Microsoft Entra ID Conditional Access Gets Protected Actions Support to Boost Security

Microsoft has announced that Conditional Access for protected actions support is now generally available for Entra ID (Azure AD) customers. The new security feature enables IT admins to use Conditional Access policies to protect critical administrative operations.
In Microsoft Entra ID (previously known as Azure AD), the Protected Actions feature provides additional protection by assigning Conditional Access policies to specific permissions. The Protected Actions feature helps organizations to reduce the risk of unauthorized access and potential security breaches.
“With Conditional Access for protected actions, organizations can now add an extra layer of protection to these sensitive operations by defining granular policies that specify the conditions under which users can perform protected actions. For example, organizations can require administrators to complete phishing-resistant multi-factor authentication (MFA), use a compliant device, or be in a trusted location before modifying a conditional access policy,” Microsoft explained.
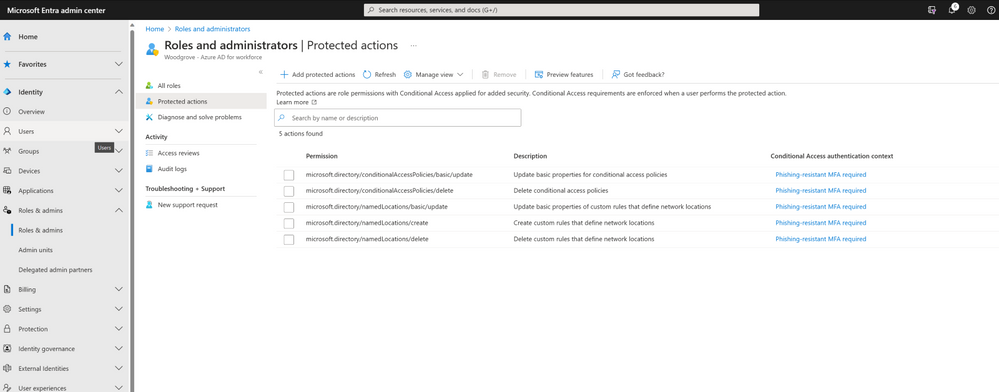
Microsoft Entra ID supports a limited set of protected actions
Currently, protected actions can be applied to a limited set of permissions in Microsoft Entra ID. These include Conditional Access policy management, custom rules that define network locations, and protected action management. Microsoft will continue to listen to customer feedback to expand the set of protected actions, including Cross-tenant access settings management and Microsoft Entra Connect management.
Microsoft highlighted that the new Conditional Access for protected actions support should help organizations to enhance their overall security posture. The feature prevents threat actors from changing federation trust settings, adding credentials to an application, or altering conditional access policies. If you’re interested, you can learn more about protected actions on this support page.


