
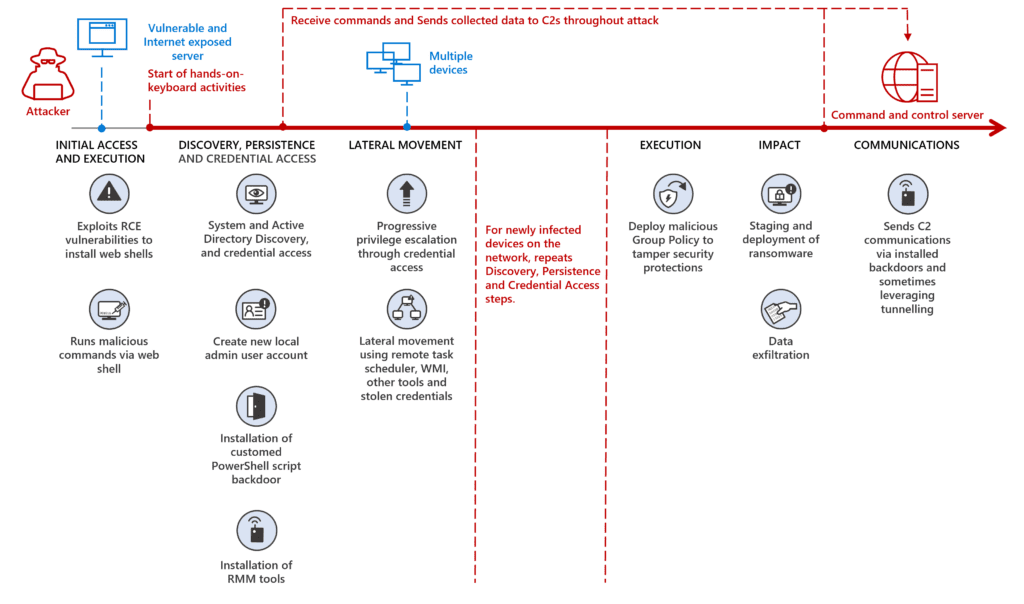
Microsoft has warned that an Iranian state-backed threat actor dubbed Mercury has been carrying out destructive attacks in hybrid environments. The Microsoft Threat Intelligence team has found that the attackers teamed up with another hacking group code-named DEV-1084 to target both on-premises and cloud customers.
According to Microsoft, Mercury first exploited the log4j vulnerability to gain initial access to the system. The threat actors established persistence and then moved laterally throughout the enterprise network. Once done, Mercury handed out network access to the DEV-1084 group that launched two separate attacks against on-premises resources and Microsoft Azure.
Specifically, the threat actor leveraged Group Policy Objects (GPO) to interfere with the security tools and distribute ransomware in the NETLOGON shares on Active Directory domain controllers (DCs).
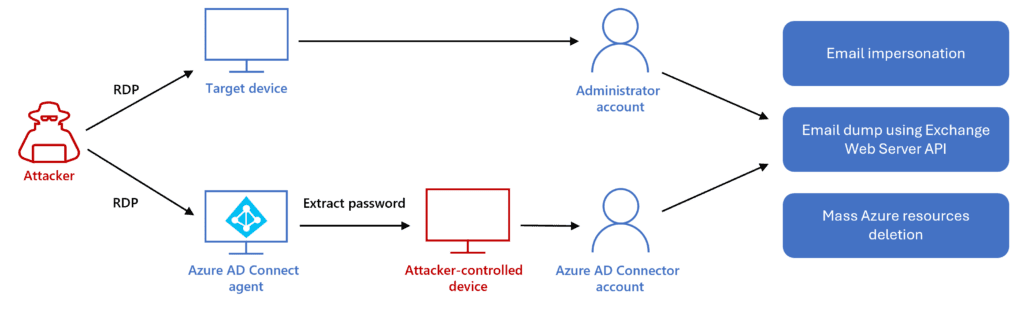
Additionally, the hacking group used the AADInternals tool to harvest credentials for the Azure AD Connector account. They also used RDP to compromise another Global Administrator account and bypass MFA.
“Azure AD Connector account and the compromised administrator account were then used to perform significant destruction of the Azure environment—deleting within a few hours server farms, virtual machines, storage accounts, and virtual networks. We assess that the attacker’s goal was to cause data loss and a denial of service (DoS) of the target’s services,” the Microsoft Threat Intelligence team explained.
How to block destructive attacks in on-prem and Azure AD environments
Microsoft has detailed a couple of recommendations to protect organizations against similar attacks. Customers should enable Tamper protection features in Microsoft Defender for Endpoint to prevent misconfigurations in antivirus solutions. Secondly, IT admins should review global admin permissions in their Microsoft 365 environment.
Furthermore, Microsoft suggests enforcing Conditional Access policies (like trusted IP address and device compliance). It’s highly recommended to enable continuous access evaluation (CAE) to block access to compromised accounts to mitigate cyberattacks. Microsoft says that administrators should also keep an eye on any unusual activities on the Azure AD connector and AD DS connector accounts.



