
Key takeaways:
- Microsoft Defender for Endpoint adds device tagging support in public preview for mobile devices.
- The feature allows IT admins to label and categorize iOS and Android devices during onboarding.
- These tags can be used to group devices by location, which should be helpful for administrators working across various geographical areas.
Microsoft Defender for Endpoint has introduced device tagging support in public preview for mobile devices. This capability allows IT admins to tag iOS and Android devices during the onboarding process.
Microsoft highlighted that tags enable administrators to label and classify devices in enterprise environments. The feature is designed to enhance searching and organization capabilities and streamlines the process of assigning rules to specific categories or groups.
“In today’s reality where SOC analysts are decentralized across multiple geographical locations, this capability helps admins designate and group devices by location while ensuring that the correct role-based access control permissions are assigned to the SOC analysts responsible for that location. Tags are unique keywords set by admins to be assigned to particular devices. Admins then create device groups based on these tags,” Microsoft explained.
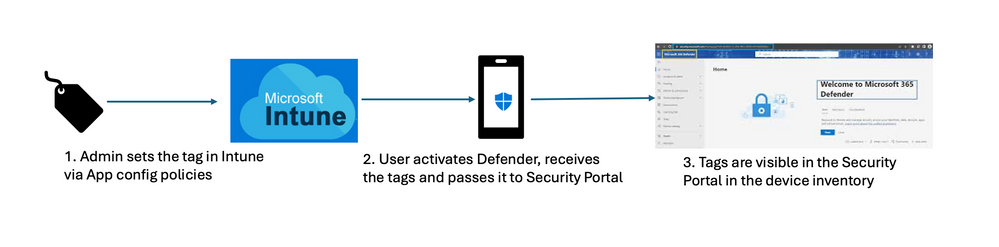
According to Microsoft, the process to assign tags to Android and iOS devices is pretty straightforward. Specifically, IT admins can use configuration policies to configure the device tags through Microsoft Intune and then add them to mobile devices. Once installed, the Microsoft Defender app passes the tags to the Security Portal. These device tags are visible in the device inventory against onboarded devices.
Microsoft notes that IT admins will need to keep the Defender app open to sync the tags with Microsoft Intune and Security Portal. However, administrators may need to wait for upto 18 hours for tags to be visible in the portal.
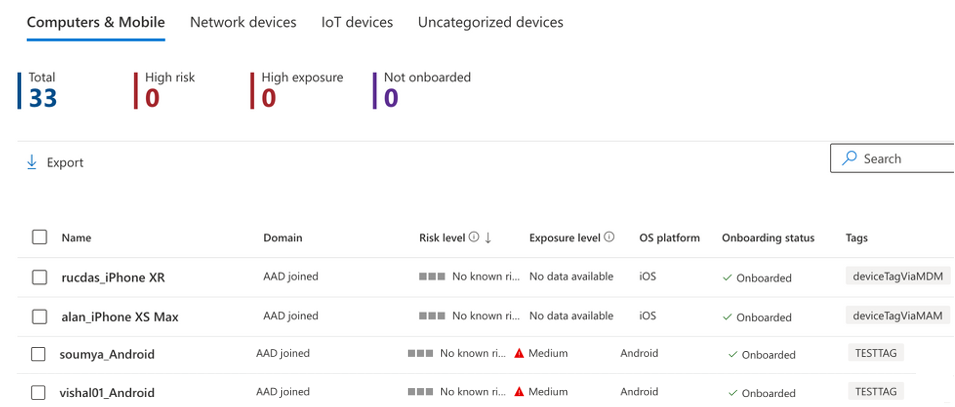
Mobile device tagging feature available in preview
As of this writing, the device tagging feature is available in public preview for Microsoft Defender for Endpoint customers. This capability should help organizations to enhance their cybersecurity posture and boost protection for corporate data shared on mobile devices.
Earlier this year, Microsoft Defender for Endpoint added a new feature that lets IT admins discover internet-facing devices. This update was aimed at helping IT admins to detect and remediate critical vulnerabilities in corporate networks.


