Microsoft to Enable Automatic Conditional Access Policies for Entra ID Customers

Key Takeaways:
- Microsoft will enable new automatic Conditional Access (CA) policies for Entra ID customers in February and March 2024.
- The current implementation of the policies is in a report-only mode, providing administrators with a crucial 90-day period to thoroughly review and make necessary adjustments to the settings before the policies transition into full enforcement.
- The CA policies address MFA requirements, focusing on Microsoft admin portals, legacy per-user MFA implementation, and mandatory MFA for high-risk sign-ins.
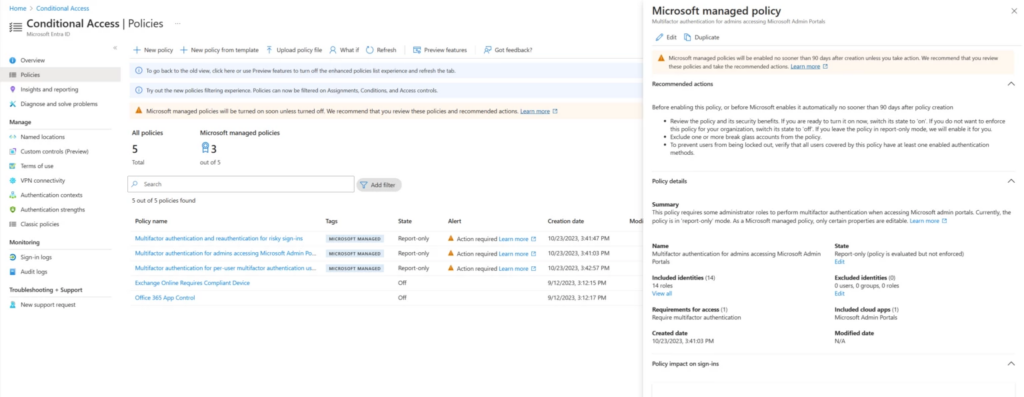
Microsoft announced the automatic rollout of new Conditional Access (CA) policies for select Microsoft 365 licenses in November 2023. As of today, these policies are only available in report-only mode, with the activation for commercial customers set for February and March 2024.
The report-only mode enables policies to log policy results without enforcing them. Microsoft says administrators had 90 days to review and, if necessary, change or opt out of the CA policies before they became automatically enabled for all organizations. These policies are in place for Microsoft 365 E3 and E5, as well as Microsoft 365 Business Premium subscribers.
Microsoft explained that the first policy requires IT admins to complete MFA when signing Microsoft admin portals like Microsoft 365 admin center, Azure, and Exchange admin center. It applies to Entra ID Premium Plans 1 and 2. The second policy is aimed at customers who are still using the legacy per-user multifactor authentication implementation. According to this policy, MFA is mandatory for accessing all cloud applications.
The third policy mandates the use of multi-factor authentication and re-authentication during high-risk sign-ins. This policy only applies to commercial customers who are on the Microsoft Entra ID Premium Plan 2. Going forward, Microsoft plans to customize the policies for organizations by combining machine learning-based policy recommendations with automated policy rollout. However, it is unclear when this feature will be available for enterprise customers.
“Customers may not be in a position to disable legacy authentication for certain accounts (a requirement for security defaults), or they may need to make exceptions for certain automation cases. Conditional Access does a great job here, but often customers aren’t sure where to start. They’ve told us they want a clear policy recommendation that’s easy to deploy but still customizable to their specific needs,” Microsoft explained.
Microsoft’s automatic Conditional Access policies tackle low MFA adoption
Currently, only 37 percent of customers use Multi-Factor Authentication (MFA). However, the number of newer Entra ID tenants adopting this security measure is significantly higher. The automatic roll-out of Conditional Access policies is part of Microsoft’s efforts to increase MFA adoption among all commercial customers.
According to Microsoft’s research, multi-factor authentication (MFA) can significantly reduce the risk of account takeover and phishing attacks by over 99 percent. The feature requires users to provide multiple forms of authentication before accessing an account or system. Customers who enable security defaults experience 80 percent fewer hacks compared to those who don’t implement such security measures.



