Microsoft Azure Sentinel gets SAP Support, Plus UEBA and Entity Pages Reach GA
Last week Microsoft announced improvements to its cloud-native SIEM product, Azure Sentinel. In an effort to make Sentinel more efficient for Security Operations (SecOps) teams, Microsoft has improved the quality of rules and includes more innate intelligence out-of-the-box. There’s also built-in support for SAP in preview. Plus, other features like UEBA and entity pages, which were previously in preview, have now reached general availability.
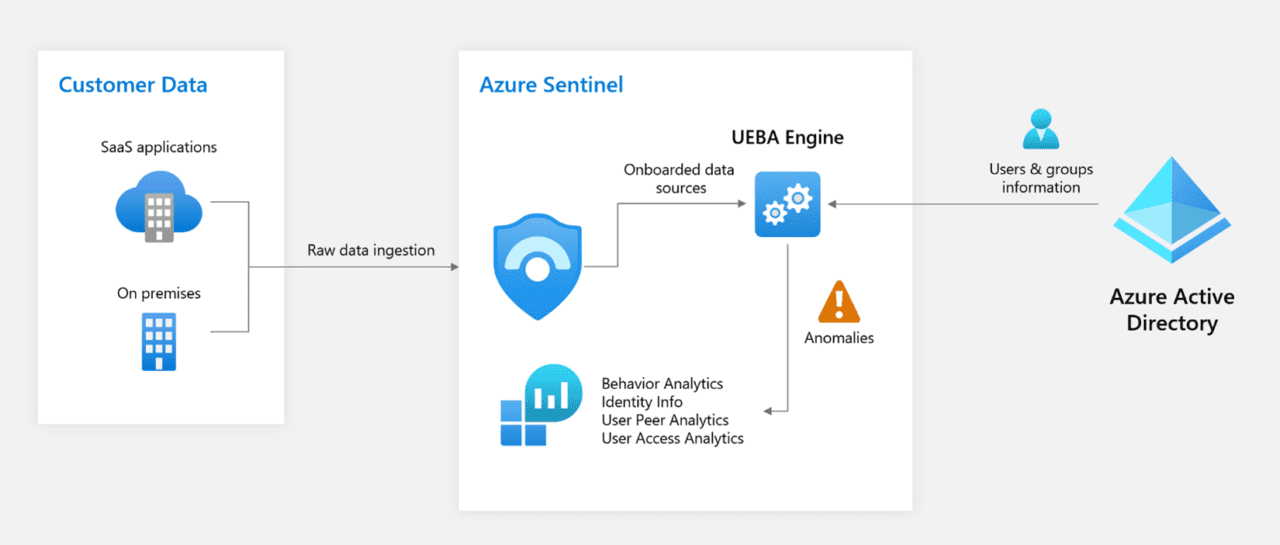
User and Entity Behavior Analytics (UEBA) general availability
At Ignite in September last year, Microsoft announced the availability of User and Entity Behavior Analytics (UEBA) in preview for Azure Sentinel. Starting May 11th, 2021, UEBA is generally available in Azure Sentinel in all regions. UEBA takes user data from Azure Active Directory (AD), and combined with logs and alerts from connected data sources, it builds baseline behavioral profiles for entities like Azure AD users, hosts, IP addresses, and applications.
UEBA uses behavior analytics and machine learning to identify unusual activity and help SecOps identify whether there is a compromised entity or a malicious insider. Microsoft says that additionally, UEBA can work out the relative sensitivity of your assets, peer groups of assets, and tell you the possible impact if a given asset gets compromised. Microsoft calls this an asset’s ‘blast radius’. With the extra information that UEBA provides, SecOps can better prioritize investigation and incident response.
