Making Office 365 Activity Alerts More Accessible
Creating Alerts from Office 365 Audit Events
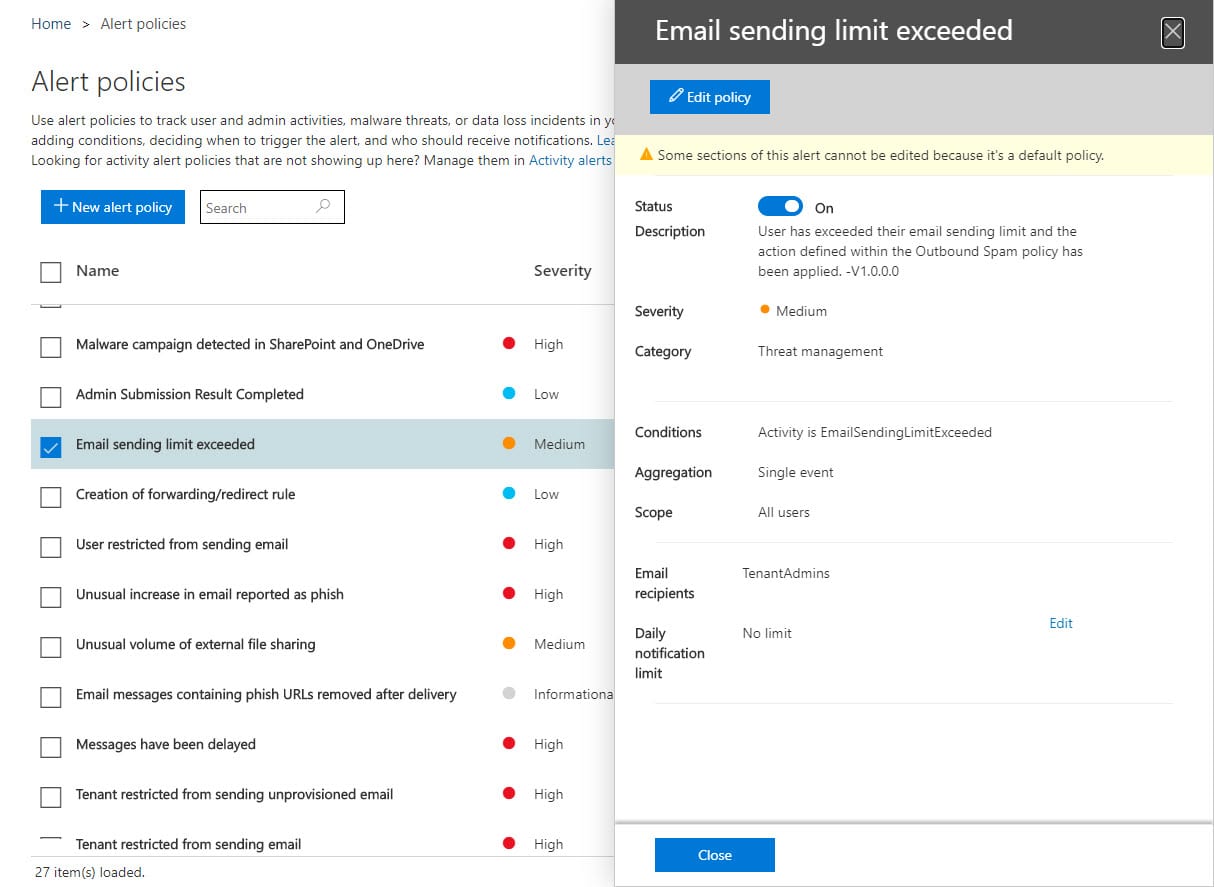
As events from workloads flow into the Office 365 audit log, activity alerts and alert policies look for instances of specific events. Alert policies are more sophisticated because they allow time-limited thresholds for activities to be defined so that an alert won’t be created unless the threshold is breached within a set period. Policies can also be restricted to monitoring specific users. Microsoft populates some alert policies for tenants, with the exact set depending on the licenses held by the tenant. Figure 1 shows an example of an alert policy created by Advanced Threat Protection (ATP).
Products can add alert policies too, which is what is done for communication compliance policies to advise when potential policy violations are detected. Finally, tenants can create custom alert policies to meet their own needs.
