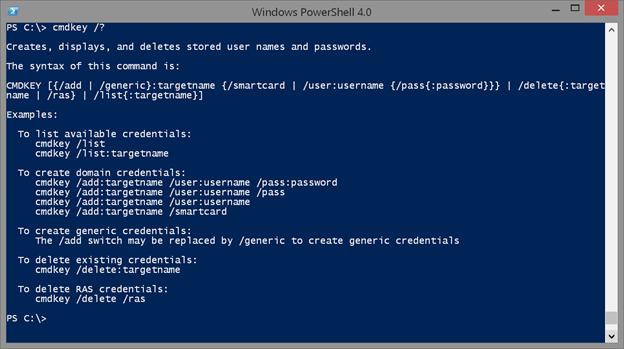
The utility in question is called cmdkey.exe. You can even run it in PowerShell. Because this is a command-line tool, you’ll need to learn its syntax.
Cmdkey /?
Let me show you how you might use it in a domain environment. I’m sure you are familiar with the concept of Least Privileged Use, which should apply to domain administrators as well. The account you logon on with and run your daily work under should be a non-privileged account. It should be like any other user account. You should then have a separate domain admin account that can be connected with you.
Personally, I don’t think anyone should use the administrator account. Even with logging it is next to impossible to know who used it. Was it John or Jane? Or was it someone unauthorized? Instead create domain admin accounts with a name like da_john and da_jane. Something that indicates who the domain admin account belongs to. Now I can have a meaningful audit trail and if I see the administrator account in use, then I know there is a problem because nobody should be using it.
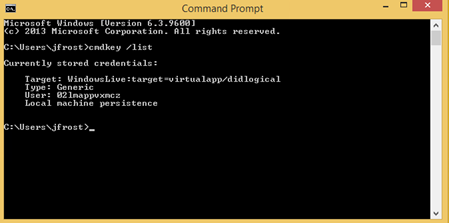
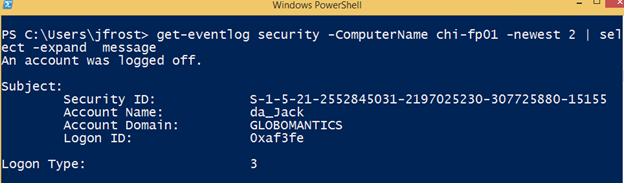
Here’s where cmdkey can come in handy. In my domain, there is a user Jack Frost. He has a non-privileged account (jfrost) as well as a domain admin account (da_jack). Right now, Jack has no credentials stored.
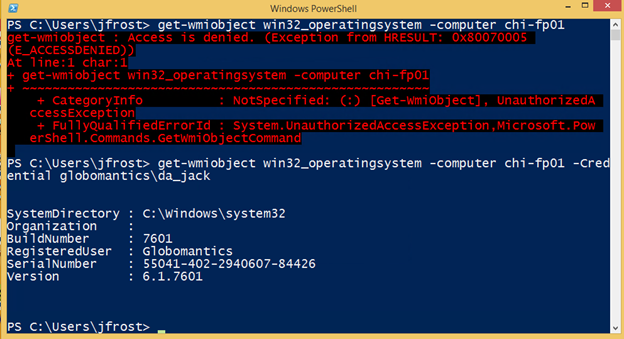
In PowerShell, if he tries an operation that requires admin privileges, it will fail, unless he uses his domain admin credential.
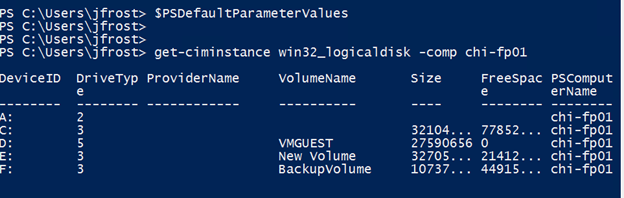
On one hand, it may not be that big a deal to specify the credential. In fact, beginning with PowerShell 3.0, he could even set a default parameter value so that any cmdlet that had a –Credential parameter would use the domain account.
$cred = get-credential globomantics\da_jack
$PSDefaultParameterValues.add("*:Credential",$cred)
Now any command with –Credential will use this value. But this doesn’t help for everything else.
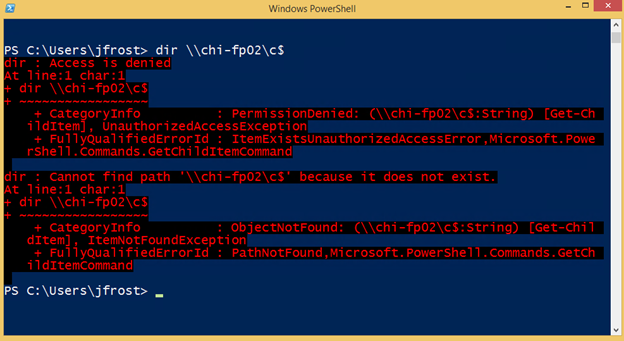
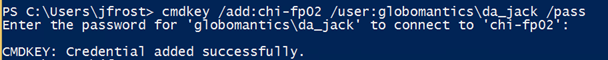
This is where cmdkey is a real timesaver. Jack can add an entry to his store for Chi-fp02. Run cmdkey /add /? to see all the options.
Cmdkey /add:chi-fp02 /user:globomantics\da_jack /pass
I also could have entered the password as part of the cmdkey command.
Cmdkey /add:chi-fp02 /user:globomantics\da_jack /pass:MyPasswordHere
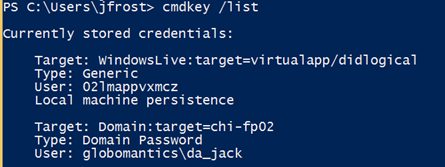
But now it is stored and persistent.
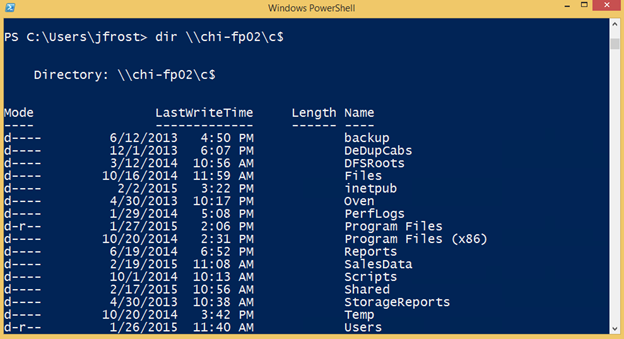
When Jack tries to access the target, Windows will use this stored password.
At some point, Jack will need to change his password. He can re-run the Add command with the new password. You can also delete items by target name.
Cmdkey /delete:chi-fp02
However, the previous credentials are cached until the user logs off.
If you need to authenticate for multiple computers, you’ll need to add an entry for each one. A command like this will fail.
Cmdkey /add:chi-* /user:globomantics\da_jack /pass:MyPasswordHere
But it isn’t too difficult to process a list of computer names and add a credential for each one.
get-content c:\work\chi.txt | foreach { cmdkey /add:$_ /user:globomantics\da_jack /pass:P@ssw0rd}
Now, even without a setting in $PSDefaultParameterValues, Jack can do all of the domain admin work he needs without having to bother entering his domain admin credentials.
But the activity can be tracked to his domain admin account.
So if you have been running your daily work under a domain account because it is easier, think again. There are potentially serious security consequences. But using something like cmdkey should take away the pain. Of course, be sure to lock your computer when you step away from your desk. But you do that anyway, right?
Do you use cmdkey? How do you handle the burden of maintaining and using a separate domain admin account? I hope you’ll share in the comments.