Microsoft Pulls Azure Cosmos DB Component After Major Security Issue Exposed
It has been revealed that Microsoft pulled a component of its Azure Cosmos DB service earlier this month because of a serious security issue uncovered by researchers at Wiz.io. Dubbed #ChaosDB, the flaw was disclosed to Microsoft on August 12, 2021. It gives any Azure user full access to other customers’ Cosmos DB instances, without any need for additional authorization.
The vulnerability allows malicious actors to perform a remote account takeover of Cosmos DB in the Azure cloud, providing read, write, and delete access to another customer’s database. The Wiz Research Team says:
The vulnerability has a trivial exploit that doesn’t require any previous access to the target environment, and impacts thousands of organizations, including numerous Fortune 500 companies.
What is Cosmos DB and Jupyter Notebook?
Cosmos DB is a non-relational database that’s popular for modern app development. Azure’s fully managed Cosmos DB service provides single-digit millisecond response times and 99.999 percent availability.
Jupyter Notebook is an open-source web app that lets you create and share documents that include live code, equations, and text. Notebooks are used with Cosmos DB to allow developers, data scientists, engineers, and analysts to explore, clean, and transform data. Notebooks can also help with numerical simulations, statistical modeling, data visualization, and machine learning.
Research team dubs flaw ChaosDB
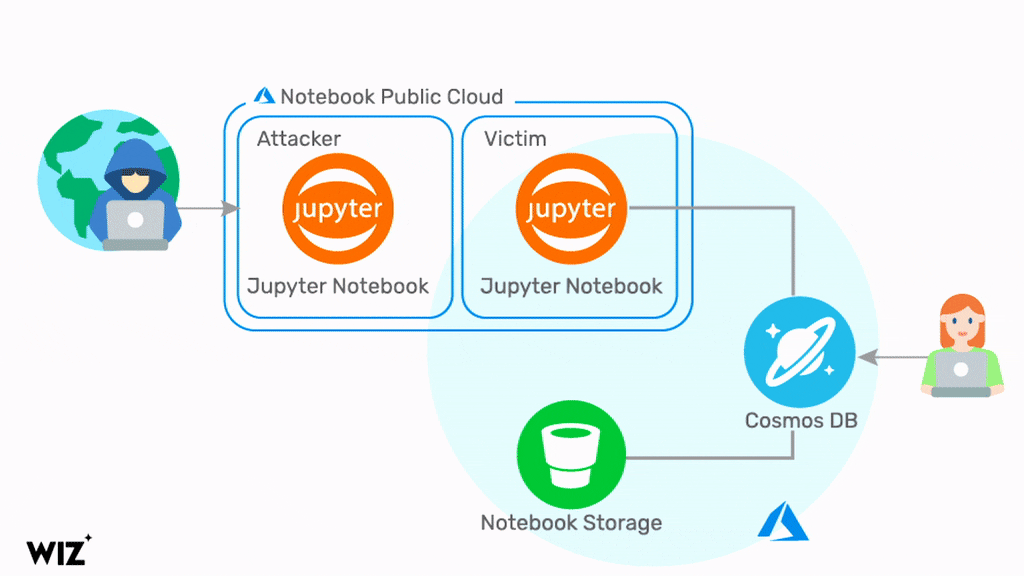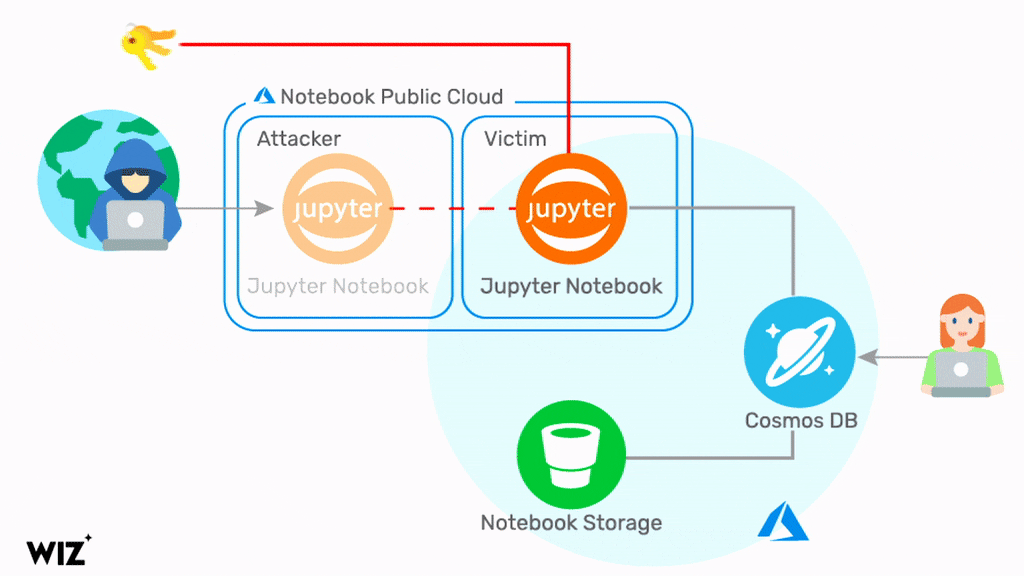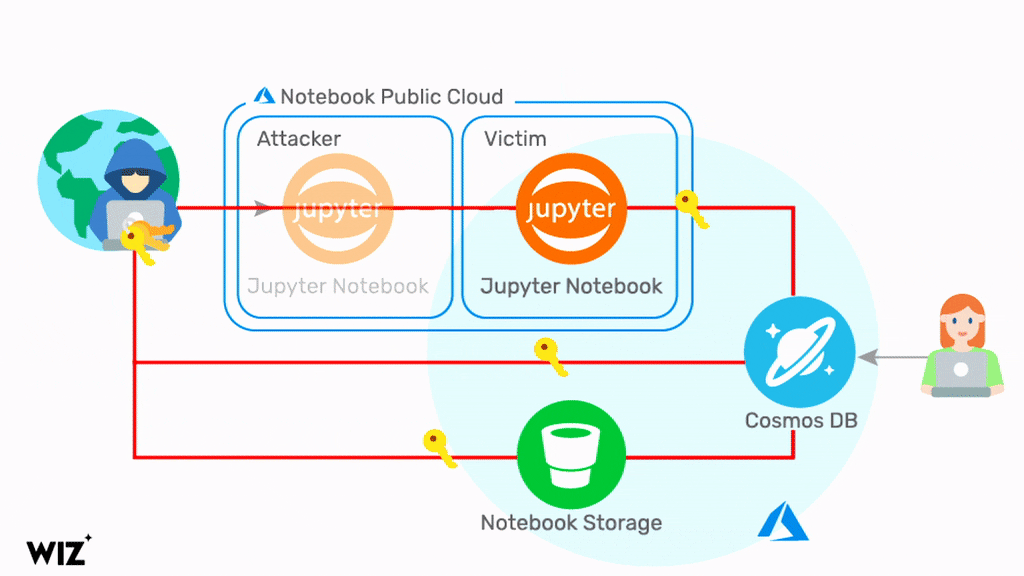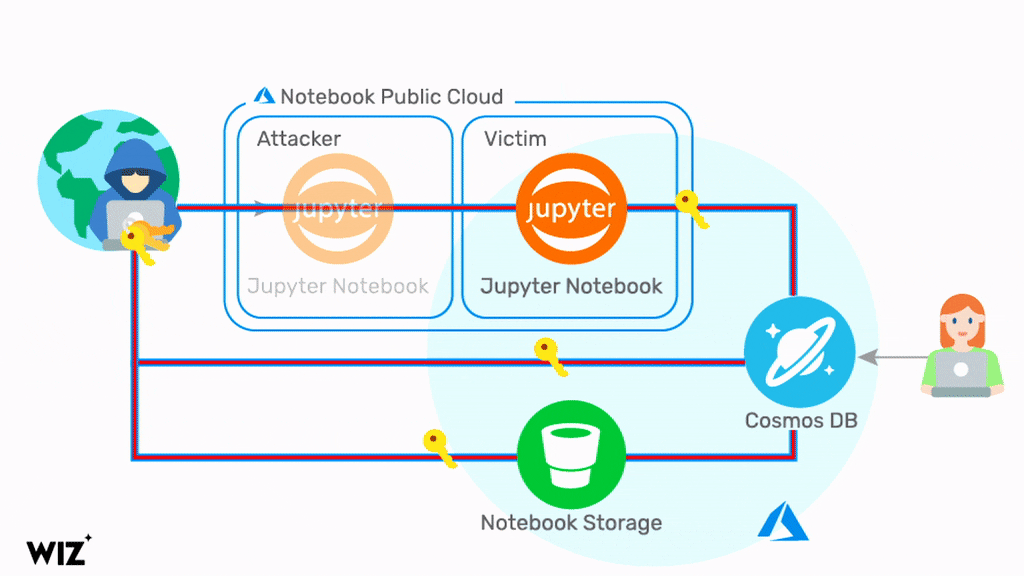
But by exploiting a series of flaws in Jupyter Notebook in Cosmos DB, a hacker could query information about a database through Jupyter Notebook. This let the hacker get credentials to the Cosmos DB account related to the notebook, and several other accounts connected to the notebook, and the database Primary Key. With this information in hand, the hacker could view, change, and delete data in a Cosmos DB via several different methods.
