Microsoft Exchange Servers Hit By Stealthy IIS Backdoors

Microsoft has published a security advisory about a new wave of malware attacks that target Exchange Servers. The company has warned IT admins that threat actors are increasingly using malicious Internet Information Services (IIS) modules to install backdoors and steal credentials.
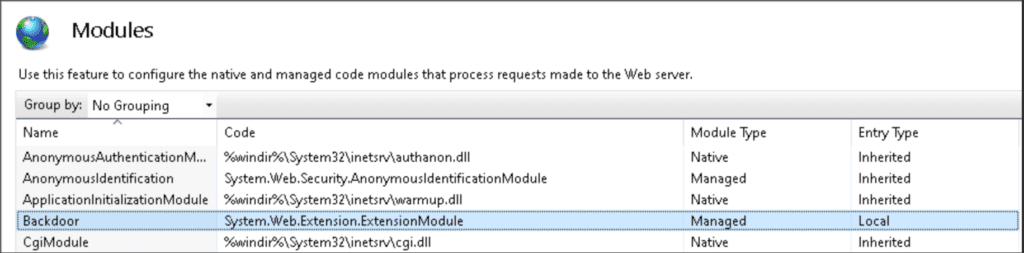
For those unfamiliar, Internet Information Services (IIS) is a web server that lets developers host websites and applications. It has been a core part of Windows for years and can be extended via various add-ons called modules.
IIS modules offer an ideal way to install malicious backdoors into web-facing applications. These attacks typically enable the attacker to abuse a critical vulnerability in the application to deploy a web shell. Once installed, the IIS module lets threat actors to get persistent access to target servers.
In a recent campaign, Microsoft observed that attackers are infecting Exchange servers with customized IIS modules. They managed to run commands, steal credentials, access sensitive data, and deliver additional payloads to the victim’s machines.
“Once registered with the target application, the backdoor can monitor incoming and outgoing requests and perform additional tasks, such as running remote commands or dumping credentials in the background as the user authenticates to the web application,” Microsoft noted.
How to protect Exchange Servers against malicious IIS backdoors
Microsoft says malicious actors will continue to use IIS backdoors in the coming months. It is important that organizations should follow best security practices to protect their servers. The company has provided some insights that can help IT admins to detect and remove malicious IIS modules in enterprise environments.
The Microsoft 365 Defender Research team urges customers to keep their Exchange servers updated and review highly privileged roles and groups. It is also recommended to turn on multi-factor authentication (MFA), analyze config file and bin folder, prioritize alerts, and restrict access to IIS virtual directories.


