How to Block TLS 1.0 and TLS 1.1 in Microsoft Edge and Google Chrome
In October 2018, Microsoft announced that it intended to disable Transport Layer Security (TLS) 1.0 and 1.1 in Microsoft Edge and Internet Explorer 11 in the first half of 2020. Along with similar announcements from Apple, Google, and Mozilla, the idea was to provide users with more performant and secure connections.
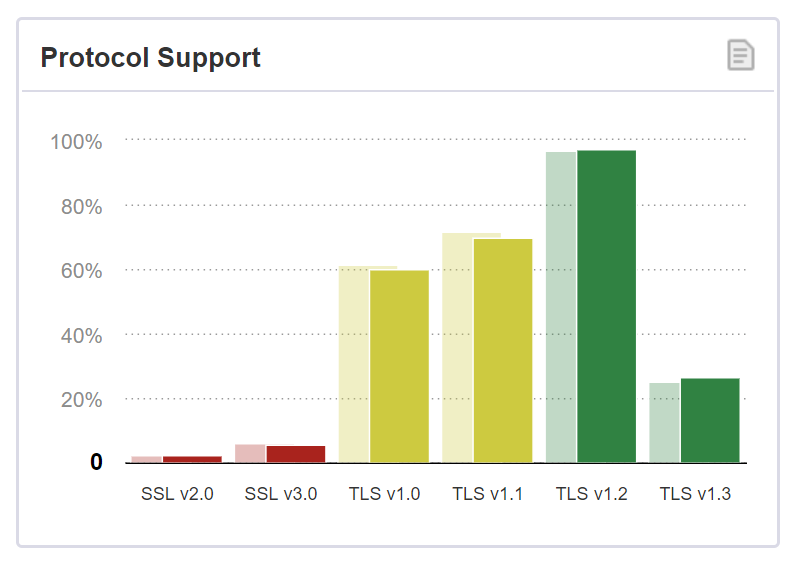
Microsoft said that most sites wouldn’t be impacted by the change. Legacy Edge and Internet Explorer 11 both support TLS 1.2. And the new Chromium-based Edge additionally supports TLS 1.3. If you head to Qualys SSL Labs site, you’ll see that as of March 2020, 97.1% of sites surveyed support TLS 1.2. It’s best practice to use TLS 1.2 as a minimum, and TLS 1.3 if your webserver supports it.
The Internet Engineering Task Force (IETF) says TLS 1.0 and 1.1 shouldn’t be used. TLS 1.2 with SHA-1 as a signature should also not be used. Neither TLS 1.0 or 1.1 let peers select a stronger hash for signatures in the ServerKeyExchange or CertificateVerify messages than SHA-1. So, the only choice is to upgrade to a newer version of the protocol.
Microsoft postpones support for dropping legacy TLS in its browsers
In an announcement at the end of March, Microsoft said that it would delay disabling legacy TLS protocols by default in all its supported browsers. Originally planned for the first half of 2020, Microsoft will now disable legacy TLS in Chromium-based Edge with the release of version 84.
For the new Microsoft Edge (based on Chromium), TLS 1.0 and 1.1 are currently planned to be disabled by default no sooner than Microsoft Edge version 84 (currently planned for July 2020).
Internet Explorer 11 and legacy Microsoft Edge users will potentially retain default TLS 1.0 and 1.1 support for a bit longer:
For all supported versions of Internet Explorer 11 and Microsoft Edge Legacy (EdgeHTML-based), TLS 1.0 and TLS 1.1 will be disabled by default as of September 8, 2020.
Microsoft does however note that TLS 1.0 and 1.1 will remain available to reenable should the need arise. Although it strongly advices against using either legacy protocol.
