So you’ve just finished preparing a new system using Windows Server 2008 R2 and now you’re ready to deploy it to production. You’ve prepared the physical hardware or virtual machine according to the system requirements, installed and configured the operating system, configured any necessary roles and/or features, perhaps joined the domain and applied group policy settings required for this system’s particular role, and finally installed anti-virus software along with your system management agents. But is this system really ready for production? Perhaps not! Today I’ll go through security hardening techniques in Windows Server 2008 R2.
Why Perform Security Hardening?
In my experience, production servers are often deployed without consideration for the overall security posture of the system – an oversight that can often lead to serious security issues in the future. Before releasing a server to production, it would be wise to perform some level of system security hardening in an effort to reduce the attack surface and lower the potential for compromise. This process should be conducted on each server prior to production deployment, and it should be performed on a per-workload basis, as the security characteristics change dramatically depending on applications (e.g. file and print, IIS, domain controller, etc.) and network location (e.g. internal, Internet accessible, edge facing, etc.).
It’s important to understand that even if the server you are deploying doesn’t hold sensitive data, it is still important for it to be secure. If, for example, a seemingly unimportant server is successfully compromised it can still be used as a pivot point by an attacker to conduct further reconnaissance and information gathering in order to mount additional attacks with the ultimate goal of finding and stealing your organization’s confidential data. Thankfully there are some tools and techniques that you can leverage to make it much more difficult to compromise your servers.
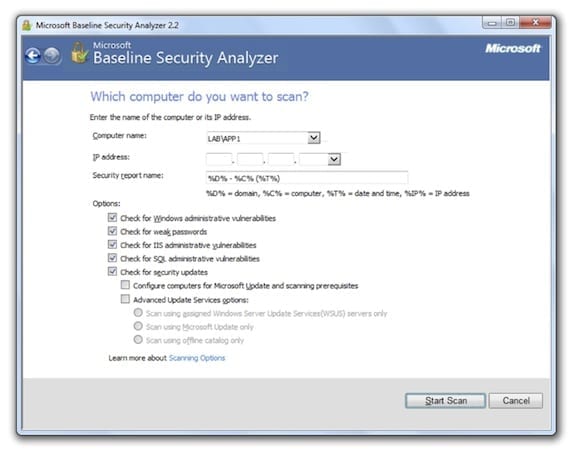
Microsoft Baseline Security Analyzer (MBSA)
The Microsoft Baseline Security Analyzer (MBSA) is an excellent free tool that can be used to provide a detailed assessment of the security configuration of your Windows Server 2008 R2 host. As of this writing, you can download the latest version of MBSA (which at the time of this writing is version 2.2). Note: MBSA v2.2 does not yet support Windows 8 or Windows Server 2012.
Security best practices dictate that you would install this tool on your administrative workstation, but you can install it directly on the server if necessary. The tool also requires that you have local administrative rights on the target system. Once the MBSA is installed, select a target to scan. You can select an individual host or multiple computers. By default, the MBSA will check for Windows administrative vulnerabilities, weak passwords, IIS administrative vulnerabilities, and SQL administrative vulnerabilities. In addition it will also check for security updates. The tool can be configured to use Microsoft Update, your local Windows Server Update Services (WSUS) servers, or an offline catalog.
Once the scan completes, the MBSA will provide a detailed report of its findings, listed in order of severity. The results can then be used to address potential security issues on the system. These reports can be saved and viewed later, if required.
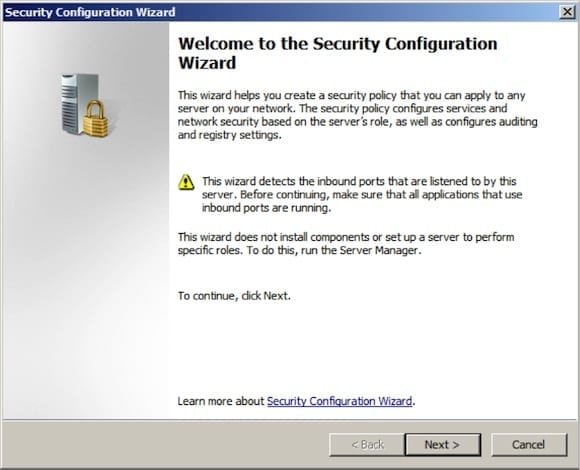
Security Configuration Wizard (SCW)
Once you’ve addressed the security issues uncovered using the MBSA, the next step is to perform a comprehensive attack surface reduction on the system. The purpose here is to limit the exposure of the system by disabling services that are not required to support the workload running on the server, and configure additional network security, authentication, and audit settings to support a secure server.
While it’s possible to perform this process by manually, the ideal way to do this is to use the native Security Configuration Wizard (SCW) included with the operating system. The SCW will walk you through the process of gathering information about the intended role of the server and will create a security policy that can be applied to the target system. The SCW also allows you to edit existing policy and optionally perform a rollback of an applied policy. To open the SCW, navigate to Start/Administrative Tools and click the Security Configuration Wizard.
Select the option to create a new security policy and specify the name of the server. Once the configuration database has been processed, role-based service configuration will begin. The SCW will automatically select any roles, features, and options that are installed on the system. You can review the list and make changes as necessary depending on your specific implementation. You have the option of disabling any services that are not explicitly specified during the configuration, so choose this option carefully. While it may provide the highest level of protection, it can potentially break functionality for legitimate services and applications.
