
Key Takeaways:
- Security researchers reveal ongoing exploitation of the Log4j vulnerability by the Lazarus hacking group, showcasing the persistent and widespread nature of the threat.
- Lazarus leverages the security flaw to deploy remote access Trojans (RATs) written in Dlang.
- Cybersecurity researchers found that a significant 32% of applications are still running vulnerable versions of Log4j.
Security researchers have disclosed that hackers are persistently exploiting the Log4j vulnerability to infiltrate organizations globally. The infamous Lazarus hacking group has recently exploited this flaw to launch a fresh wave of cyberattacks, deploying new remote access Trojans (RATs) coded in the D programming language.
What is Log4j?
The Log4j vulnerability, also known as Log4Shell, was discovered in December 2021. This security flaw (CVE-2021-44228) exists in the Apache Log4j 2 library, which is a widely used Java-based logging utility. It lets hackers execute arbitrary code by exploiting the log4j library’s ability to process users’ data in log messages.
The Log4j vulnerability received a severity rating of 10 out of 10 on the CVSS bug severity scale. It impacts several applications and services that use Log4j for logging purposes. As a result, cybersecurity researchers recommend that organizations should update their systems and applications to a patched version of Log4j.
Last week, cybersecurity firm Veracode revealed that around 32 percent of applications are still running vulnerable versions of Log4j. Log4j2 1.2x reached end of support in August 2015, and it no longer receives security patches.
“Veracode analyzed data from software scans over 90 days between August 15 and November 15, 2023 for 38,278 unique applications running Log4j versions 1.1 through 3.0.0-alpha1 across 3,866 organizations,” said Chris Eng, chief research officer at Veracode.
Lazarus uses new malware tools in cyberattacks
In March 2023, Cisco Talos researchers discovered a campaign named “Operation Blacksmith.” The threat actors behind the campaign have been targeting agriculture, manufacturing, and physical security companies. The attackers have deployed a new malware written in the unpopular D programming language to avoid detection.
The Lazarus hacking group utilized the Log4j vulnerability to gain entry to the vulnerable server. After gaining initial access, they used a custom proxy tool named “HazyLoad” to establish persistent access. Next, the attackers created new admin accounts on the host machine and used them to download credential-stealing software, including ProcDump and MimiKatz.
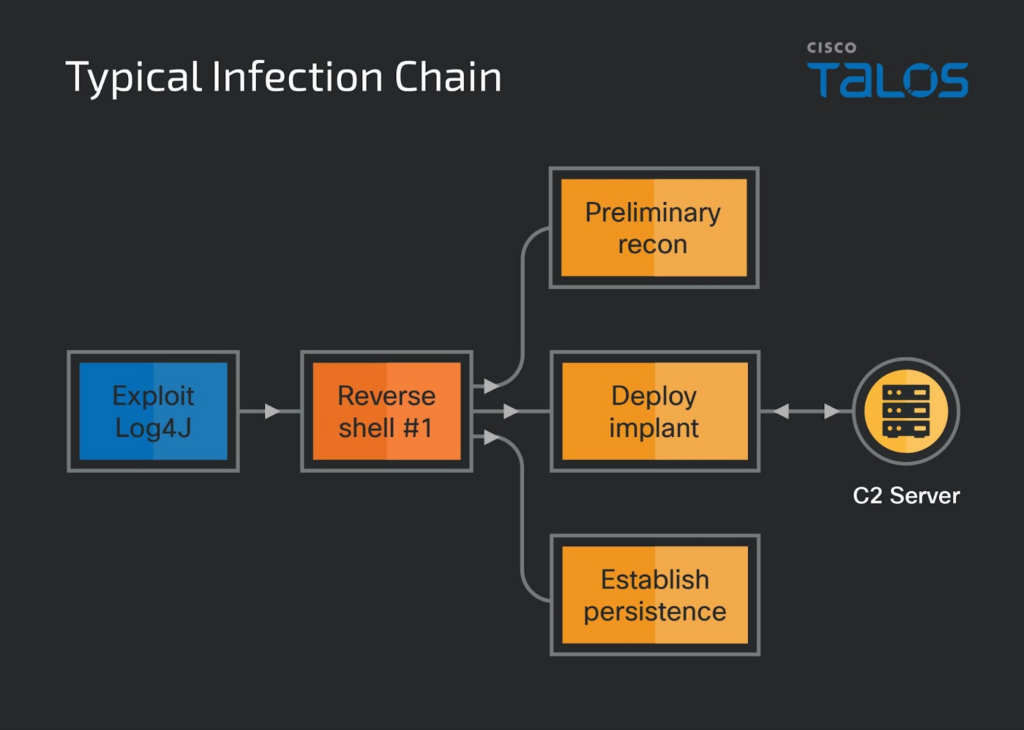
In the second phase of the attack, the Lazarus group deployed the NineRAT malware on the compromised system. The backdoor leverages the Telegram API as its command and control communication. The hackers also used the DLRAT malware to download and execute additional payloads on the infected computer.
Additionally, the security researchers identified a malware downloader named “BottomLoader,” which uses PowerShell commands to execute payloads from a hardcoded URL. It can also modify the Startup directory to gain persistence.
How to protect organizations against Lazarus attacks?
According to Cisco researchers, Lazarus may be sharing the data collected by NineRAT with other hacking groups. For this reason, businesses should adopt a proactive and multi-layered approach to protect their sensitive data and infrastructure.
This includes deploying advanced threat detection tools, using network segmentation, and conducting regular security audits to enhance security defenses against Lazarus attacks. Moreover, organizations should educate their employees about phishing threats and other social engineering tactics.



