Manage and Audit Windows and Linux Servers Using Azure Arc

One of the biggest announcements at this year’s Microsoft Ignite conference in November was about Azure Arc, a new service that allows organizations to extend the reach of Azure to other cloud providers, the edge, and on-premise devices. Azure Arc is currently in public preview and at this early stage, it lets you manage Windows and Linux servers, and deploy Azure SQL Database and Azure Database for PostgreSQL Hyperscale on any Kubernetes cluster regardless of where it is physically located.
But Microsoft is planning to expand the range of Azure services that are supported by Arc in the future.
In this article, I’m going to look specifically at managing Windows and Linux servers with Azure Arc. Once a Windows or Linux server is connected to Arc, you can monitor logs, control who gets access to the Azure resource using Role-Based Access Control (RBAC), and audit configuration settings using Azure Policy Guest Configuration. While Azure Arc is new, some of the features here, like log collection, cross over with Azure Sentinel and Azure Security Center.
Sentinel is Microsoft’s Cloud-Native Security Information and Event Management (SIEM) service. Here are a couple of Petri articles where you can find out more about Azure Sentinel:
Azure Sentinel, Microsoft’s Cloud-Native SIEM Solution, Is Now Generally Available
Monitor Windows Server Security Using Azure Sentinel Part 1 – Set Up a Workspace and Data Connector
How to connect servers to Azure Arc
I’m not going to provide complete instructions here at this time. Partly because Arc is in an early preview stage and secondly you are guided through the few simple steps required to connect servers to Arc in the Azure management portal. To access Arc from the management portal, just type arc in the search box and then click Azure Arc in the list of results. From the Azure Arc page, you can manage servers, Kubernetes apps, and run Azure data services anywhere.
During preview, you will need to sign up for each of these services separately but if you are interested in just managing servers, you can sign up for the preview during the server onboarding process by simply checking the necessary box.
Adding a new server to Arc is as simple as clicking + Add and then following the instructions to generate a script that will install the required agent on the remote server. During the script generation process, there are also options to specify proxy server settings and add tags. I downloaded the generated script and ran it in Windows Server 2019. At the time of writing, Arc supports Windows Server 2012 R2 and later, and Ubuntu 16.04 and 18.04.
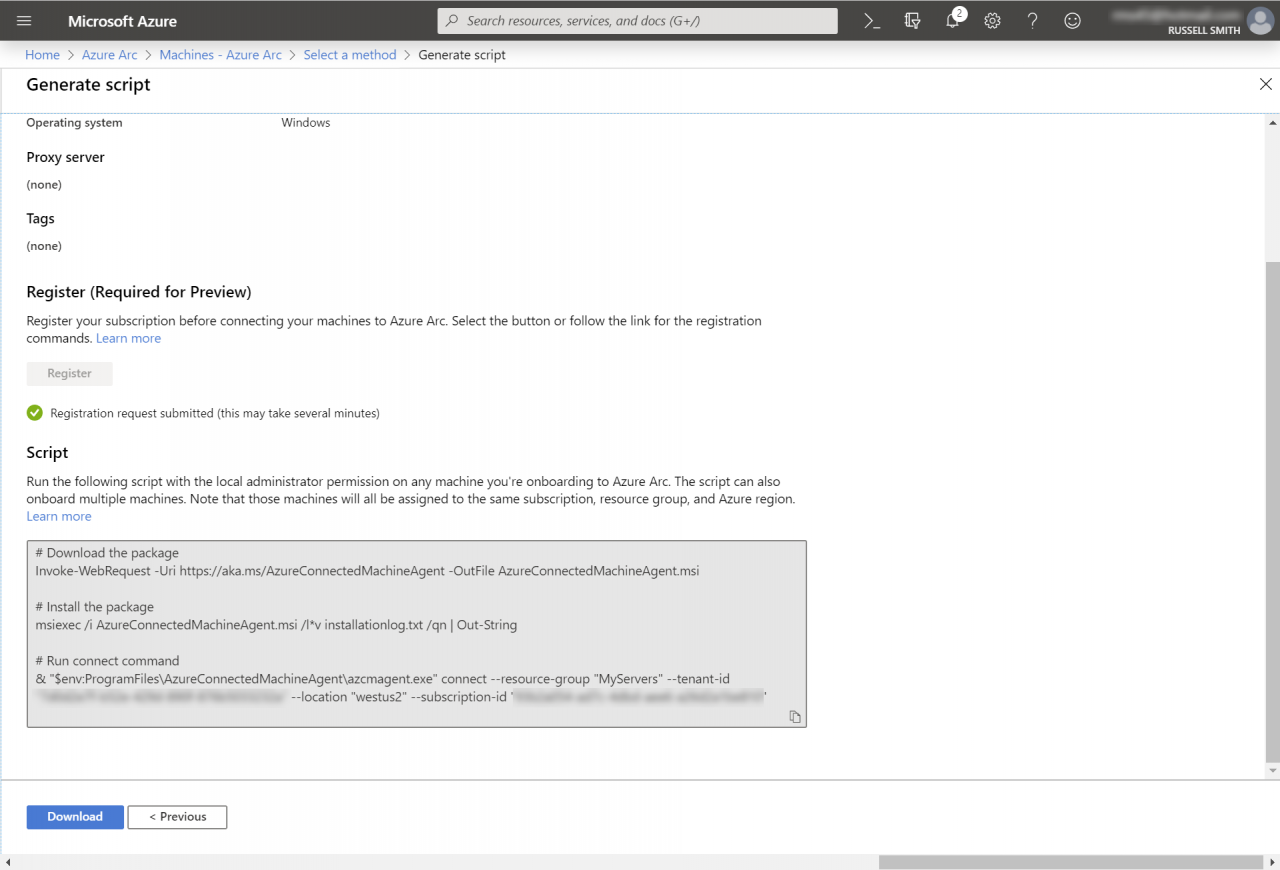
The script is divided into three parts. First, it downloads the agent exe. Then is uses Windows Installer to install the agent on the server. Finally, a command is run to authenticate the agent to the Azure Arc service.
