
Key Takeaways:
- Microsoft has discovered four security vulnerabilities in the Perforce Helix Core Server.
- The highest severity vulnerability (CVE-2023-45849) could be exploited by remote attackers to execute code from the LocalSystem account.
- Microsoft urges organizations to update to the patched version of Perforce Server immediately.
Microsoft has recently disclosed four vulnerabilities in the Perforce Helix Core Server. These security flaws could enable threat actors to remotely execute commands in order to gain privileged access to the local Windows systems.
The Perforce Helix Core Server (also known as Perforce Server) is a version control system that helps software development teams manage and track changes to source code. It allows multiple users to work on the same project simultaneously. Perforce Server is used to manage the software development life cycle across various industries such as technology, military, government, gaming, and retail.
In August 2023, Microsoft reported four security vulnerabilities in the Perforce Helix Core Server. These vulnerabilities allow hackers to carry out malicious activities, such as denial-of-service (DoS) and remote code execution (RCE) attacks.
The first vulnerability (tracked as CVE-2023-45849) has a high severity rating of 9.0 out of 10 on the CVSS. Remote attackers can exploit this flaw to execute code from the LocalSystem account. LocalSystem is a highly privileged account used by Windows services and system processes to access resources on the local system without requiring specific user credentials.
Microsoft warned that the vulnerability lets malicious actors gain full control over a system running a vulnerable version of the Perforce Server. “An attacker with system-level remote code execution access to a source code management platform can insert backdoors into software products, exfiltrate source code, and other intellectual property, and pivot to other sensitive enterprise infrastructure,” Microsoft explained.
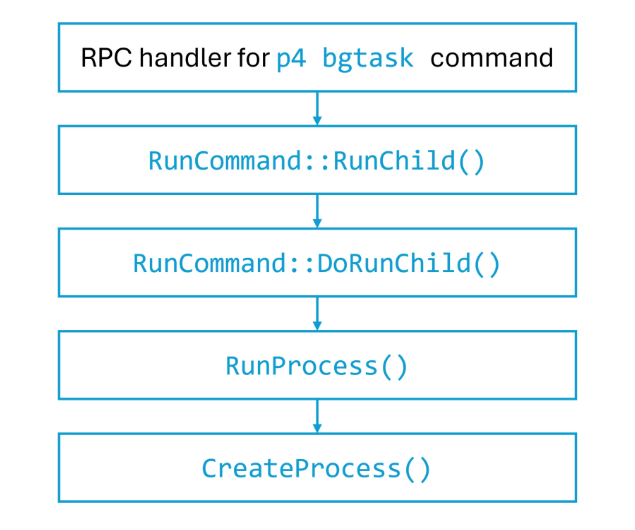
Microsoft notes that the other three security flaws (tracked as CVE-2023-5759, CVE-2023-35767, and CVE-2023-45319) received a CVSS score of 7.5. The vulnerabilities could let unauthenticated attackers launch denial-of-service attacks remotely.
Fortunately, Perforce released new security updates to patch the vulnerabilities in early November. Microsoft advises that organizations should update to version 2023.1/2513900 of Perforce Server to protect their systems against cyberattacks.
Microsoft’s recommendations to protect Perforce Servers
Microsoft recommends that enterprise customers should apply security patches for Perforce Server any other products. They should also use a VPN to limit communication with the Perforce Server. Organizations should issue TLS certificates to verified Perforce users and use a TLS termination proxy in front of the Perforce Server to validate client TLS certificates.
Last but not least, Microsoft suggests that enterprise administrators keep a log of all access to their Perforce Server through network appliances and the server itself. Additionally, organizations can configure alerts to inform IT admins and security teams of Perforce Server process crashes.