In addition to service configuration, the SCW also addresses network security configuration, registry settings, SMB security signatures settings, outbound authentication methods, and audit policies. Once you’ve completed the SCW you can save the policy as an XML file. You can apply the security settings contained in this file now or later. It is possible to convert the security configuration XML file to an Active Directory Group Policy Object (GPO) using the scwcmd.exe command line tool. The syntax for this tool is:
scwcmd.exe transform /p:PathandPolicyFileName /g:GPODisplayName
For example: scwcmd.exe transform /p:iis_default.xml /g:”IIS Default Policy”
System and Application Updates
The process of system hardening and attack surface reduction can go a long way to creating a more secure computing environment. However, it is important to realize that these efforts only address the potential exposure and attack vectors used by an attacker at this point in time. The overall security of the solution must be maintained on an ongoing basis to provide the highest level of protection for our applications and data. A comprehensive update management solution is vital to addressing this requirement. The solution should monitor and manage not only operating systems updates, but application updates as well.
A simple and effective way to manage these updates is using the Windows Server Update Services (WSUS) role included with Windows Server 2008 R2 or Windows Server 2012. WSUS allows you to much more effectively monitor the state of update deployment in your environment. Once installed, you can configure your Windows systems (clients and servers) via GPO to use your internal WSUS server to obtain operating system and application updates. WSUS includes robust reporting tools that enable you to clearly identify which systems are missing updates, reducing the chance that an attacker can successfully exploit a vulnerability for which there is an existing update. In addition to WSUS, Microsoft System Center Configuration Manager is an excellent alternative to WSUS for large enterprise environments. There are also a number of good third-party tools that make the job of managing updates much easier.
Remote Management Tools
Using system management best practices can also serve to improve the security posture of your environment. For example, it is good security practice to avoid logging in to the server interactively using a domain administrative account. If an attacker can successfully compromise a server and gain local administrative rights through privilege escalation, it will be possible to obtain the password hashes for anyone who has logged in to the console of the server. Using a technique called “pass the hash,” it will be possible for the attacker to then masquerade as a legitimate domain administrator, which of course will provide them with nearly unlimited access to data and information on your network. For these reasons it is best to use remote management tools as much as possible. To facilitate remote system management, Microsoft makes available the Remote Server Administration Tools (RSAT) for use on Windows Vista, Windows 7 SP1, and Windows 8. The Sysinternals PsTools suite is another excellent way to remotely manage systems. Also, don’t forget that PowerShell has very powerful remote administration capabilities too.
Hardening Security: Additional Considerations
For the highest level of security, consider deploying services and applications on Windows Server core. This will provide the least possible attack surface, which not only improves security but also increases availability, as many of the features of the operating system that are updated frequently (e.g. Internet Explorer) have been removed and don’t require servicing. Server core does not include a GUI, and it is configured and managed completely from the command line.
Remote Management Redux
RSAT tools can also be used to remotely manage a Windows Server core system. Windows Server core does not support all workloads, but it is an excellent choice for infrastructure services like Active Directory, file and print servers, DNS, DHCP, and others. One of the drawbacks to Windows Server core in 2008/R2 is the fact that you can’t switch from GUI to core or vice versa. Essentially, the decision is made once when you choose the installation; it can’t be changed without a full wipe and reload of the operating system. Windows Server 2012 now includes the ability to switch from core to GUI as required, and also supports additional workloads. Windows Server 2012 also has a “minimal server interface” installation mode that provides better compatibility for server applications that require some GUI features.
Think Like an Attacker: Network Port Scanning Tools
In addition to some of the techniques I’ve discussed here, it’s also a good idea to periodically evaluate and assess our systems from an attacker’s point of view. This includes network port scanning using tools like PortQry, a Microsoft command line port scanner, or NMap, a command line port scanner with an optional GUI. Using these tools will give you an idea what services your server is listening and responding to on your network. Data from these tools can be used to configure the local Windows firewall to provide additional protection. Penetration testing can also be a useful exercise to determine what vulnerabilities can be potentially exploited remotely. There are free and commercial tools that are available to handle this task.
Password Protection
No discussion about server security would be complete without discussing passwords. Every effort should be made to enforce long and complex passwords, and to ensure that they are rotated on a regular basis. Avoid shared accounts, and consider using dynamic, one-time passwords (OTP) for systems that manage sensitive data. Limit the number of domain administrators in your organization and avoid service accounts that have domain administrative privilege at all costs.
With careful planning and some diligence, you can improve your resistance to attack by following the guidance I’ve outlined here. Attackers frequently exploit weaknesses in security configuration to gain access to our systems. By using the Microsoft Baseline Security Analyzer you can be aware of any potential configuration errors that might make it easier for a system to be compromised. In addition, attackers often seek to exploit vulnerabilities in the operating system, and increasingly applications, in an effort to compromise our defenses. An all too common occurrence is when a system is compromised by a vulnerability for which an update has been widely available, sometimes for months or even years. Here you can leverage update management solutions to ensure that you systems are always up to date, reducing your vulnerability window from months to days or even minutes. And by following some administrative best practices we can further reduce the chances that an attacker could obtain valid credentials for an administrator.
Always keep in mind that security is a process, not an end state. There is no way to simply run through a configuration tool and declare a system secure. However, using these tools and applying these security practices on an ongoing basis will yield positive security benefits in the long run.