
Key Takeaways:
- Microsoft has warned that hackers are exploiting OAuth for automated financial cyberattacks.
- Threat actors use various tactics such as password spraying and phishing to compromise user accounts and launch attacks.
- Organizations are urged to implement multifactor authentication and dynamic conditional access policies to boost security against OAuth attacks.
Microsoft has issued a warning about cybercriminals exploiting OAuth for automated financial cyberattacks. The Threat Intelligence team has identified that threat actors are creating malicious OAuth apps to carry out password spraying, phishing, and crypto mining activities.
OAuth (Open Authorization) is an open standard designed to offer secure third-party access to user resources on a website or application without the need to share credentials. It uses tokens (such as refresh tokens or access tokens) to effectively manage the authorization process securely.
The Microsoft Threat Intelligence team has recently published a blog post highlighting a series of campaigns that aimed to compromise user accounts and conceal malicious activity by creating, modifying, and granting high privileges to OAuth apps. The attackers primarily targeted user accounts that lacked strong authentication mechanisms. Microsoft revealed that the hackers utilized password spraying, crypto mining, and business email compromise (BEC) techniques to execute the attacks.
The Storm-1283 hacking group infiltrated an account to develop an OAuth application, which they then used to deploy virtual machines for crypto mining. As a result, the targeted organizations were charged Azure compute fees ranging from $10,000 to $1.5 million.
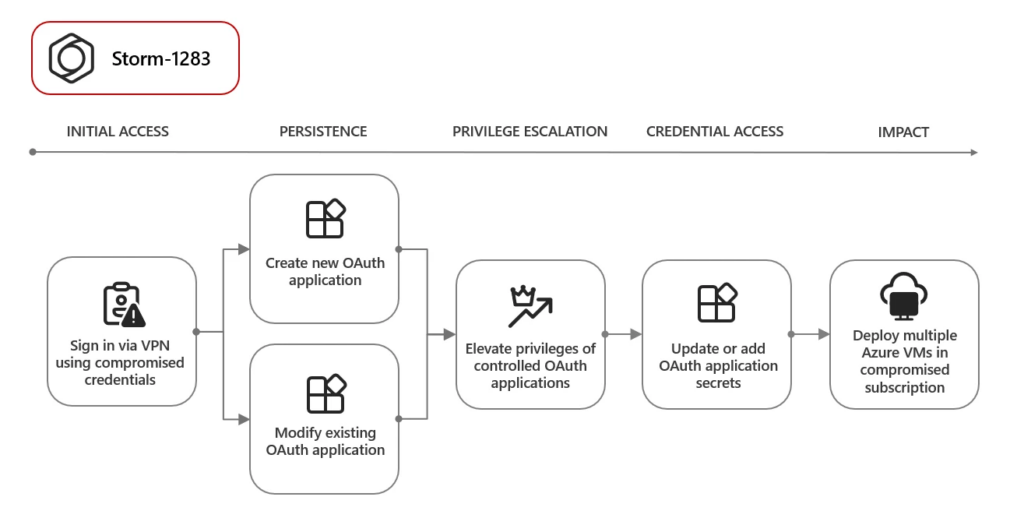
In addition, Microsoft’s researchers discovered that another threat actor (Storm-1286) employed password-spraying tactics to gain access to email accounts. These accounts were used to create new OAuth applications with Azure PowerShell or a Swagger Codegen-based client.
“These applications were set with permissions like email, profile, openid, Mail.Send, User.Read and Mail.Read, which allowed the actor to control the mailbox and send thousands of emails a day using the compromised user account and the organization domain,” Microsoft explained
OAuth applications used for phishing campaigns
In a third attack, an unidentified cybercriminal used an adversary-in-the-middle (AitM) phishing kit to send a large number of emails to multiple organizations. The emails included a malicious URL that directed the recipients to a proxy service. This service allowed the hacker to steal tokens from the user’s session cookie, which could then be used to perform session cookie replay activity.
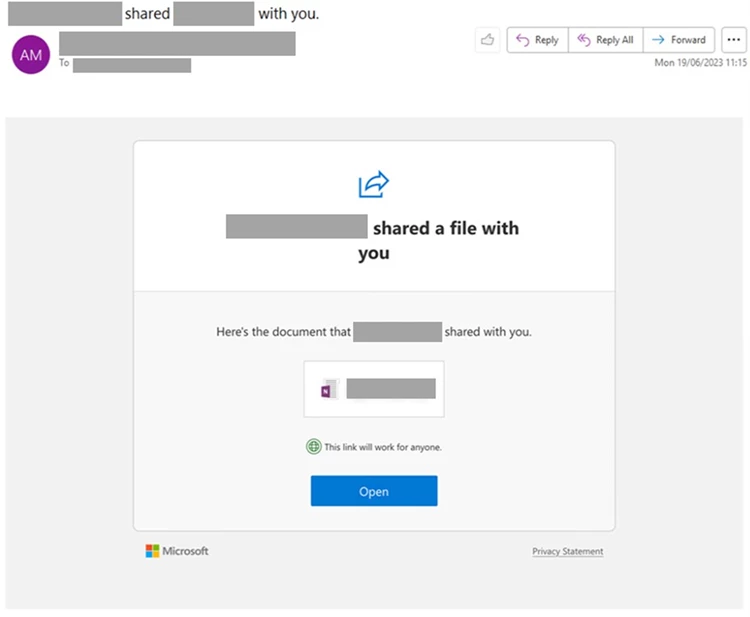
Microsoft has strongly recommended organizations to adopt multifactor authentication (MFA) to reduce the chances of being a victim of OAuth-based attacks. They have also suggested enabling dynamic conditional access policies to keep track of every attempt made by users to sign in to their accounts.
Furthermore, Microsoft has released a set of incident response playbooks that can help security teams audit compromised apps and permissions across an organization. These playbooks are designed to make it easier to analyze and respond to OAuth attacks.



