IT Admins Get New Azure AD Temporary Access Pass Feature to Create Time-Limited Passcodes

Microsoft has announced that Temporary Access Pass (TAP) is generally available for commercial customers. The Temporary Access Pass feature enables users to securely sign in to their accounts without a password.
Microsoft launched the public preview of Temporary Access Pass in Azure Active Directory earlier this year. It could be useful in scenarios where the old credentials are lost, or the device is stolen. The TAP feature can also be used to set up new Windows PCs for employees.
“TAP is a time-limited passcode that basically temporarily enables users to sign-in. That sign-in is focused on getting users up-and-running with passwordless authentication and on helping users recover access to their account. And all of that without the usage of a password, as TAP satisfies the needed strong authentication requirements,” the company explained.
Notably, IT teams will be able to configure and manage the Temporary Access Pass feature for users in their organization. First up, IT admins with Global Admin or Authentication Policy Admin permissions will need to enable TAP for users in their tenants. Next, they should create a Temporary Access Pass for a particular end-user in Azure AD.
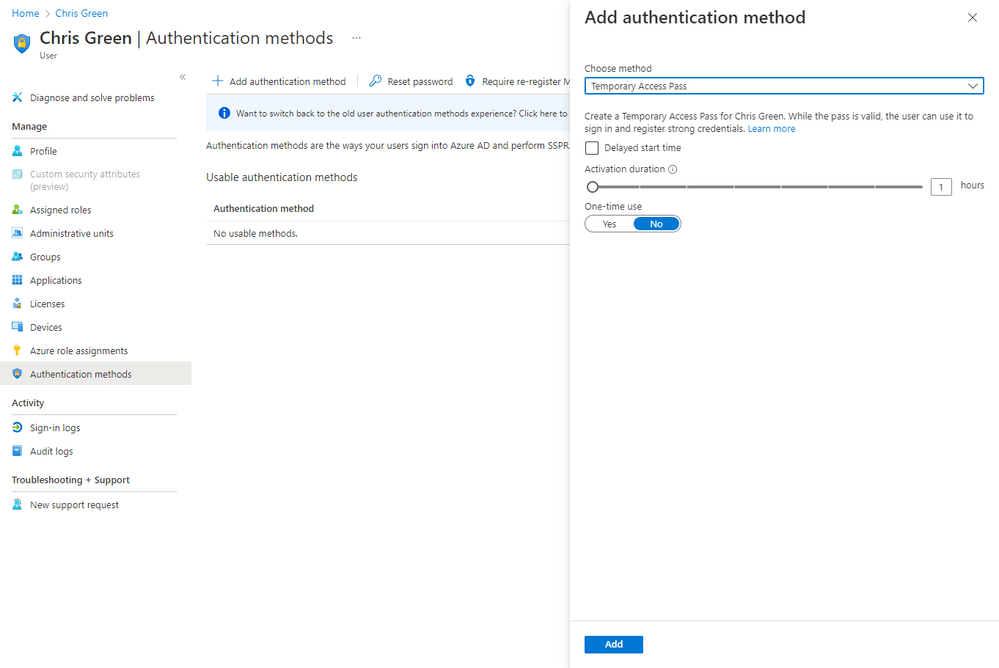
How to use a Temporary Access Pass
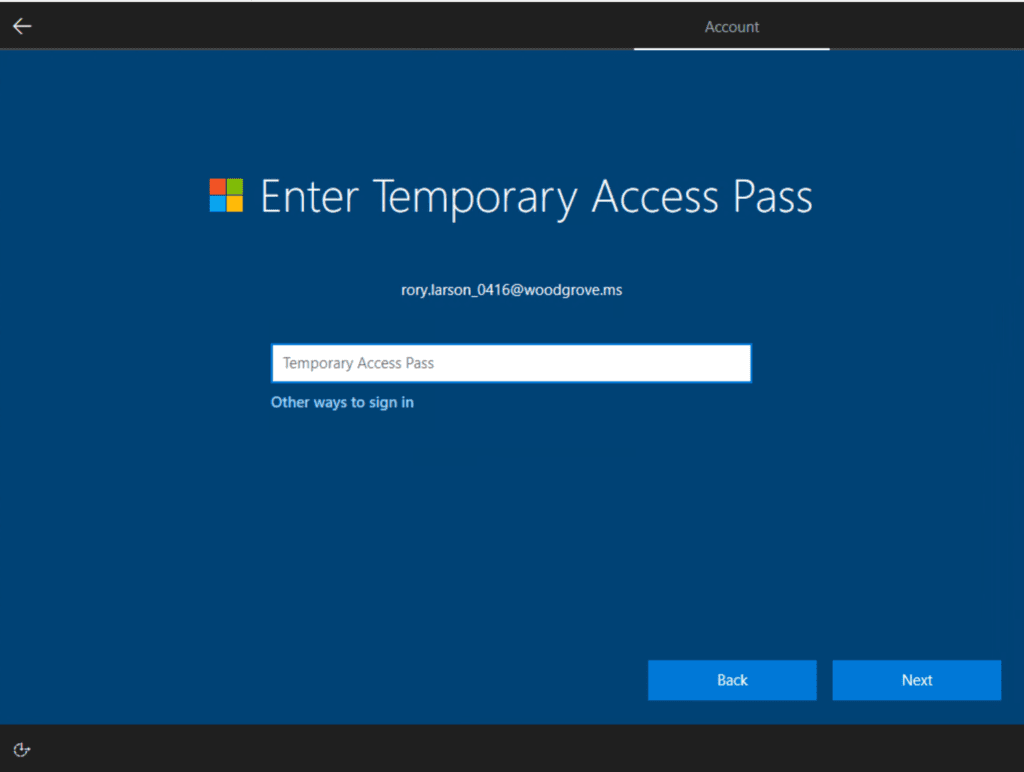
Once the TAP is created, the user can use it to sign in and register a secure authentication method by following these steps:
- Open a web browser and head to Microsoft’s security portal.
- Enter the UPN of the account associated with the Temporary Access Pass (such as [email protected]).
- The user will be prompted to enter their Temporary Access Pass on the Sign-in screen.
- Finally, enter the Temporary Access Pass shared by the IT admin.
Meanwhile, IT administrators can assign new Temporary Access Passes to replace old ones or delete expired passcodes. There is also an option to use Microsoft Graph APIs to integrate TAP with existing apps or an “HR-driven provisioning process.”
Microsoft has outlined some limitations of the Temporary Access Pass capability in Azure AD. It requires users to register a new Passwordless authentication method (such as Phone sign-in or FIDO2) within 10 minutes of the TAP sign-in. If you’re interested, you can check out Microsoft’s support page for more information.



