Enable IP between VPC Instances in Amazon Web Services
In this easy Ask the Admin, I’ll show you how to configure security groups in Amazon Web Services (AWS) so that EC2 Virtual Private Cloud (VPC) instances can communicate with each other. In Manage IP Addressing with Virtual Private Clouds in Amazon Web Services on the Petri IT Knowledgebase, I provisioned virtual machines (Elastic Compute instances) in a VPC, so that the VMs would be assigned to the same internal private IP address each time they are started. This is especially important for servers that require a static IP address, such as Active Directory domain controllers.
In that article, I created an Internet gateway for the VPC and set up a new security group that would allow traffic from the Internet to reach instances on TCP port 3389 for Remote Desktop access. Security groups are locked down by default. Because security group configuration is applied to each instance, communication between instances in the same VPC is prevented. In AWS, network ACLs control the traffic allowed to reach VPC subnets, and security groups are used to protect instances.
Add Rules to a Security Group
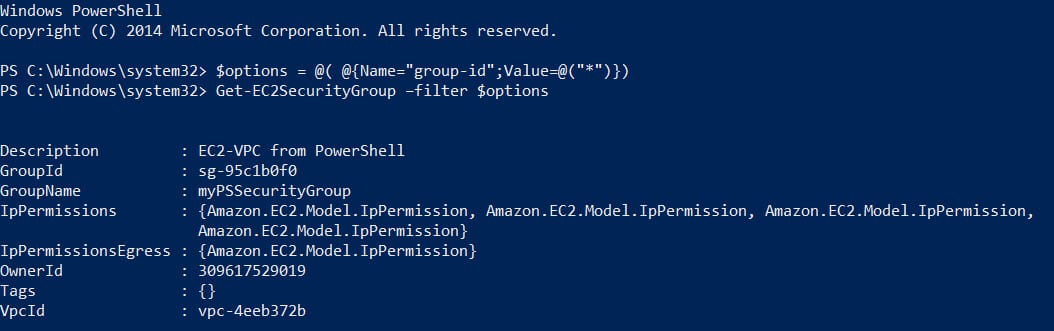
For the purposes of this article, I’m going to assume that you already have a security group in your VPC, as described in the article mentioned above. If not, create a new group that allows RDP access to your instances. Don’t forget that you can have more than one security group, and instances connected to a VPC can be associated with different security groups. You will also need to have the AWS Tools for Windows PowerShell installed on your PC as described here in Provision Windows Server in Amazon Web Services using PowerShell. First, I need to establish the GroupId for myPSSecurityGroup, which is the security group I created when provisioning the VPC and instances.
$options = @( @{Name="group-id";Value=@("*")})
Get-EC2SecurityGroup –filter $options
Make a note of the GroupId that corresponds to your security group from the output of the previous commands. Now I know the GroupId for myPSSecurityGroup, I’ll put it into a variable:
$groupID = “sg-95c1b0f0”
I also know that my VPC private subnet is 10.0.0.0/16, so I can allow all inbound TCP traffic from any address in this range.
$cidrBlocks = New-Object 'collections.generic.list[string]'
$cidrBlocks.add("10.0.0.0/16")
$ipPermissions = New-Object Amazon.EC2.Model.IpPermission –Property @{IpProtocol = “tcp”; FromPort = “0”; ToPort = “65535”; IpRanges = $cidrBlocks}
Grant-EC2SecurityGroupIngress –GroupID $groupID -IpPermissions @($ipPermissions)
Now I’ll repeat that for UDP, keeping the address block the same.
$ipPermissions = New-Object Amazon.EC2.Model.IpPermission –Property @{IpProtocol = “udp”; FromPort = “0”; ToPort = “65535”; IpRanges = $cidrBlocks}
Grant-EC2SecurityGroupIngress –GroupID $groupID -IpPermissions @($ipPermissions)
Finally, I’ll configure ICMP echo requests so that I can use the ping command for troubleshooting. In FromPort, I’m specifying the ICMP type, which is 8. The ToPort value is not used for ICMP, so must be set to -1.
$ipPermissions = New-Object Amazon.EC2.Model.IpPermission –Property @{IpProtocol = “icmp”; FromPort = “8”; ToPort = “-1”; IpRanges = $cidrBlocks}
Grant-EC2SecurityGroupIngress –GroupID $groupID -IpPermissions @($ipPermissions)
Check Security Group Settings
Now check that the settings above have been applied to the group correctly.
($groupid | Get-EC2SecurityGroup).IpPermissions
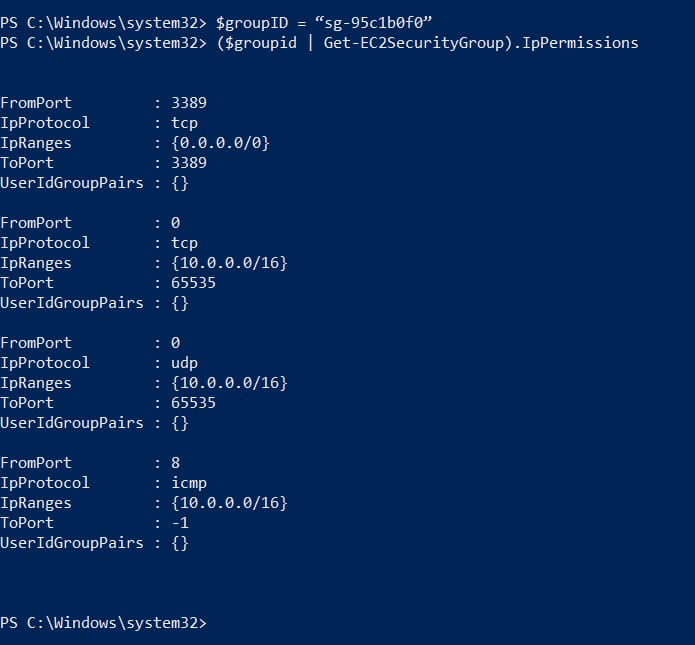
You should now be able to ping and communicate using IP between any instances in your VPC that belong to the security group determined in the $groupID variable.



