
Security researchers have discovered a design flaw in Microsoft Azure. The vulnerability could enable threat actors to get access to storage accounts and gain full control of the environment.
According to Orca Security researchers, the design flaw exists in a mechanism known as Shared Key authorization. Shared Key authorization is enabled by default while creating storage accounts, and it can be exploited easily.
Microsoft claims that Azure automatically generates two 512-bit storage account access keys while setting up a storage account. The access keys, which are utilized for granting data access, have a total length of 512 bits. The data access can be provided either via Shared Key authorization or with SAS tokens signed with the shared key.
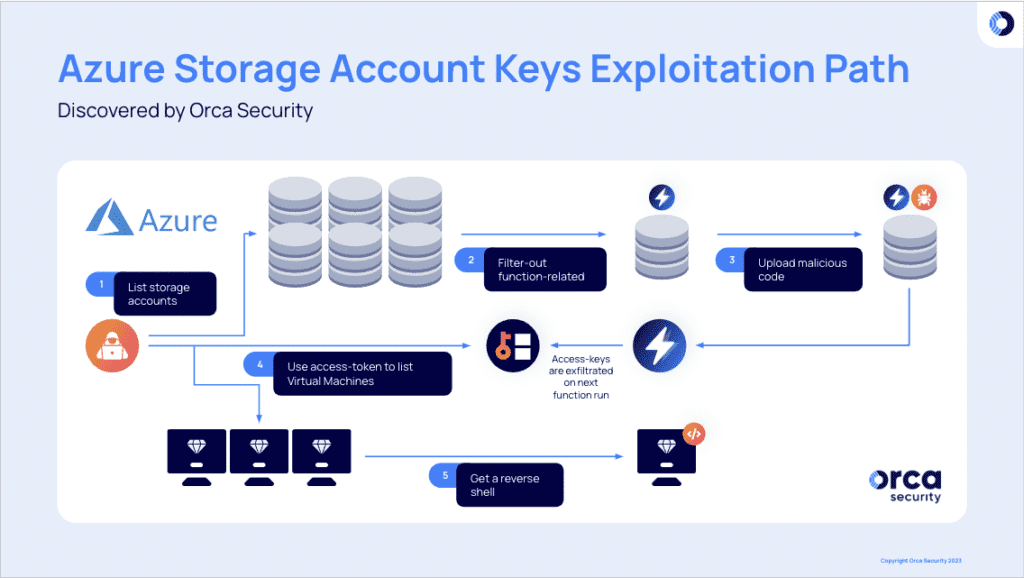
Orca Security found that threat actors could manipulate Azure Functions to steal access tokens of highly privileged identities. This means that a hacker who gains access to the Storage Account Contributor role could potentially access sensitive business assets, and execute remote code (RCE) on virtual machines.
“At this point stealing credentials and Escalating Privileges, as scary as it may sound, is fairly easy. Once an attacker locates the Storage Account of a Function App that is assigned with a strong managed identity, it can run code on its behalf and as a result acquire a subscription privilege escalation (PE),” Orca Security explained.
Microsoft: Shared Key authorization is a “by-design flaw” in Azure Storage accounts
The Microsoft Security Response Center investigated the problem and concluded that it’s a design flaw rather than a security issue. Microsoft recommends that IT admins should disable Azure Shared Key authorization and switch to Azure Active Directory authentication instead.
Microsoft also plans to disable shared access signature authorization by default for new storage accounts. However, there is currently no information available on the timeline for this update. Meanwhile, Microsoft recommends IT admins to learn more about how to use identity-based authorization for Azure Storage accounts.



