
Key Takeaways:
- Security researchers at Binarly have identified a new firmware vulnerability named LogoFAIL, affecting both Windows and Linux machines.
- It enables attackers to replace legitimate logos with specially crafted images, leading to the execution of malicious code during the boot process.
- The majority of consumer and enterprise-grade computer models are vulnerable to LogoFAIL attacks.
Security researchers have disclosed a new firmware vulnerability named LogoFAIL, which is capable of infiltrating a wide array of Windows and Linux machines. The attack allows threat actors to use malicious logo images to potentially compromise the security of devices from major vendors, including Intel, Acer, and Lenovo.
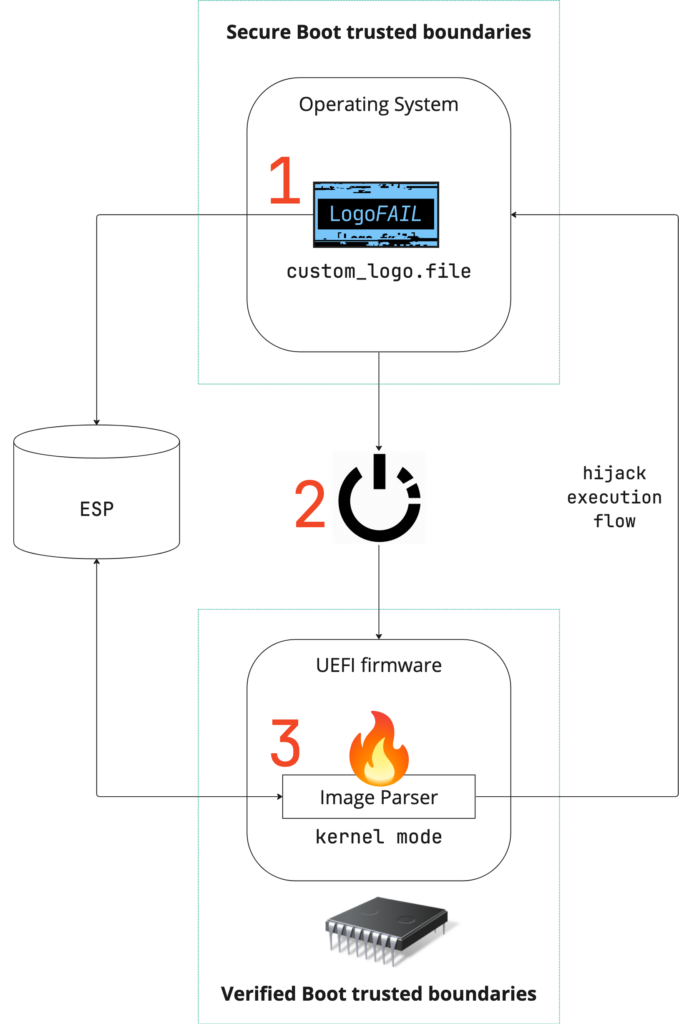
Cybersecurity company Binarly has discovered a security flaw in the image parsers used by the UEFI firmware to display logos on the device screen during the boot process. The researchers presented the details of the LogoFAIL attack at the Black Hat Europe conference on Wednesday.
Mode of LogoFAIL attack
The LogoFAIL attack allows hackers to replace the legitimate logo with a specially crafted image. This can lead to the execution of malicious code during the Driver Execution Environment (DXE) phase of the boot process. The DXE phase loads and executes UEFI drivers that manage hardware components such as network interfaces and storage controllers. This method helps the threat actor to compromise the entire computer system and bypass built-in security protections like Secure Boost.
“Once arbitrary code execution is achieved during the DXE phase, it’s game over for platform security,” researchers from Binarly, the security firm that discovered the vulnerabilities, wrote in a whitepaper. “From this stage, we have full control over the memory and the disk of the target device, thus including the operating system that will be started,” Binarly explained.
Majority of Windows and Linux devices are vulnerable to LogoFAIL attacks
Here’s a video that shows how a hacker can exploit the vulnerability to gain firmware-level privileges on the operating system.
As it turns out, the affected firmware is shipped with hundreds of consumer and enterprise-grade computer models. These include X86 and ARM-based devices with firmware from three major BIOS vendors, namely Insyde, AMI, and Phoenix.
It’s important to note that image parser vulnerabilities have been found in several devices from popular vendors. However, the research study shows that attackers cannot always exploit these flaws. For instance, Dell has implemented the Image Boot Guard to safeguard image files and prevent unauthorized changes to the logo, even if the target system is compromised. Similarly, Apple has hardcoded logo images into the UEFI of their Mac devices for added protection.
Cybersecurity researchers have warned that both OEMs and motherboard manufacturers are vulnerable to image parser vulnerabilities. It is highly recommended that users promptly apply new UEFI security patches to protect their systems from firmware-based attacks.



