Microsoft Entra ID to Get Automatic Conditional Access Policies This Month

Key Takeaways:
- Microsoft has unveiled new automatic Conditional Access policies aimed at safeguarding organizations from cyberattacks.
- These policies cover a range of security measures, from requiring multifactor authentication for admin portals to enhanced protection for high-risk sign-ins.
- Microsoft plans to combine machine learning-based policy insights and recommendations with automated policy rollout to boost security.
Microsoft has announced plans to introduce new Conditional Access policies that will automatically protect customers against potential cyberattacks. Starting next week, the company will begin rolling out the new policies to all eligible commercial customers.
“We’ve designed these policies based on our deep knowledge of the current cyberthreat landscape to help our customers strengthen their security baseline, and we’ll adapt them over time to keep the security bar high. These policies are part of a broader initiative to strengthen security, which includes key engineering advances,” said Alex Weinert, Vice President, Identity Security.
Microsoft plans to roll out the following three policies to all eligible tenants:
- Require multifactor authentication for admin portals: This policy requires multifactor authentication (MFA) from administrators when signing into any Microsoft admin portal (like Microsoft 365, Microsoft Entra, Azure, and Exchange). It will be enabled for all eligible Entra ID customers.
- MFA for per-user MFA users: This policy is for existing per-user multifactor authentication customers, and it makes multifactor authentication mandatory for all cloud applications. It’s designed to make it easier for organizations to switch to Conditional Access.
- MFA for high-risk sign-ins: This policy requires multifactor authentication and reauthentication during sign-ins with a high level of risk. It applies to all customers with a Microsoft Entra ID Premium Plan 2 subscription.
Once rolled out, IT admins will be able to find the policies by signing into the Microsoft Entra admin center, and navigating to Protection > Conditional Access > Policies. The new policy view user experience provides detailed information, including a summary, recommended actions, alerts, and policy impact. It’s also possible to leverage sign-in and audit logs to track these policies.
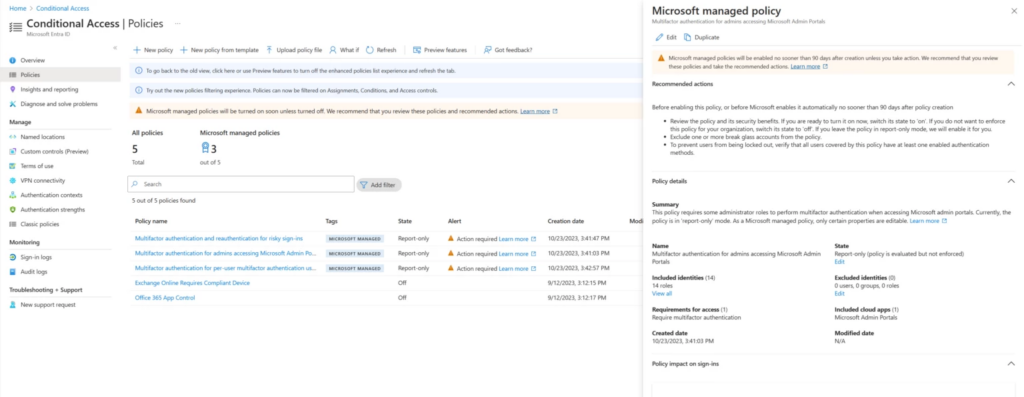
Additionally, IT admins can exclude specific users, roles, and groups from these policies, allowing for exceptions such as emergency and break glass accounts. Microsoft says administrators also have the option to duplicate a policy and customize it to their specific needs, just like any other Conditional Access policy.
IT admins get 90 days to review automatic Conditional Access policies
Microsoft notes that IT Pros will have a 90-day window to review or disable these policies before they become enabled by default. The policies will be in a report-only mode, which will allow Conditional Access to log policy results without enforcing them.
Microsoft plans to gradually enhance these Conditional Access policies to protect organizations against cyber threats. “Our eventual goal is to combine machine learning-based policy insights and recommendations with automated policy rollout to strengthen your security posture on your behalf with the right controls,” Weinert added.


