
Microsoft has warned that threat actors are increasingly using business email compromise campaigns to target enterprise customers. The company has found that it could be challenging for the victims to identify and mitigate the attacks on time.
Business email compromise (BEC) is a type of cyberattack that lets hackers use phishing emails to request payments or gain access to sensitive information. The threat actor impersonates a trusted individual (like an executive or customer) to convince the target to take a specific action. The FBI 2021 Internet Crime Report revealed that BEC attacks increased by 65 percent from July 2019 to December 2021.
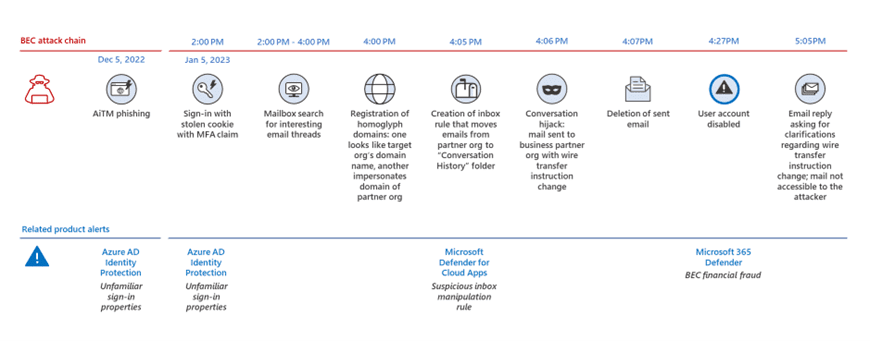
Microsoft explained that the attacker used a phishing technique called adversary-in-the-middle (AiTM) to get the session cookie and bypass multi-factor authentication (MFA). They signed in to the target account and spent two hours searching for email threads to hijack. The next step involves using homoglyph characters to register deceptive domains similar to the legitimate website.
The cybercriminals made a rule to move and hide emails in a different folder. They also emailed the business partner and asked them to send money to an account they owned. After that, the threat actors deleted the email so the compromised user wouldn’t notice. Microsoft says that its Microsoft 365 Defender alerted about the BEC attacks around 20 minutes after the email was deleted from the mailbox. The solution disabled the compromised account to mitigate the cyberattack.
Microsoft 365 Defender disrupted 38 BEC attacks
Microsoft highlighted that the tool uses AI-based detection capabilities to mitigate 38 BEC attacks targeting 38 enterprise customers. “In our testing and evaluation of BEC detections and actions in customer environments faced with real-world attack scenarios, dozens of organizations were better protected when accounts were automatically disabled by Microsoft 365 Defender,” Microsoft explained.
If you’re interested, you can learn more about the BEC attack disruption capabilities available in Microsoft 365 Defender in our previous post.



