
Security researchers have disclosed a new campaign that exploited a critical Citrix NetScaler vulnerability to infect thousands of devices. They found that hackers have abused the security flaw to target around 2,000 NetScaler instances in Europe.
Last month, Citrix disclosed a zero-day vulnerability, tracked as CVE-2023-3519, which impacts NetScaler Citrix Application Delivery Controller (ADC) and Gateway devices. These devices are designed to provide VPN connectivity and ensure secure application delivery in enterprise environments.
Citrix warned that the remote code execution vulnerability lets attackers drop web shells on vulnerable ADC and Gateway appliances that are configured as a gateway or AAA virtual server. The company released security updates to address the vulnerability on July 18, and urged IT admins to deploy the patches in their organization.
Now, British information assurance firm NCC Group has found the automated exploitation campaign, which launched between 20 and 21 July, affected over 1,950 NetScaler instances. The researchers have identified 2,500 dormant web shells on the compromised devices.
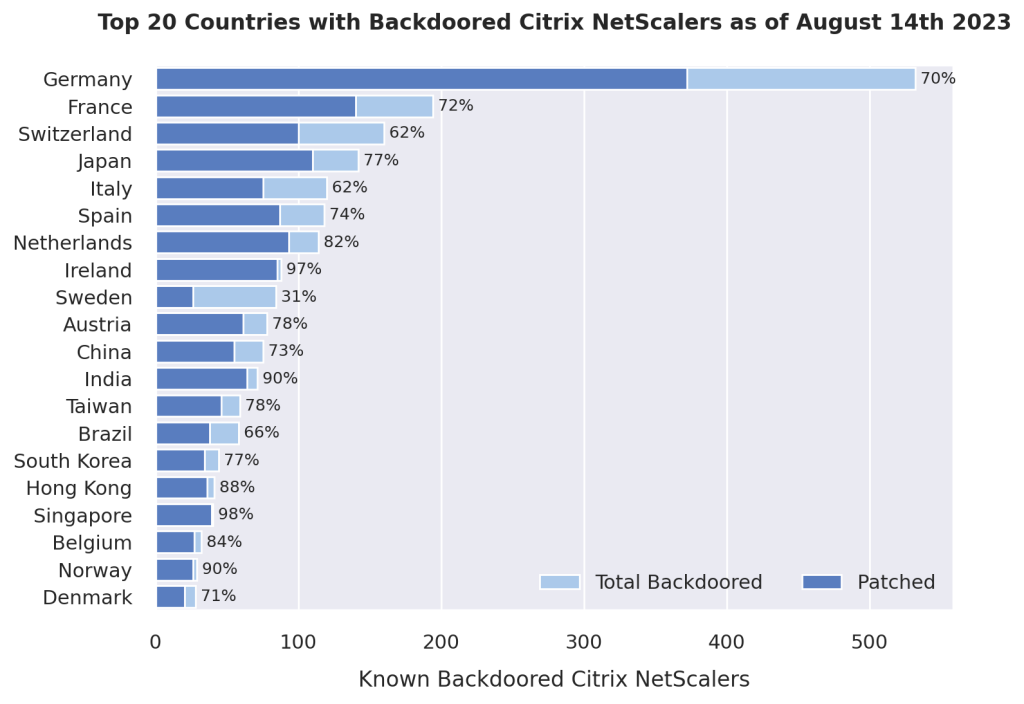
The Dutch Institute of Vulnerability Disclosure notified all impacted organizations on August 10. The cybersecurity firm found that most compromised customers were based in European countries, including France, Germany, and Switzerland. It’s important to note that around 69 percent of the backdoored NetScaler instances were already patched at the time of mass exploitation.
“This indicates that while most administrators were aware of the vulnerability and have since patched their NetScalers to a non-vulnerable version, they have not been (properly) checked for signs of successful exploitation. Thus, administrators may currently have a false sense of security even though an up to date Netscaler can still have been backdoored,” NCC Group noted.
Mandiant releases new script to detect hacked Citrix ADC, Gateway devices
NCC Group recommends organizations to check for the known indicators of compromise (IOCs) on NetScaler devices. The cybersecurity firm Mandiant has also released a script to help administrators scan their Citrix appliances for post-exploitation activity. It’s recommended to perform a complete forensic examination and evaluate the scope of the security breach.
Mandiant says IT admins can download the CVE-2023-3519 scanner tool from its GitHub repository. It’s compatible with Citrix ADC and Citrix Gateway versions 12.0, 12.1, 13.0, and 13.1.


