
Security researchers have unveiled a new malware that is infecting Linux endpoints and Internet-of-things (IoT) devices. The malware allows attackers to gain persistent access to the compromised system and deploy crypto-mining software.
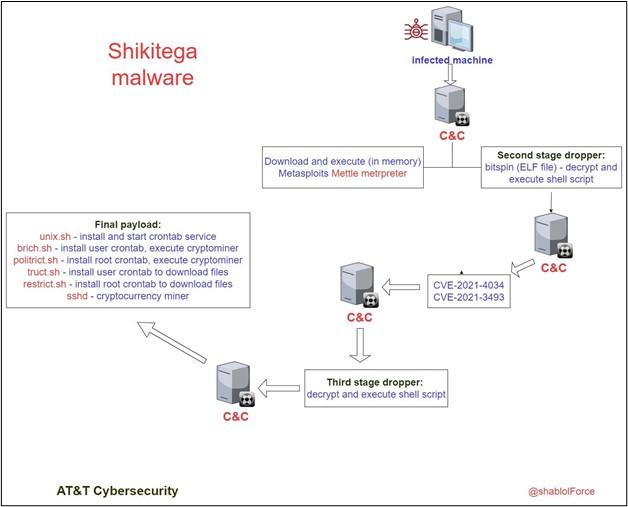
The stealthy malware dubbed “Shikitega” was first discovered by cybersecurity researchers at AT&T Alien Labs. The malware is delivered in a multi-stage infection chain via polymorphic encoding. This technique enables the malware to mutate its code, making detection extremely difficult by antivirus tools.
“Threat actors continue to search for ways to deliver malware in new ways to stay under the radar and avoid detection,” explained AT&T Alien Labs. “Shikitega malware is delivered in a sophisticated way, it uses a polymorphic encoder, and it gradually delivers its payload where each step reveals only part of the total payload. In addition, the malware abuses known hosting services to host its command and control servers.”
Shikitega malware lets attackers install crypto miner payloads
Additionally, Shikitega downloads a harmful Metasploit package called “Mettle.” It lets threat actors take control of attached webcams, control processes, execute shell commands, steal credentials, and much more. The malware also exploits two critical Linux vulnerabilities (CVE-2021-4034 and CVE-2021-3493) to install and run the XMRig cryptocurrency miner. The software allows the attackers to secretly mine the Monero cryptocurrency on affected devices.
“To achieve persistence, the malware will download and execute a total of 5 shell scripts. It persists in the system by setting 4 crontabs, two for the current logged in user and the other two for the user root. It will first check if the crontab command exists on the machine, and if not, the malware will install it and start the crontab service,” AT&T added.
AT&T has detailed file hashes and domains that can help organizations to detect indicators of a compromise in enterprise environments. It recommends that organizations should install the latest security patches on Linux endpoints and IoT devices. Moreover, IT admins should keep Endpoint Detection and Response (EDR) software up to date and regularly back up important data.



