
Security researchers have disclosed a campaign that allowed hackers to gain access to data center logins for Microsoft, Amazon, Apple, and several other big companies. According to a new report from Bloomberg, the stolen credentials could potentially allow threat actors to gain physical access to clients’ servers.
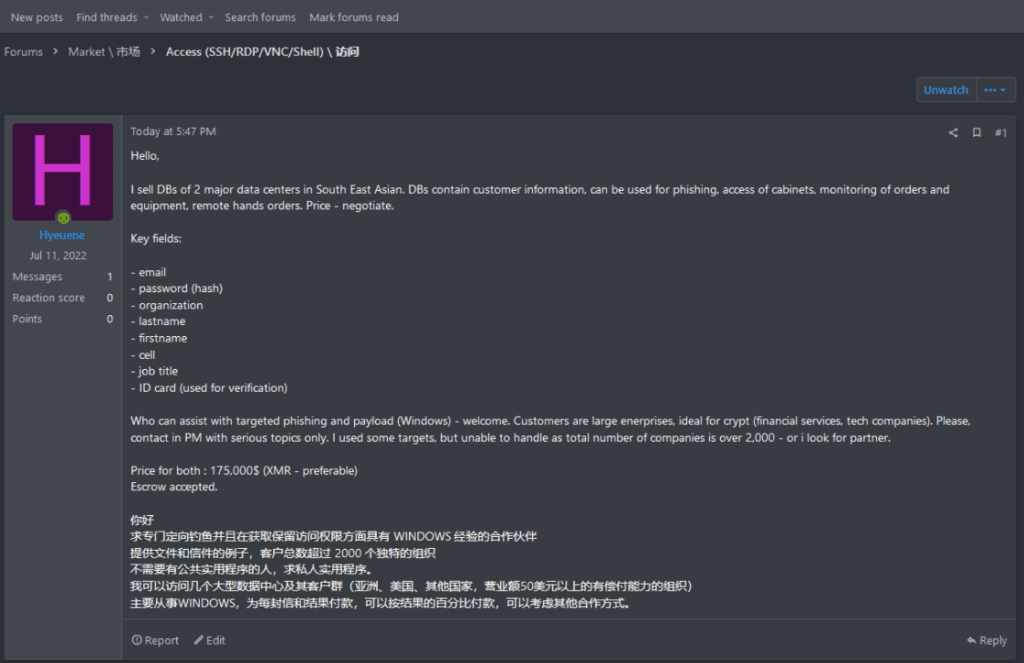
Cybersecurity research firm Resecurity Inc. first discovered the attacks back in September 2021. The security researchers detailed that the threat actors breached two largest third-party data center operators based in Asia to steal emails and passwords for the customer support systems of around 2,000 companies. They also obtained the logins of 30,000 CCTV cameras used to monitor data center environments.
“The information included credentials in varying numbers for some of the world’s biggest companies, including Alibaba Group Holding Ltd., Amazon.com Inc., Apple Inc., BMW AG, Goldman Sachs Group Inc., Huawei Technologies Co., Microsoft Corp., and Walmart Inc., according to the security firm and hundreds of pages of documents that Bloomberg reviewed,” Bloomberg explained.
According to Resecurity, the hackers managed to log into the accounts of at least 5 customers of GDS Holdings and ST Telemedia Global Data Centers in January 2023. At that time, both companies quickly mitigated the attacks with forced password resets for all users. Last month, however, the threat actors posted the login credentials for sale on the dark web for $175,000.
Leaked login credentials could allow physical access to data centers
GDS and STT GDC investigated the incident and found no evidence that the attacks impacted
customer support portals. The data center operators claimed that customers’ data and IT systems are secure. However, four major US-based organizations affected by the attack warned the stolen login credentials could be used to physically access their servers.
“We regularly monitor for threats that could impact Microsoft and when potential threats are identified we take appropriate action to protect Microsoft and our customers.” A Microsoft spokesperson said in a statement to Bloomberg. “We have in place additional controls to protect against this type of breach and we are satisfied that our data was not at risk.”
The security researchers added that the stolen customer information could enable malicious actors to launch phishing attacks against high-profile employees. Furthermore, the data can also be used to monitor the orders and equipment of victims.