Before I could run this part of the script, I needed to close and reopen my PowerShell window. And it should go without saying that your server must have Internet connectivity.
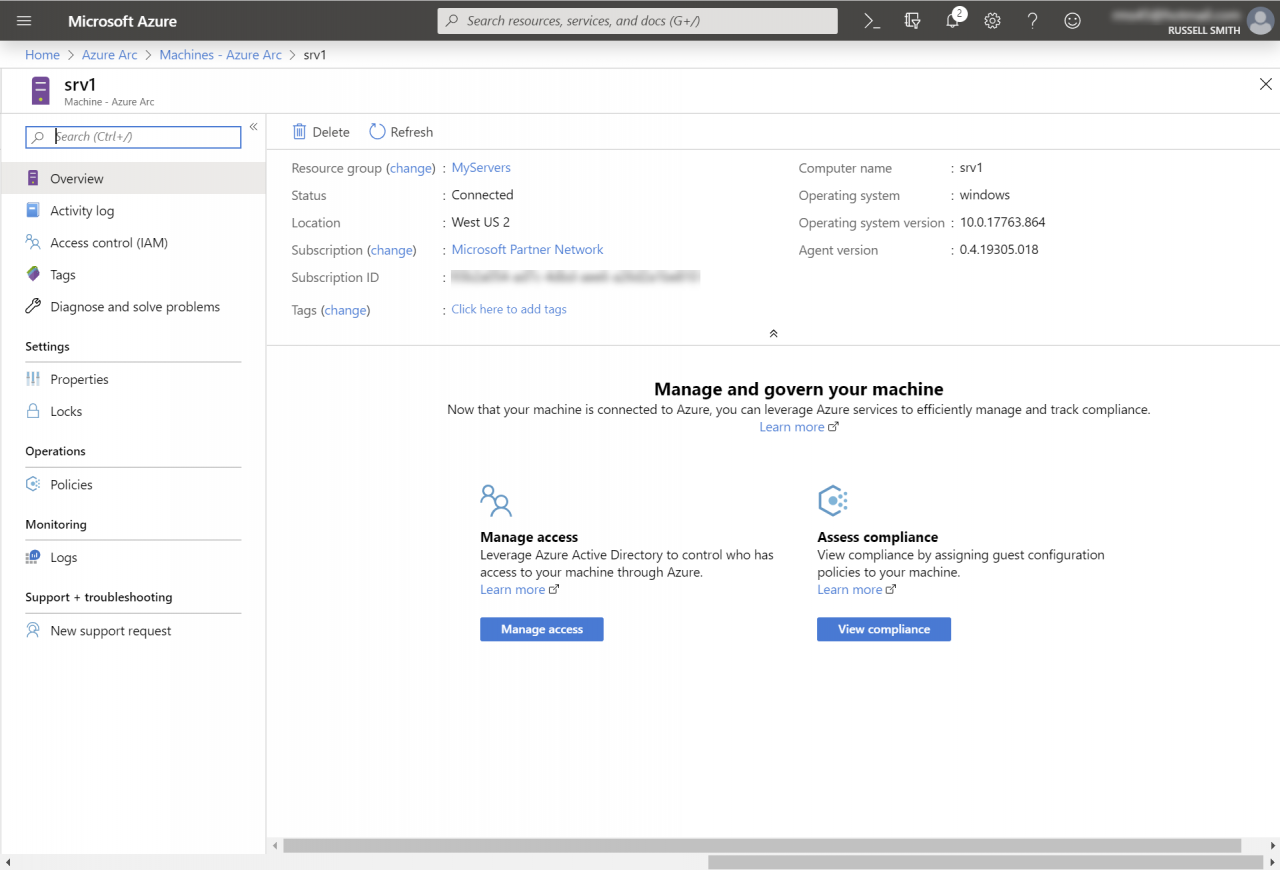
Authenticating to Azure Arc involves opening a URL provided by the script, entering a code, and then Azure tenant credentials that have permission to add servers to Arc. Once your server is connected, you can go back to the Arc Machines page in the Azure management portal and your server should be listed. If Arc doesn’t receive a heartbeat signal from the server for more than 5 minutes, it will be shown as ‘Offline’.
Audit and manage access using Azure Arc
There several things you can do once a server is connected to Arc. You can view and filter the server’s logs. Optionally, you can apply RBAC to determine who gets to do what with the resource that is created in Azure when you connect a server to Arc. You can add tags to help organize resource management and assign Azure policies and initiatives, which are one or more policies grouped together. There are 38 built-in initiatives and 387 policies to choose from.
Just like when using Azure Security Center, there’s a default initiative applied to servers called ASC Default. As far as I can tell, the main difference between what Arc offers and Security Center is that Arc just lets you know whether your servers are compliant with assigned policies and initiatives. But Security Center goes one step further by providing advice on how to remediate security issues on non-compliant servers.
Summary
As is usually the case with Microsoft’s management products and services, here there is a mix of services being brought together to offer a more complete capability for organizations that need to manage hybrid workloads. And from what I can see, it looks like Azure Arc is shaping up to be an interesting service.