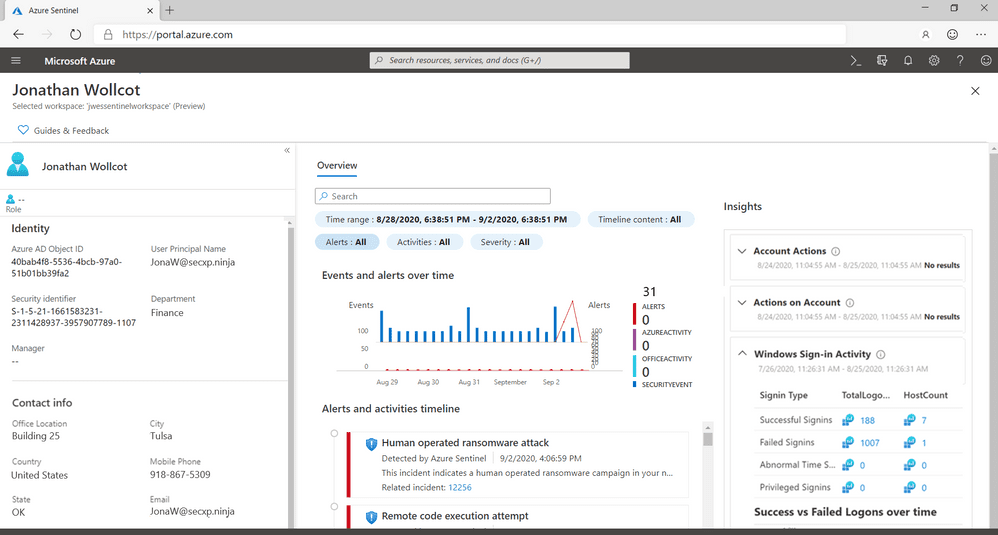
Azure Sentinel entity pages
Also reaching general availability, entity pages provide SecOps with a datasheet of useful information about users or hosts. IP address entities are currently in preview. Entity pages are made up of three sections. The left panel contains the entity’s identifying information from sources like Azure Active Directory (Azure AD), Azure Monitor, Azure Defender, CEF/Syslog, and Microsoft 365 Defender. The center panel shows a graphical and textual timeline of notable events, like alerts, bookmarks, and activities. And the right panel displays behavioral insights.
Improved machine learning
Sentinel uses a technology called fusion to correlate events into ‘incidents’ using machine learning. Microsoft says that incidents have a much higher fidelity than individual events because they are correlated together and can help map out an entire attacker kill chain. SecOps can use incidents to prioritize work in Sentinel and focus on what might really pose a threat to organizations. When incidents are closed in Sentinel, staff are asked if they were useful so that Microsoft can continue to improve the machine learning model.
Microsoft says that its customers have reported Sentinel incidents as useful in more than 90% of cases. And George Mudie, CISO of ASOS, says that since moving from a traditional SIEM solution implemented in its data centers to Azure Sentinel, it has been able to reduce the time analysts spend on security incidents by 50%. Mudie also says that Azure Sentinel is easy to get started with because there’s no model to train. The machine learning capabilities just work out-of-the-box.
Azure Sentinel Solutions and SAP support
In an attempt to get non-Microsoft systems onboarded faster to Sentinel, the Azure Sentinel Solutions marketplace, currently in preview, provides 32 solutions that let organizations onboard systems to Azure Sentinel without having to set up individual connectors. Some of the currently available solutions for Sentinel include Cloudflare, Palo Alto Prisma, and RiskIQ. You can check out the solutions catalog here.
Along with this announcement, Microsoft is unveiling SAP support for Sentinel. Currently in preview, it’s now possible to send SAP logs to Sentinel. A lot of customers believe that Microsoft only has products that secure its own solutions. But it’s worth remembering that Microsoft provides security for solutions from a range of different vendors, including Amazon, Google Cloud, and Kubernetes.
Two other Azure features enter preview this month, including Microsoft Teams integration and anomaly detection. You can find out more about anomaly detection here and Microsoft Teams integration here.