
Key Takeaways:
- Microsoft has introduced a Terraform module aimed at simplifying the onboarding process for Microsoft Defender for Cloud (MDC).
- It facilitates the configuration of MDC plans for subscriptions or management groups using just a few lines of code.
- The new Terraform module eliminates the need to engage with multiple Microsoft Defender for Cloud ARM APIs.
Microsoft has introduced a new Terraform module aimed at simplifying the onboarding process for Microsoft Defender for Cloud (MDC). This module enables organizations to configure MDC plans for their subscriptions or management groups using a minimal amount of code.
Microsoft Defender for Cloud is a security solution that allows customers to protect cloud-based applications against various cyber threats and vulnerabilities. It provides tools to enhance cloud security posture, mitigate cyber-attacks, and streamline security management.
Previously, security teams had to engage with multiple Microsoft Defender for Cloud ARM APIs to onboard the service successfully. The new Terraform module provides a portal-like experience, making it easier to onboard single, multiple, or all subscriptions. Additionally, the module helps to onboard MDC plans for all subscriptions within a specific management group.
“The module is specifically designed to streamline the onboarding process, providing a new and improved onboarding experience with Terraform. This module is easy to use and supports configuration at both the subscription and tenant levels. It enables customers to verify that their security posture is running the correct Defender for Cloud plans, simplifying the process and providing additional oversight over securing their entire environment,” Microsoft explained.
