Set Up Active Directory to Support Tiered Administration and Privileged Access Workstations
In this Ask the Admin, I’ll discuss setting up Active Directory to support a secure tiered administrative model and Privileged Access Workstations (PAWs).
At the end of last year, I wrote several posts on how to administer Active Directory securely. Some of the concepts in those articles might have been new to you, such as the clean source principle and tiered administration. If you need to recap those topics, see Managing Privileged Access to Active Directory, Why You Should Use Microsoft’s Active Directory Tier Administrative Model, and Secure Active Directory Using the Clean Source Principle on Petri.
I also mentioned Privileged Access Workstations, which use a dedicated installation of Windows for sensitive Active Directory management tasks. PAWs are hardened to protect them from threats that might otherwise be pervasive on user workstations. The separation of tasks and accounts from workstations and accounts used for everyday computing tasks helps to protect Active Directory from vulnerabilities and many different types of attack.
Originally, I was going to write a post on setting up Privileged Access Workstations. But Microsoft has a good set of instructions here that you can follow with a detailed architectural overview. However, I will provide a summary of the process below. But remember that the instructions are frequently updated, so I recommend you refer to Microsoft’s detailed instructions.
The instructions include a link to a set of PowerShell scripts that set up an Organizational Unit (OU) structure and the required groups for managing PAWs. The OU structure goes beyond what’s needed for PAWs and provides everything needed for tiered administration. You can download the scripts as a zip archive here from the TechNet gallery.
Create an OU Structure and Group Policy Objects in Active Directory
I started by running three scripts in the following order: Create-PAWOUs.ps1, Create-PAWGroups.ps1, Set-PAWOUDelegation.ps1. In addition to the scripts, you’ll need to manually create two Group Policy objects (GPOs), PAW Configuration – Computer and PAW Configuration – User, and link them to the relevant OUs, Tier 0\Admin\Devices and Tier 0\Admin\Accounts respectively. In the figure below, you can see the OU structure that Create-PAWOUs.ps1 creates.
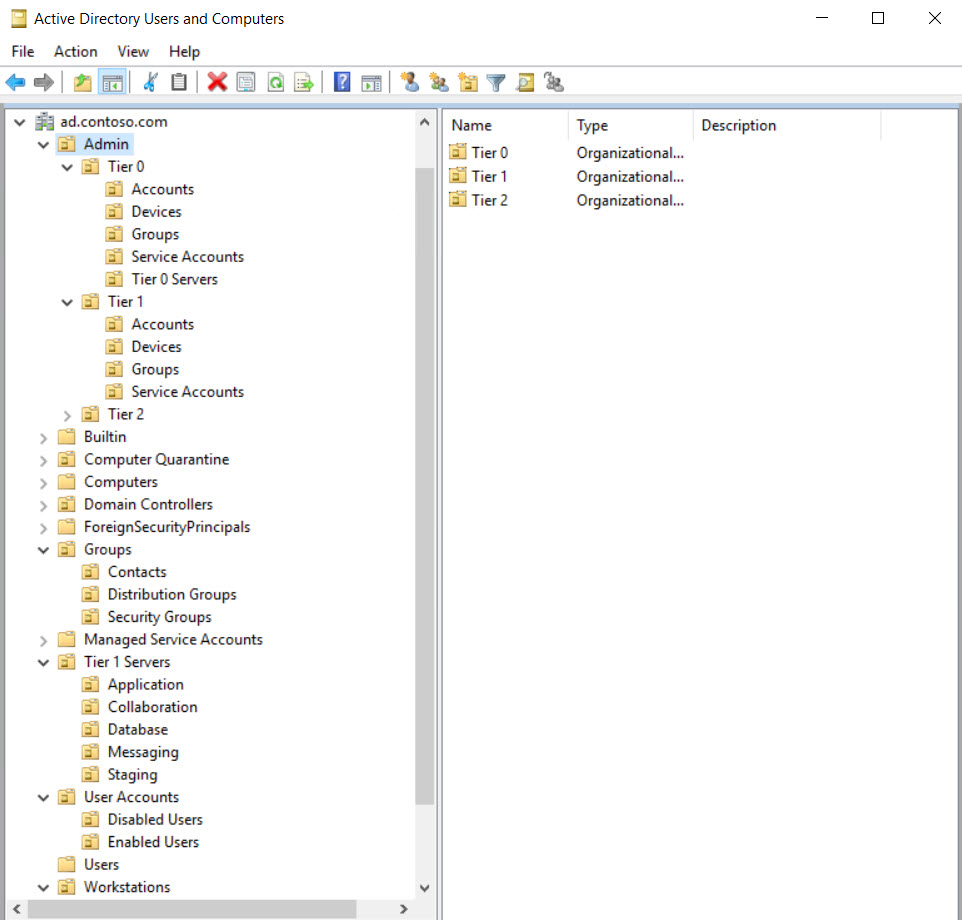
Here is a list of groups created by Create-PAWGroups.ps1:
- Tier 0 Replication Maintenance
- Tier 1 Server Maintenance
- Service Desk Operators
- Workstation Maintenance
- Cloud Service Admins
- PAW Users
- PAW Maintenance
- Tier 1 Admins
- Tier 2 Admins
Notice that there’s no Tier 0 Admins group. That’s because Tier 0 admins should be added to the PAW Users group. It’s worth noting that the PAW Users group should not be a member of the local Administrators group on PAWs to prevent users from modifying PAW security settings.
The GPO settings must be configured manually. Except for Windows Firewall rules, which can be imported from a file included in the zip archive. When configuring Local Group preferences, be sure to follow Microsoft’s instructions carefully, taking special note of the requirement not use the Browse button for certain entries. This is to make sure you include local accounts and groups and not AD accounts and groups.