Processing Alerts
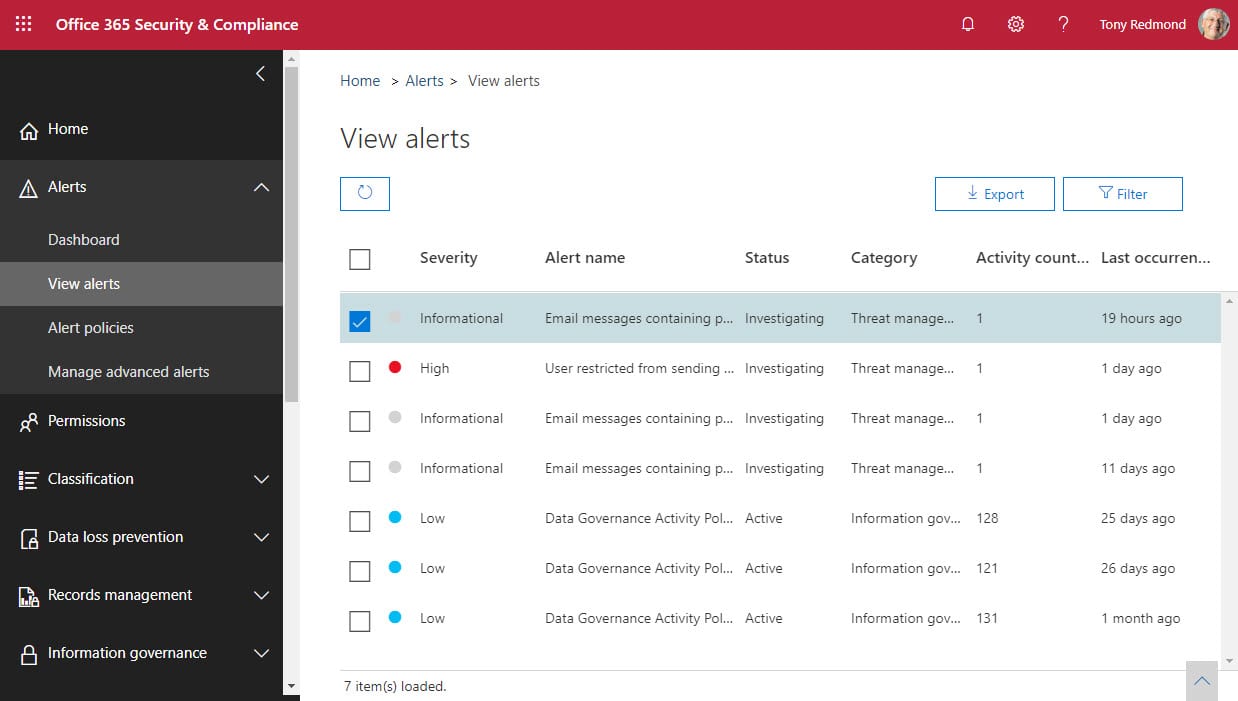
When the conditions set in an alert policy are met, Office 365 notifies individuals defined in the policy by email. Administrators can then access the View Alerts page in the Security and Compliance Center (Figure 2) to work with the alerts and decide if any further action is needed.
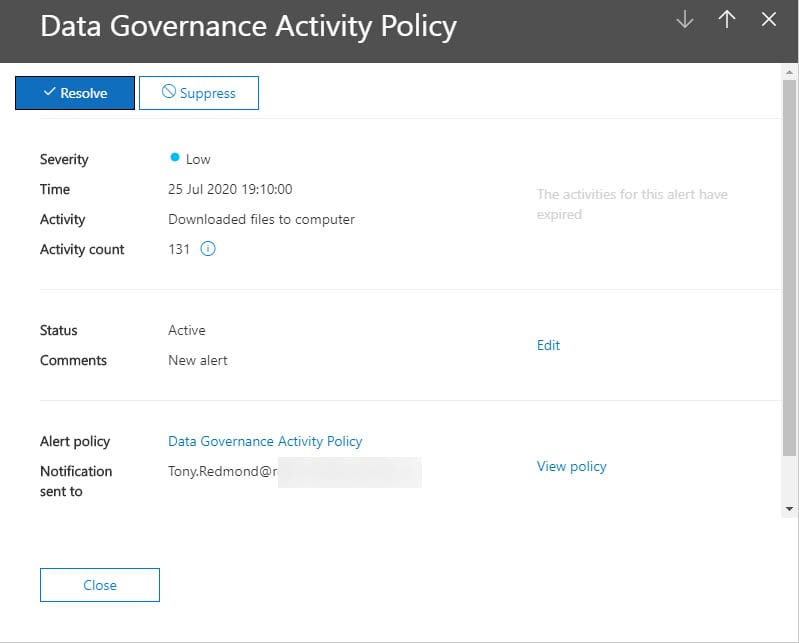
Access to the Alert information is controlled by RBAC roles; the alerts that people see depends on the roles held by their account (see this page for more information). The value of alerts degrades with time, so Office 365 purges alerts from the View Alerts dashboard after 30 days. After accessing the dashboard, users can examine details of the alerts available to them (Figure 3).
Hopefully, an alert can be quickly resolved because administrators are aware of a problem. Sometimes it’s hard to know what needs to be done without going back to check the policy. For instance, the alert shown in Figure 3 is generated when 120 file downloads are done by the OneDrive sync client in 180 minutes. The figure is aggregated, so any download by any user is counted. Note that in this instance the linked activities aren’t available because we’ve taken too long to check the alert. Linked activities are only available for a week. Once you’re happy that the event is understood, click the Resolve button to mark it as such.