Getting started with the new Microsoft Defender for Cloud Terraform module
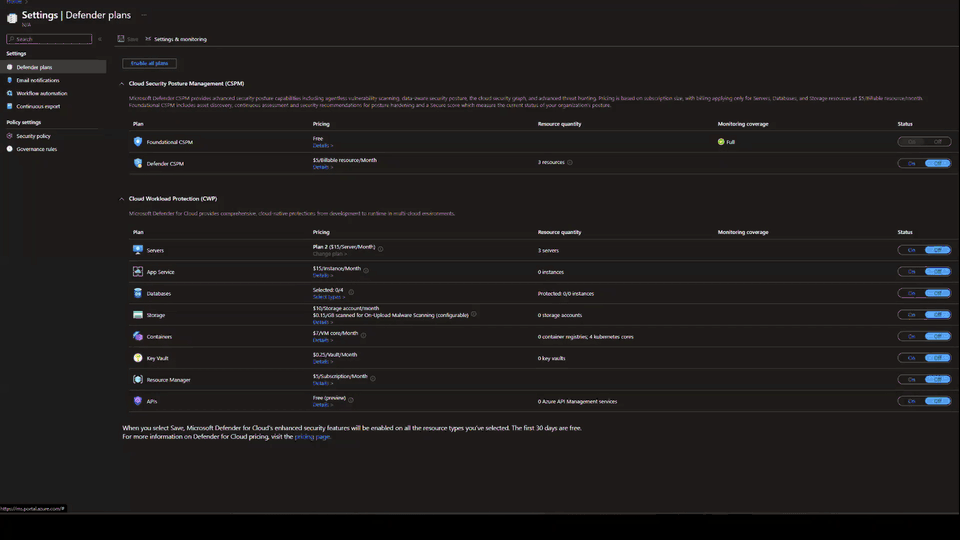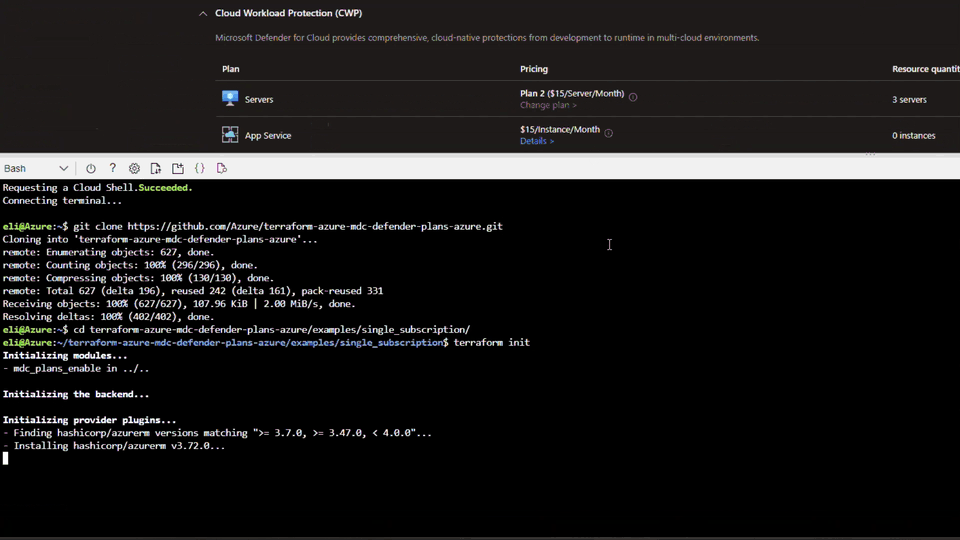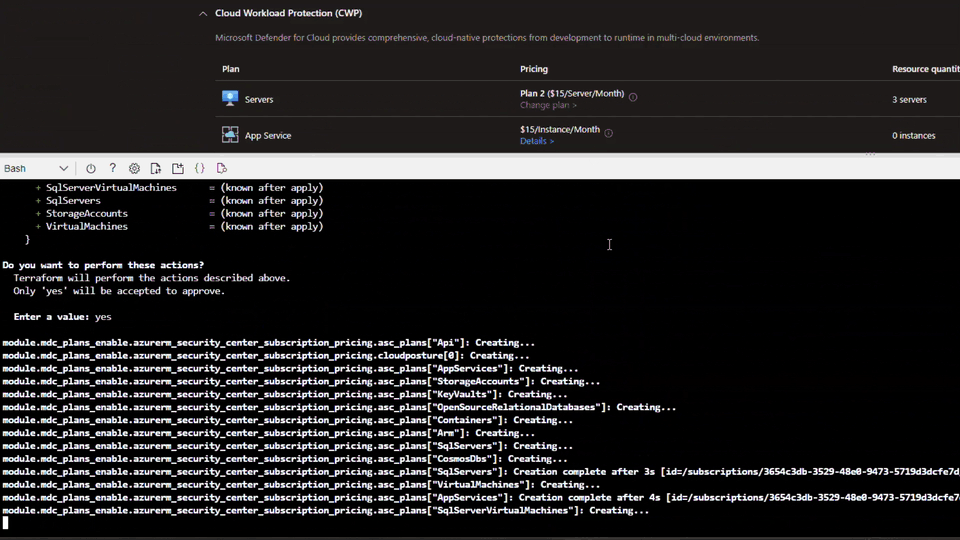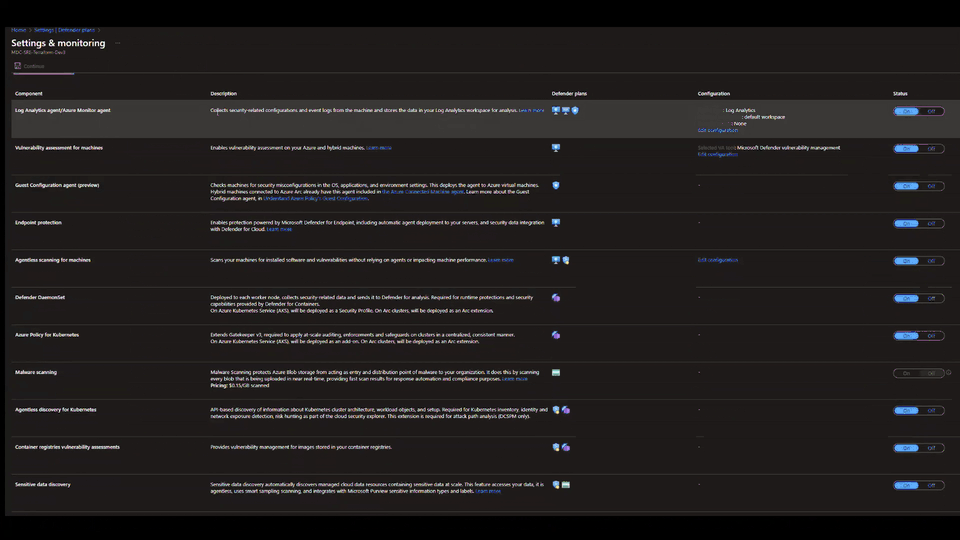
Microsoft notes that customers should have the Terraform core’s version 1.3 (or higher) and Terraform Provider for Azure (AzureRM) version v3.x. To get started, follow the steps listed below:
- Use the service principal’s credentials to configure Terraform for Azure.
- Navigate to the examples directory and select the onboarding type for implementation: Single Subscription, Chosen Subscriptions, All Subscriptions, or Management Group.
- Now, run the terraform apply command within the folder.
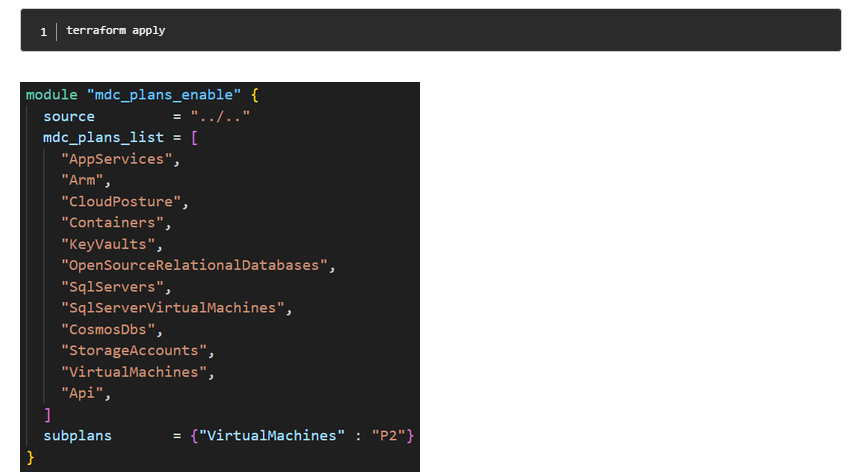
- If you have more specific requirements, you can modify the main.tf file in the output directory and then run the “terraform apply” command again.
According to Microsoft, IT administrators can use the “terraform destroy” command to reverse the onboarding process. Additionally, it’s possible to customize the “mdc_plans_list” variable in order to disable specific plans.
Microsoft has recently announced several new capabilities for Defender for Cloud to help organizations improve their security posture across multi-cloud environments. The new Security Copilot integration enables IT admins to use natural language commands to identify risks and vulnerabilities. There are some new features to allow proactive attack path analysis across clouds.