The configuration settings for the GPOs will take you some time to set up. This is just a case of carefully following through with the instructions. In addition to the two PAW GPOs, there are several other GPOs that you should create:
- RestrictedAdmin Required – Computer
- Restrict Workstation Logon
- Restrict Server Logon
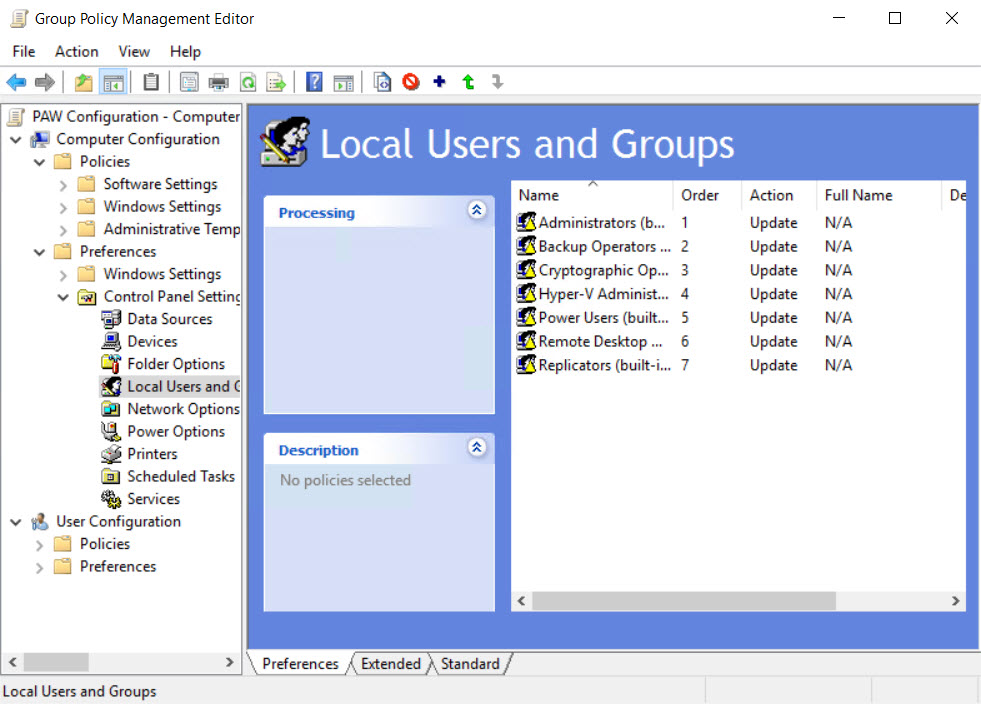
Create a Restrict Server Logon GPO and link it to Tier 1 Servers OU. This GPO will prevent Tier 0 accounts logging in to Tier 1 servers. The Restrict Workstation Logon GPO should be linked to the Workstations OU and prevents Tier 0 and Tier 1 administrators from logging into workstations. Finally, the RestrictedAdmin Required – Computer GPO enforces the /RestrictedAdmin switch for outgoing Remote Desktop connections.
In addition to the GPOs listed above, you’ll need to create and link security baseline GPOs, which you can create using Microsoft’s baseline security templates provided in the Security Compliance Toolkit (SCT). For more information on using SCT, see Microsoft Launches the Security Compliance Toolkit 1.0 on Petri.
Setting Up a Privileged Access Workstation
The PAWs should be built using the Clean Source Principle and disconnected from the network while Windows 10 is being installed. For more information on the Clean Source Principle, see Secure Active Directory Using the Clean Source Principle and Validate the Integrity of Installation Media on Petri.
Each PAW needs a strong and unique local administrator password. You should use the Local Administrator Password Solution (LAPS) to manage local administrator passwords on PAWs and other domain-joined devices. For more information on LAPS, see Secure Local Administrator Accounts with the Local Administrator Password Solution (LAPS) Tool on Petri.
To join a PAW to your domain the Add-Computer cmdlet, open a PowerShell as a local administrator. You will need to change the command line below so that your AD fully qualified domain name (FQDN) is used instead of ad.contoso.com in -OUPath and that the FQDN name of your domain is used in -DomainName. When you run Add-Computer, you’ll be prompted to enter the domain credentials you want to use to join the PAW to the domain.
Add-Computer -DomainName ad.contoso.com -OUPath "OU=Devices,OU=Tier 0,OU=Admin,DC=ad,DC=contoso,DC=com"
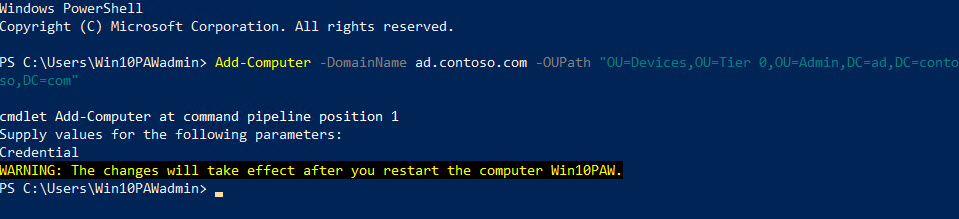
Finally, run gpupdate /force /sync to update Group Policy and force the PAW to restart. Now that the PAW is joined to the domain and configured, members of the PAW Users group can log in.
In this article, I showed you how to set up Active Directory for tiered administration and Privileged Access Workstations. There are important details, such as installing remote administration tools and configuring Windows Update, that are missing from my overview. For a complete list of steps, be sure to check Microsoft’s detailed instructions here.




