How FIDO2 Passwordless Logins Work in Hybrid Azure AD Environments
Microsoft is expanding support for passwordless logins to devices that are hybrid joined to Azure AD domains. In this article, I explain how FIDO2 security keys work in hybrid Azure AD environments. Microsoft announced a public preview of support for FIDO2 security keys in hybrid Azure AD environments in late in February. FIDO2 security keys enable passwordless login for users. Microsoft has been pushing the concept of passwordless logins for several years because security experts agree that passwords alone are no longer effective.
Multifactor authentication (MFA) can improve the effectiveness of passwords considerably. Once a device is ‘trusted’, users might not be challenged to provide an additional factor with their password for a couple of weeks or a month. But uptake hasn’t been anything near what Microsoft had hoped. Partly because MFA can be complicated to set up and it adds an additional layer to the login process.
If you already understand how FIDO2 security keys and hybrid Azure AD environments work, you can skip straight to FIDO2 support in hybrid Azure AD environments below.
How do FIDO2 security keys work?
FIDO2 security keys provide for several different options when users log in:
- Single factor passwordless
- Two-factor authentication
- Multifactor authentication
FIDO2 security keys can provide single-factor hardware-based authentication that is much stronger than a username and password. FIDO2 keys can also be used additionally as a second factor for even stronger security. And for organizations that want to go all out, FIDO2 security keys may be used in combination with a PIN or biometric gesture for stronger multifactor authentication.
Unlike passwords, PINs are stored locally on the key and aren’t sent across the network. This makes PINs harder to compromise than passwords. PINs are used to unlock the hardware key so it can perform its function. And because PINs perform a limited role, they can be shorter, less complex, and changed less frequently than passwords.
What is a hybrid Azure AD join?
Passwordless sign-in has been available for Azure AD joined devices for some time. Windows 10 devices joined to AAD let users sign in to Windows using their organizational work or school account from the lock screen, either using a password, Windows Hello for Business, or FIDO2 security key.
Users with Azure AD registered devices, on the other hand, must sign in with a local account or Microsoft Account (MSA). But users get single sign-on (SSO) support for cloud resources for simpler access. Registered devices can also be enrolled with Microsoft Intune.
When organizations have both Windows Server Active Directory (AD) and Azure Active Directory, they can opt to perform a hybrid join. This is where Windows 10, 8.1, and 7 devices are domain joined to Windows Server AD and registered with AAD. The main features of a hybrid join are:
- SSO to both cloud and on-premises resources
- Conditional Access through domain join or through Intune if co-managed
- Self-service Password Reset and Windows Hello PIN reset on the lock screen
- Enterprise State Roaming (ESR) across devices
FIDO2 support in hybrid Azure AD environments
Until recently, FIDO2 security key login was only supported on devices joined to an Azure AD domain. Or standalone devices with a local or MSA account. But now FIDO2 login also works on devices hybrid joined to Azure AD. Microsoft says that support for FIDO2 keys in hybrid Azure AD environments has been one of the top requests from customers that already use passwordless authentication.
Microsoft says there are three requirements for FIDO2 support in Azure AD hybrid environments:
- Windows Server 2016/2019 patch for domain controllers
- Windows Insider Builds 18945 or later for PCs
- Version 1.4.32.0 or later of Azure AD Connect
Security keys can also be used to sign in to supported browsers, like Microsoft Edge legacy and chromium-based Edge. Windows Server 2016 must be build 14393.3474 or later. And Windows Server 2019, build 17763.1012 or later.
