
Microsoft has introduced a new Azure Active Directory Identity Protection alerts feature in Microsoft 365 Defender. The feature is designed to help organizations prevent threat actors from gaining unauthorized access to enterprise networks via compromised accounts.
With this release, IT admins can now configure policies to trigger Identity Protection alerts when one or more user accounts appear to have been compromised. The feature takes into account the behavior, location, and other factors to generate an alarm. This capability should be useful in blocking suspicious activities.
“Identity Protection alerts are now correlated into related incidents along with alerts from the other security domains, and can be reviewed directly in Microsoft 365 Defender for a full view of the end-to-end attack. No need to switch portals! This helps drive efficiency and simplicity for security teams investigating incidents to understand the full scope of the attacker’s activity and take action in one place,” the company explained.
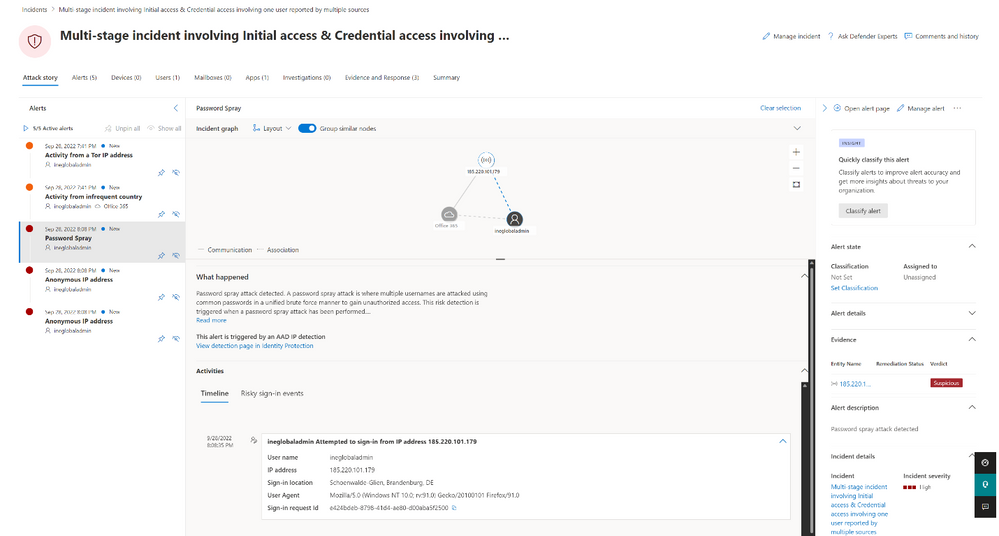
Microsoft notes that Identity Protection alerts leverage “trillions of detection signals” to find compromised Azure AD accounts. The feature can trigger warnings for leaked credentials, anonymous IP address & locations, suspicious sign-in attempts, and more. Security teams can investigate these alerts to detect the root cause, identify compromised accounts and mitigate security risks.
Identity Protection alerts could detect high-profile attacks
Microsoft claims that the Azure AD Identity Protection alerts feature is designed to help organizations protect their users from high-profile attacks such as the Nobelium case. The company detailed an example where the hacking group managed to get into an on-premises network and compromise accounts with permissions to the AD Federation Services. The attackers were able to access users’ mailboxes and read sensitive information.
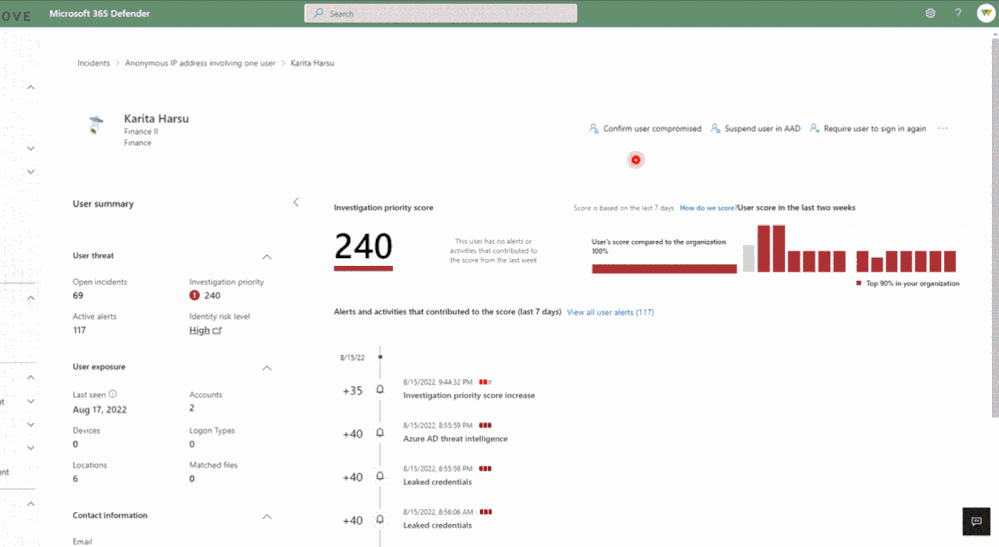
The Azure AD Identity Protection alerts feature is available in Microsoft 365 Defender and via the Microsoft 365 Defender Incident API. It’s also possible to monitor suspicious incidents in Microsoft Sentinel and other security solutions. The feature is configured by default to show alerts for highly suspicious activities that might need attention. However, IT admins can head to the Microsoft 365 Defender setting page to show or disable all types of alerts.



