Cybercriminals Exploit OpenMetadata Flaws to Target Kubernetes Clusters

Key Takeaways:
- Microsoft has identified critical vulnerabilities within OpenMetadata, posing a significant security risk to unpatched Kubernetes clusters.
- These vulnerabilities could potentially enable cybercriminals to execute remote code attacks.
- Organizations are urged to promptly update their OpenMetadata workloads and implement robust security measures to mitigate the risk of exploitation.
Microsoft has recently unveiled critical vulnerabilities within OpenMetadata’s open-source metadata repository. The security flaws could allow cybercriminals to execute remote code attacks on unpatched Kubernetes clusters.
OpenMetadata is an open-source platform that offers a centralized metadata management solution for data lakes, pipelines, and warehouses. It enables businesses to discover, understand, and govern their data assets across different data platforms. The ingestion framework of OpenMetadata supports connectors for various services, including Atlas, Apache NiFi, Airflow, Amundsen, and Athena.
Kubernetes RCE Attack flow
In mid-March, Microsoft’s researchers discovered several critical vulnerabilities (CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, CVE-2024-28254) impacting OpenMetadata versions 1.2.4 and 1.3.1. Since early April, threat actors have been actively exploiting these flaws to target unpatched Internet-exposed OpenMedata workloads. These vulnerabilities allow hackers to gain access to vulnerable Kubernetes environments, which they can then exploit for cryptocurrency mining.
“Once they identify a vulnerable version of the application, the attackers exploit the mentioned vulnerabilities to gain code execution on the container running the vulnerable OpenMetadata image,” the Microsoft Threat Intelligence team explained. “Once the attackers confirm their access and validate connectivity, they proceed to download the payload, a cryptomining-related malware, from a remote server. “
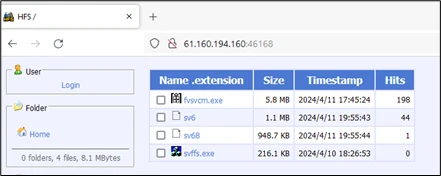
(Image credits: Microsoft)
In the second stage, the threat actors remove the initial payloads from the workload and employ the Netcat tool to establish a reverse shell connection to their remote server. This method enables hackers to take complete control of the compromised system and maintain continuous access.
Microsoft advises organizations to update the OpenMetadata workloads (version 1.3.1 or later) running in their Kubernetes environment. It’s highly recommended to use strong authentication methods and reset any default credentials. Organizations can also use security tools (such as Microsoft Defender for Containers and Microsoft Sentinel) to block Kubernetes crypto-mining attacks.


