Microsoft Streamlines Log Ingestion with New Sentinel AWS S3 Connector

Key Takeaways:
- Microsoft has released the AWS S3 connector for Microsoft Sentinel.
- The new Microsoft Sentinel AWS S3 connector can ingest logs from various AWS services, facilitating monitoring and threat detection across AWS environments.
- Administrators have the flexibility to configure the AWS S3 connector either through a PowerShell script or manually.
Microsoft has announced the general availability of the Amazon Web Services (AWS) S3 connector for Microsoft Sentinel. This new connector allows organizations to ingest service logs from various AWS services directly into Sentinel.
Microsoft Sentinel is a security solution that provides a central hub for monitoring security events, automating responses, and providing insights into security threats. The service collects data from various sources such as on-premises systems, Microsoft Azure, and other platforms. Microsoft Sentinel makes it easier to investigate suspicious activities, identify previously undetected threats, and minimize false positives.
What are AWS Connectors?
AWS connectors allow customers to provide Microsoft Sentinel access to their AWS resource logs. These connectors can be configured to establish a trust relationship between Microsoft Sentinel and Amazon Web Services. Currently, there are two versions of the AWS connector available: the legacy AWS CloudTrail connector and the new AWS S3 connector.
The AWS CloudTrail connector is designed to integrate Amazon Connect with AWS CloudTrail to record Amazon Connect API calls. It logs events related to resource changes and requester details, providing identity insights, continuous monitoring, and governance support.
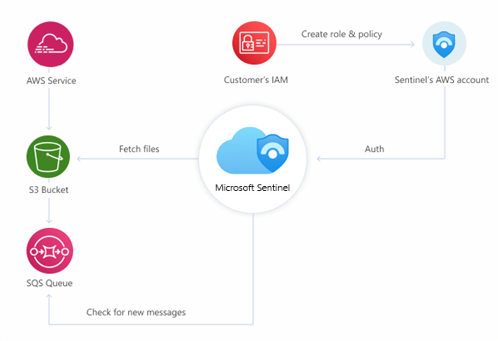
How does the Microsoft Sentinel AWS S3 connector work?
The new Microsoft Sentinel AWS S3 connector can ingest logs from a range of AWS services, such as Amazon Virtual Private Cloud (VPC), Amazon GuardDuty, AWS CloudTrail, and AWS CloudWatch. The AWS service logs are collected in AWS S3 (Simple Storage Service) buckets, which act as secure repositories for storing various types of objects within the AWS Cloud.
Microsoft notes that administrators can choose to either use a PowerShell script or manually configure the AWS S3 connector. We invite you to check out this step-by-step guide to learn more about how to connect to AWS resources to ingest logs into the Microsoft Sentinel solution.