If you get too many alerts, you could increase the aggregated number or decrease the period to make it less likely that the threshold is met.
Better Access to Alerts
The email delivered to notify people about alerts contains a link to bring the recipient to the alert. It’s easy to understand how messages can be overlooked in a busy inbox or how people don’t have the time to open the Security and Compliance Center to check current alerts. The question is then how to create better access to alerts.
PowerShell cmdlets are available to add, edit, or remove alert policies but not to list current alerts. You can find some information in Office 365 audit events, but the alert data is not easily accessible. Fortunately, better data is available through the https://graph.microsoft.com/beta/Security/Alerts endpoint in the Microsoft Graph. It’s easy to create a registered app in Azure AD and assign it the necessary permission (SecurityEvents.Read.All) to read the alert data. The required steps to create the app and use it to retrieve an access token are described in this article.
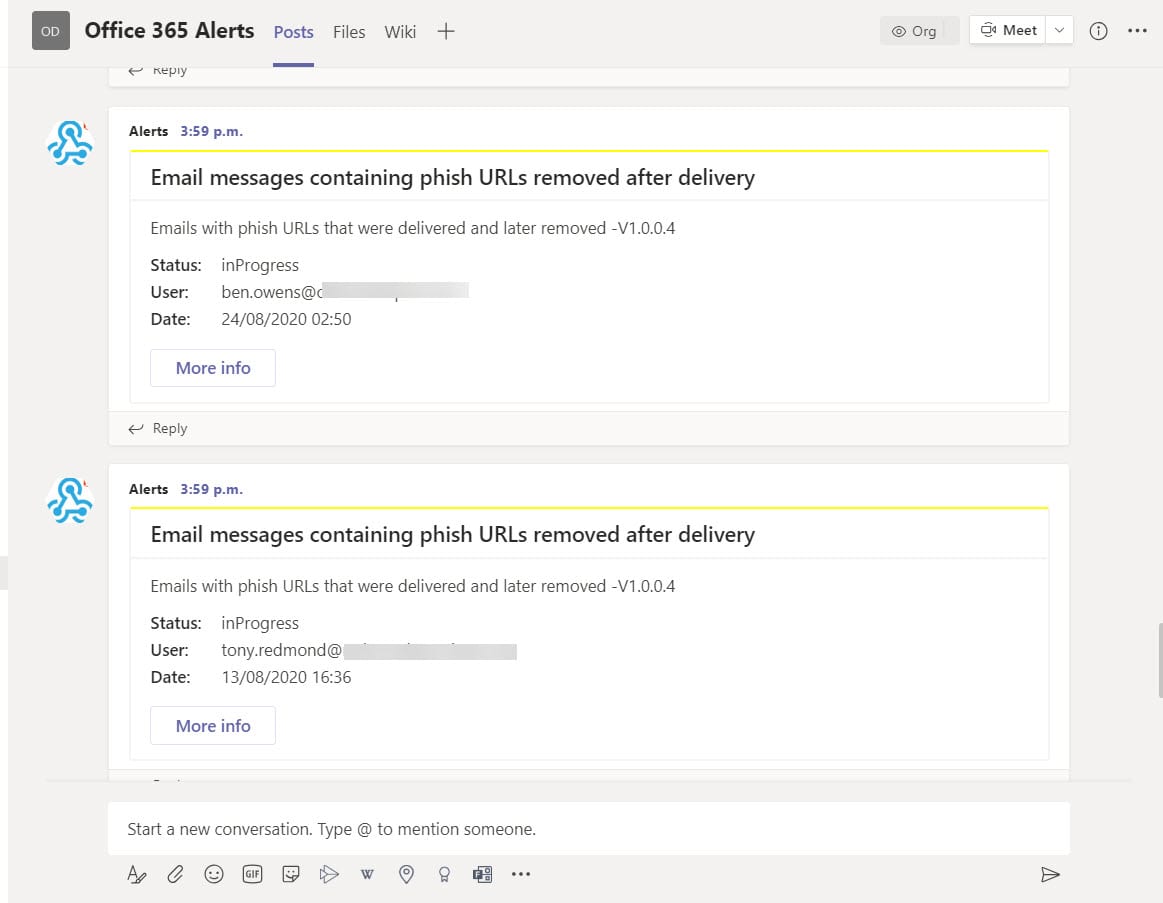
I wrote a script (available from GitHub) to illustrate how to access the alert data and parse what’s returned by the Graph. I then added some code to post information about new and unresolved alerts to a Teams channel using the incoming webhook connector. The idea is that people will see these alerts and act.
No guarantees are given for the script. It will need work to integrate into your environment. It’s designed to be is an illustration of the principle rather than a fully worked-out example. I make the same excuse for my coding efforts all the time…
Other Ways to use Alert Data
You could also use the information to create your own email but seeing that Office 365 already sends email when the alert is first created, that seems like reinventing the wheel. Another idea would be to post details of unresolved alerts to an administrative dashboard. The point being that once you have access to the alert data, the possibilities are endless.