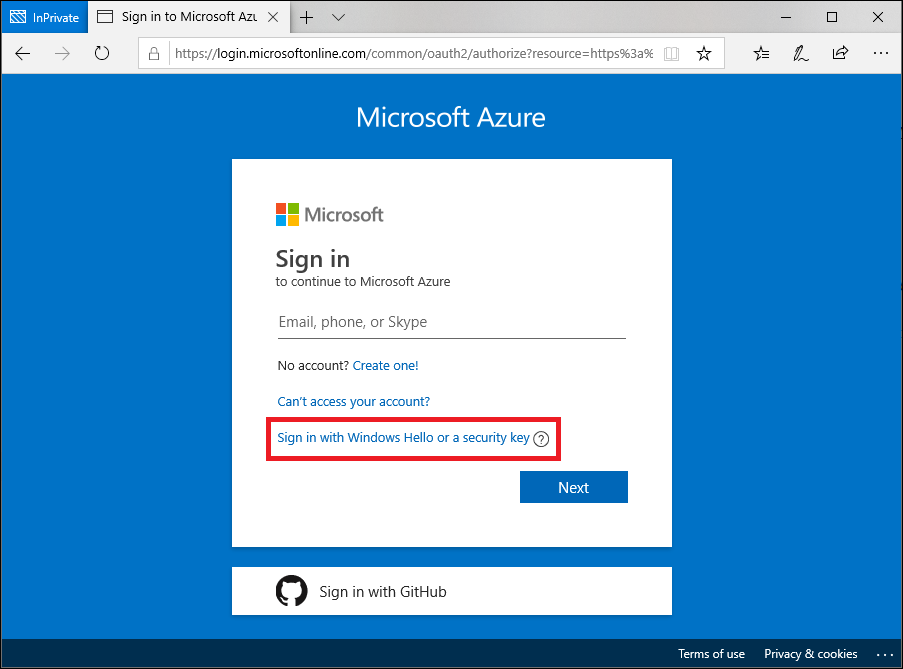
Configure FIDO2 security key support in a hybrid Azure AD environment
To enable support for FIDO2 security keys in a hybrid Azure AD environment, there are several steps that organizations must take.
- Support for security keys as a passwordless authentication option should be enabled in your Azure AD tenant. Users must then provision their security key. You can find more information on these tasks on Microsoft’s website: Enable passwordless security key sign-in to on-premises resources with Azure AD and User registration and management of FIDO2 security keys.
- Windows devices must be enabled to support FIDO2 security keys for sign in. This setting can be enabled in Group Policy: Computer Configuration > Administrative Templates > System > Logon > Turn on security key sign-in. The Turn on security key sign-in group policy setting is provided as part of an updated admx Group Policy template in Windows 10 version 2004 (20H1).
- IT must create an Azure AD Kerberos Server object in their on-premises AD. See Enable passwordless security key sign-in to on-premises resources with Azure Active Directory (preview) on Microsoft’s website for more detail.
For more information on the public preview of FIDO2 support for hybrid Azure AD environments, check out Microsoft’s blog post here.
It’s also worth noting that while many keys are FIDO2-certified, some optional extensions to the FIDO2 Client-to-Authenticator Protocol (CTAP) must be implemented for a security key to work properly with Azure AD. You can find more information about the requirements and approved security key vendors at Microsoft’s website here.
Security keys need to be more ubiquitous
Security keys can be used to log in to Windows 10, whether you have a local user account, an MSA, an Azure AD account, or an Active Directory user account in a hybrid domain environment. Keys come in a variety of forms, including those that connect to USB-A, USB-C, and via NFC.
But security keys pose an additional cost and can be easily lost. While losing a key doesn’t necessarily present a security risk, there is a cost associated with replacing one. When using FIDO2 security keys with Azure AD, users need to remove lost keys as an authentication method and then register a new key. If a lost key was used to log in to third-party sites, then the policy of the site operator determines how the user will gain access. Usually, backup login methods are required when registering a key, like use of one-time codes or an authentication app.
FIDO2 security keys seem like a good idea. But like MFA, registering keys, and the inconvenience of losing one, can put users and organizations off. Nevertheless, the costs associated with compromised credentials are far greater. It’s only a matter of time before everyone gets on board with the need to phase out passwords. And hopefully FIDO2, an alliance that has broad support in the tech industry, will provide a trusted way to log in to systems and websites without vulnerable passwords.