Identify or blocking sites using TLS 1.0 or TLS 1.1 in Microsoft Edge and Google Chrome
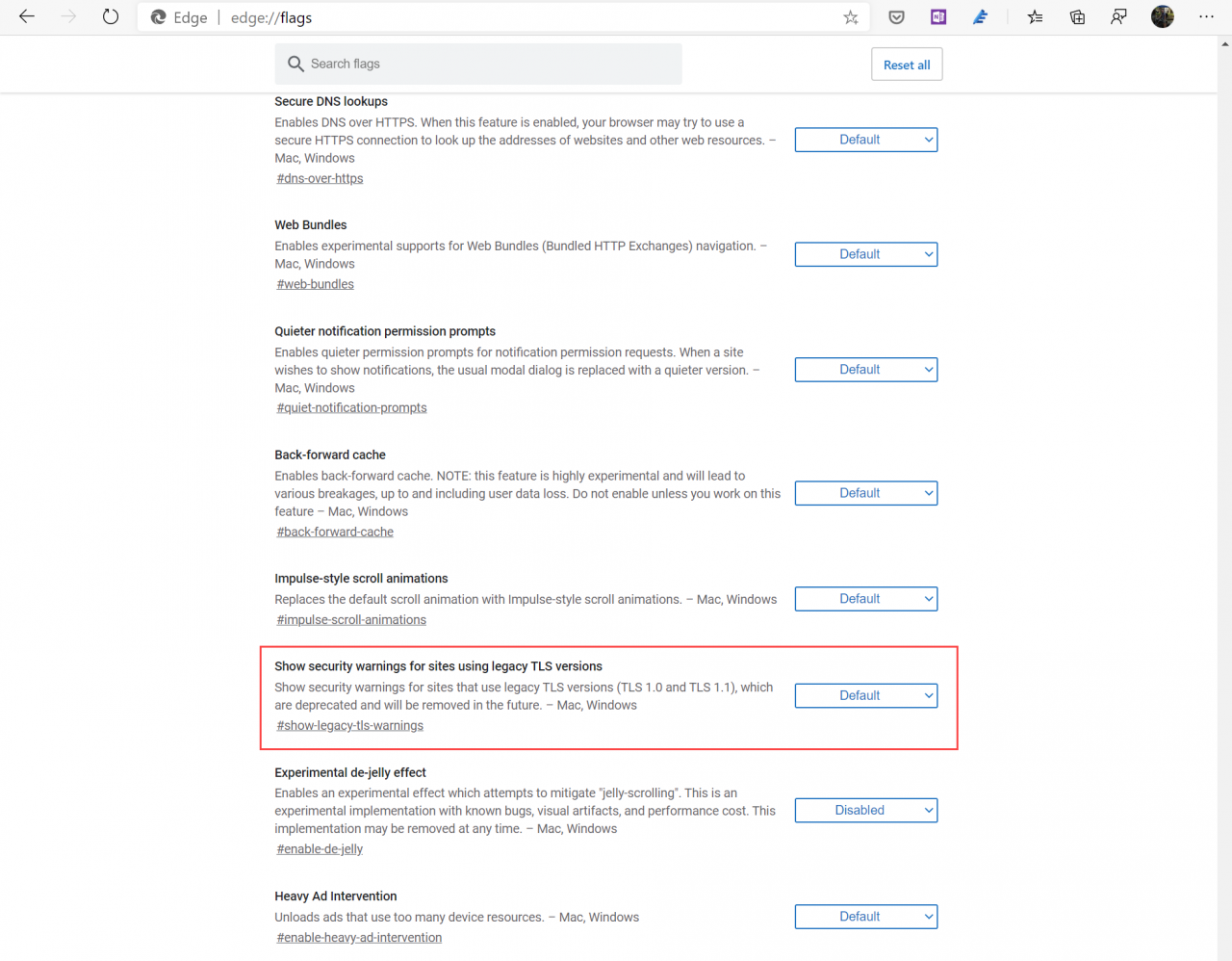
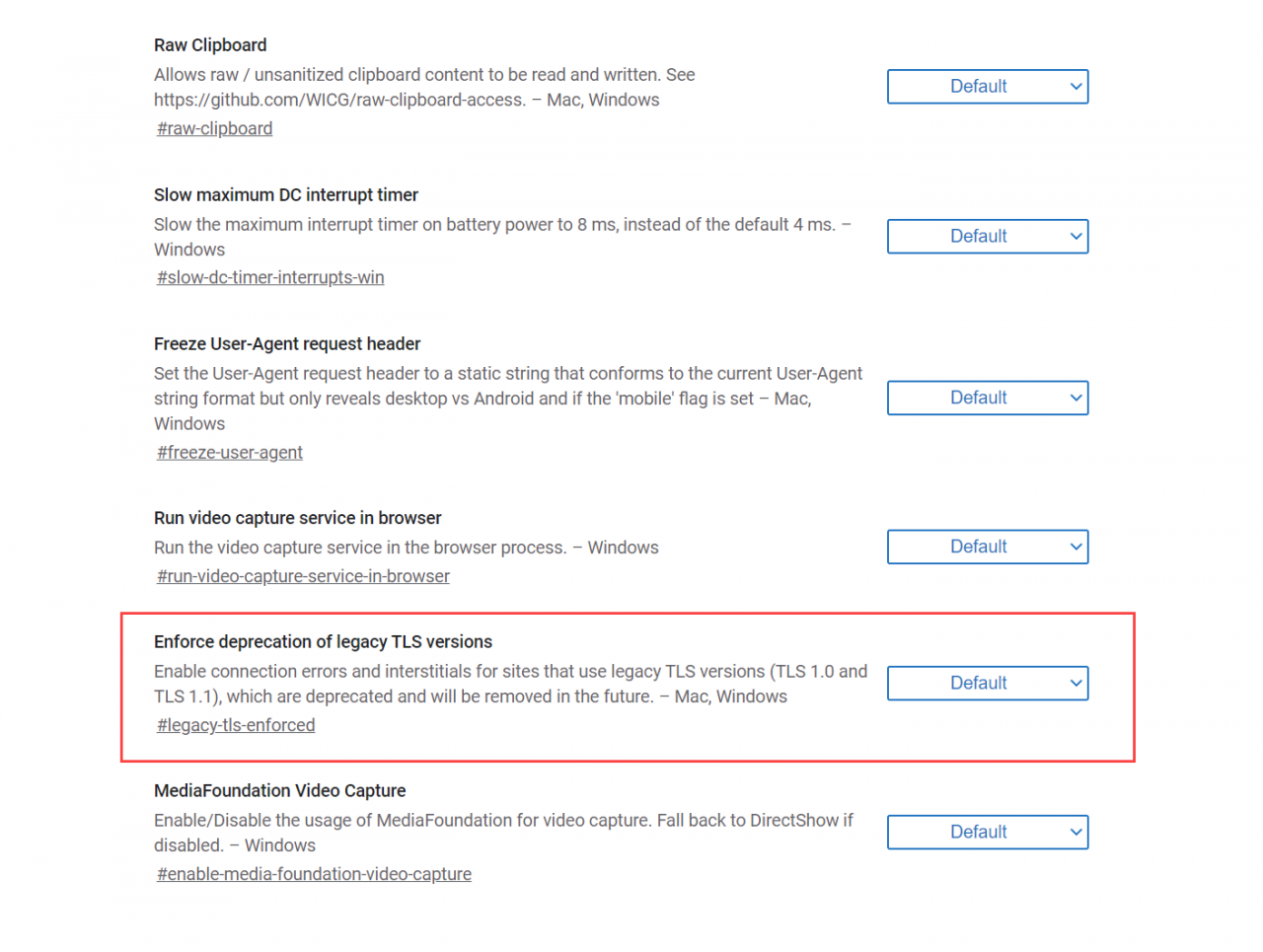
If you decide that you’d like to block legacy TLS protocols sooner, the new Chromium version of Microsoft Edge and Google Chrome let users set flags to enable experimental features or advanced functionality. Both browsers contain a flag to enforce deprecation of TLS 1.0. and 1.1 (legacy-tls-enforced), and a flag to warn users if a site uses legacy TLS (show-legacy-tls-warnings).
To access flags in Microsoft Edge, type edge://flags into the address bar at the top of the browser window and press ENTER. In Google Chrome, type chrome://flags into the address bar and hit ENTER.
Use the search box to find the flags you want to set. Flags can be set to Default, Enabled, or Disabled.
Once you’re done, close the flags tab.
Microsoft Edge Group Policy
Microsoft Edge has a Group Policy setting that lets you set the minimum version of TLS supported. By default, it is currently TLS 1.0. Enabling the SSLVersionMin policy and setting the value to tls1.2 blocks use of TLS 1.0 and TLS 1.1. Microsoft Edge version 77 or later is required to use the SSLVersionMin Group Policy setting.
Office 365 legacy TLS support to end in June
Finally, while Microsoft had been pushing to end legacy TLS support in Office 365 on a much tighter schedule than its browsers, it eventually backed off from the original timeline. In Preparing for TLS 1.2 in Office 365 and Office 365 GCC, Microsoft says:
As of June 2020, Office 365 will begin deprecating TLS 1.0 and 1.1 in worldwide environments for commercial customers and in GCC environments for GCC customers. This means that starting in June 2020, any commercial and GCC clients, devices or services that connect to Office 365 by using TLS 1.0 and 1.1 will not succeed.
TLS 1.0 and 1.1 are already unsupported in Office 365, although haven’t been switched off. That will now happen in June 2020. Microsoft says that the following client operating systems and browsers don’t support TLS 1.2 and must be upgraded:
- Android 4.3 and earlier versions
- Firefox version 5.0 and earlier versions
- Internet Explorer 8-10 on Windows 7 and earlier versions
- Internet Explorer 10 on Windows Phone 8
- Safari 6.0.4/OS X10.8.4 and earlier versions
Check out Microsoft’s blog post for more details on which Office 365 applications and services are affected by legacy TLS protocol deprecation.