Credit to Microsoft that their security team acted directly to resolve the issue and disabled the Jupyter Notebook feature within 48 hours of the initial report. But because the flaw had been left uncovered for months, customers could still remain vulnerable if their DB Primary Key were exposed. So, Microsoft is encouraging its Azure Cosmos DB customers to regenerate their Cosmos DB Primary Keys.
Microsoft releases statement on ChaosDB
Wiz says that Microsoft notified 30 percent of its customers on August 26. But Wiz believes the number of customers affected could be much higher and recommends all of them follow Microsoft’s advice to regenerate the Primary Keys. Microsoft released a statement on the issue:
“Microsoft has recently become aware of a vulnerability in Azure Cosmos DB that could potentially allow a user to gain access to another customer’s resources by using the account’s primary read-write key. This vulnerability was reported to us in confidence by an external security researcher. Once we became aware of this issue on 12 August 2021, we mitigated the vulnerability immediately.
We have no indication that external entities outside the researcher had access to the primary read-write key associated with your Azure Cosmos DB account(s). In addition, we are not aware of any data access because of this vulnerability. Azure Cosmos DB accounts with a vNET or firewall enabled are protected by additional security mechanisms that prevent risk of unauthorized access. Out of an abundance of caution, we are notifying you to take the following actions as a precautionary measure.”
If you need to regenerate the Primary Key for your Cosmos DB, check out Microsoft’s instructions here.