Hackers Abuse SQL Server Flaw to Breach Azure Cloud VMs

Key Takeaways:
- Microsoft disclosed that hackers have attempted to use a compromised SQL Server instance to breach the Azure cloud platform.
- This security incident underscores the growing challenges in cloud security and highlights the need for robust measures to safeguard sensitive data.
- Microsoft recommends proactive security measures, including the use of advanced tools like Defender for Cloud and Defender for Endpoint, along with strategic practices to fortify Azure against similar attacks.
Microsoft’s security experts have recently discovered a highly sophisticated attempt to target cloud environments. Hackers managed to exploit a compromised SQL Server instance to breach Microsoft’s Azure cloud platform, indicating a concerning evolution in their tactics.
According to the Microsoft Threat Intelligence team, threat actors have previously used this method to target several cloud services, including Kubernetes clusters and virtual machines (VMs). However, this is the first time the method has been used with SQL Server.
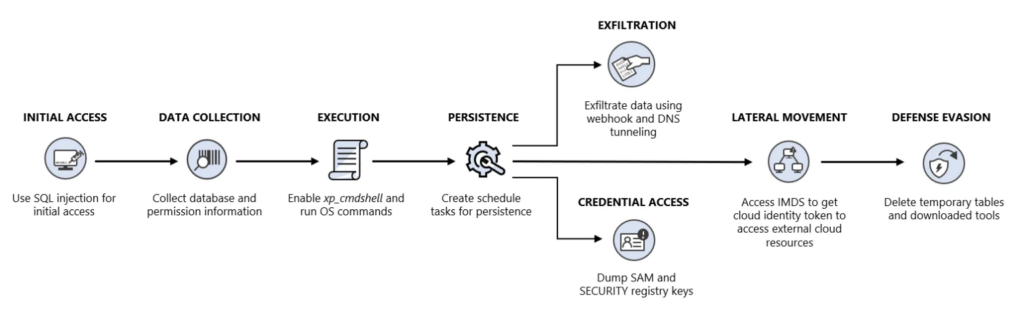
Specifically, the hackers first abused an SQL injection vulnerability in an application on the victim’s machine. It allowed the hackers to access the SQL Server instance deployed in an Azure VM and extract sensitive data. These include details about databases, table names, schemas, database versions, permissions, and network configurations.
Additionally, the threat actors tried to gain access to additional cloud resources in the corporate network. However, Microsoft’s researchers observed that the attackers failed to perform lateral movement due to some errors. The final step involves deleting temporary tables and downloaded tools to remove any traces of the cyberattack.
How to protect Azure cloud against SQL Server attacks
Microsoft mentioned that organizations should use security tools such as Defender for Cloud and Defender for Endpoint to detect SQL injections and other suspicious activities. It’s highly recommended to adhere to the principle of least privileges while granting user permissions within their organization.
“Not properly securing cloud identities can expose SQL Server instances and cloud resources to similar risks. This method provides an opportunity for the attackers to achieve greater impact not only on the SQL Server instances but also on the associated cloud resources,” the Microsoft Threat Intelligence team explained.
Microsoft detailed some security best practices for managed identities to reduce the attack surface and block lateral movement attempts. The company has also detailed some advanced hunting queries for Microsoft 365 Defender and Microsoft Sentinel to track malicious activities within corporate networks.



