
Key Takeaways:
- Security researchers have identified three vulnerabilities in the PowerShell Gallery, an online repository for PowerShell code modules, that could be exploited by hackers to upload malicious packages.
- The vulnerabilities could be abused for typosquatting attacks and supply chain attacks.
- Despite being reported to Microsoft by Aqua Nautilus researchers almost a year ago, the vulnerabilities remain unfixed, potentially leaving users exposed to security risks.
Attention all IT Pros! Security researchers have unveiled three design flaws within the PowerShell Gallery, an online platform for distributing PowerShell code modules. These vulnerabilities have the potential to let malicious hackers upload harmful packages onto the repository, introducing risks such as typosquatting and supply chain attacks.
Specifically, researchers at Aqua Nautilus first discovered and reported the security flaws to Microsoft almost a year ago. The company claimed that it had fixed the vulnerabilities in February 2022 and January 2023, respectively. However, the researchers found that these issues still remain unfixed.
The PowerShell Gallery is a popular repository that allows users to find, publish, and share scripts, PowerShell code modules, and state configuration (DCS) resources. The packages available on the registry have been published by legitimate entities (like Microsoft, VMware, and AWS) as well as community members. It’s important to note that more than 10 billion packages have been downloaded from the repository to date.
Aqua discovered that the PowerShell Gallery doesn’t protect users against typosquatting attacks. It’s a social engineering technique that lets hackers trick users into downloading malicious PowerShell modules from public repositories. Typically, the threat actors use names that are similar to legitimate packages available on public repositories.
For instance, Aqua’s researchers created a replica of the popular module called Aztable and named it Az.Table. Interestingly, the package was downloaded by several hosts across different cloud services within a few hours. The researchers warned that malicious actors could abuse the vulnerability to launch a massive attack, compromise cloud services, and target thousands of organizations.
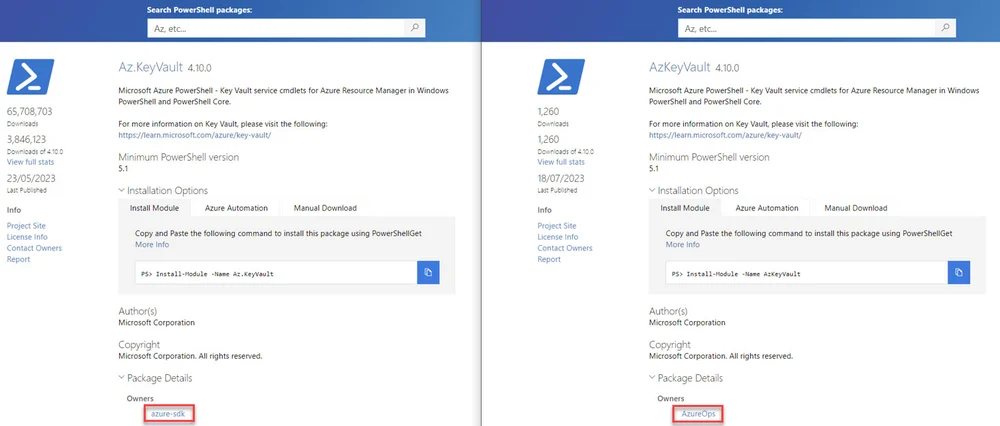
PowerShell Gallery flaw lets hackers spoof the owner’s identity
Additionally, Aqua highlighted another security flaw in the landing pages for PowerShell modules. It enables a hacker to upload a malicious package with fake details, including the author, copyright, and description.
“An attacker can freely choose any name when creating a user in the PowerShell Gallery,” Aqua explained. “Therefore, determining the actual author of a PowerShell module in the PowerShell Gallery poses a challenging task.”
Lastly, the third vulnerability allows threat actors to access unlisted or hidden packages. It could let them steal highly sensitive data associated with the modules for espionage purposes.
Currently, there is no evidence that the security flaws have been exploited to upload malicious packages into the PowerShell Gallery. However, it’s recommended to be careful while using the PowerShell Gallery until Microsoft releases a fix.



