Microsoft Intune Enhances Onboarding Experience for Defender for Endpoint

Key Takeaways:
- The latest Microsoft Intune updates facilitate seamless integration with Defender for Endpoint, simplifying the onboarding process for organizations.
- Administrators gain enhanced capabilities for monitoring and protecting devices against sophisticated threats through centralized management.
- The consolidated dashboard and reporting features offer valuable insights into device security status, enabling proactive measures against potential vulnerabilities.
Microsoft is making some improvements to the way Intune deploys and manages Microsoft Defender for Endpoint on devices. This release enables organizations to use a unified device management service for monitoring and protecting their devices with cloud-based threat detection and response capabilities.
“The single-pane of glass for these capabilities will be Intune. This assures streamlined simplification, and any connections required for on-premises managed Windows assets, like servers, only requires a simple attach configuration joining Intune with Microsoft Configuration Manager for Defender for Endpoint management,” the Microsoft Intune team explained.
According to Microsoft, IT administrators are now able to access both summary and detailed reports about the deployment status of Microsoft Defender for Endpoint across their organizations. Additionally, the new consolidated dashboard-reporting feature offers valuable insights into device signals running Microsoft Defender for Endpoint workloads, such as firewall status, detected malware, and antivirus status. It’s also possible to access additional dashboarding and reporting through the Defender portal.
Additionally, IT admins can easily access quick results on reports and policy enforcement status for all Defender for Endpoint devices along with their current timestamps. The Device Query feature in Intune’s Advanced Analytics also allows users to gain real-time insights into the state and status of Defender for Endpoint devices.
Easily deploy Microsoft Defender for Endpoint
Microsoft notes that customers have the option to use the simplified Defender for Endpoint EDR policy deployment. This feature provides a streamlined approach to deploying a preconfigured policy to all devices within the organization. It’s important to note that Microsoft Defender definition updates leverage the Delivery Optimization capability on Windows 11 and 10 devices, which uses caching and delivery methods to reduce network impact.
Microsoft Defender for Endpoint configuration applies to all Windows client and server machines that are either managed by tenant attach or Configuration Manager. It helps to ensure that Defender for Endpoint can be deployed, configured, and monitored across all Windows devices.
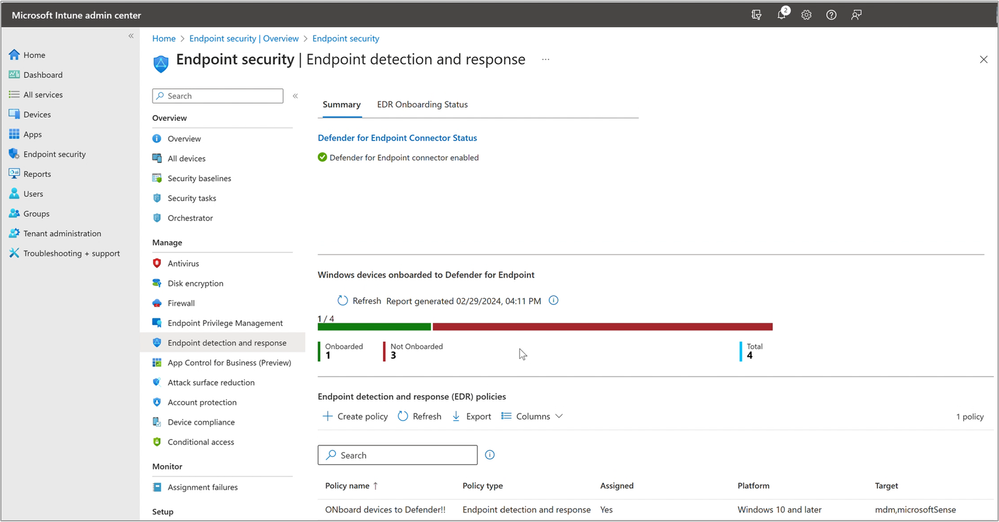
In the Intune admin center, IT admins can monitor devices with Defender for Endpoint EDR installed. To do so, they will need to check the new summary reports found on the Endpoint Security > Endpoint detection and response page. It’s important to note that the tenant Defender for Endpoint connector must be activated to get an overview of the deployment status of Defender for Endpoint EDR on devices across an organization.
Overall, these latest enhancements are poised to streamline the integration of Defender for Endpoint with Microsoft Intune, facilitating a smoother onboarding process for customers. It enables administrators to efficiently monitor and safeguard their devices against increasingly sophisticated cyber threats and improve their organization’s security posture.



