Configure Single Sign-On to Enterprise Apps using Azure Active Directory
In today’s Ask the Admin, I’ll show you how to set up single sign-on access for your Azure Active Directory users to apps such as Facebook and LinkedIn.
Azure Active Directory (AAD) can be used to provide employees with single sign-on authentication for corporate accounts in applications like Salesforce and Facebook, and apps developed in-house. Microsoft calls this feature password-based single sign-on for shared accounts, and it supports apps that have HTML log in pages. It works by logging in authenticated AAD users to designated apps by securely passing credentials stored in AAD to the app, meaning users only need remember their AAD password.
The principal advantage of using password-based single sign-on is that passwords for corporate accounts don’t have to be changed when employees leave your company, forcing remaining users to memorize a new password. Furthermore, security is improved by guarding the corporate account credentials from employees, and AAD multifactor authentication can provide additional protection for systems that might not otherwise support this additional protection.
Configure Single Sign-On
To complete the instructions in this article, you’ll need to have an Active Directory instance configured in Azure, and at least one account in a supported gallery app, such as Facebook, Twitter, or LinkedIn. Log in to the Azure Management Portal and follow the instructions below:

- In the blue panel on the left of the management portal, scroll down and click ACTIVE DIRECTORY.
- Click the Active Directory instance you want to configure on the right.
- Click APPLICATIONS at the top of the instance window.
- Click the ADD icon in the taskbar at the bottom of the portal.
- In the What do you want to do? dialog, click Add an application from the gallery.
- In the APPLICATION GALLERY dialog, browse or search for the app you’d like to add, and then click the tick icon in the bottom right corner.

- You’ll now see a message in the management portal that Your app has been added! To assign access to an AAD user, click the green Assign users button.
- Select All users in the drop-down menu to the right of SHOW, and then the tick icon on the right.
- Select one or more users from the resulting list, and click ASSIGN in the taskbar.
- In the Assign Users dialog, check I want to enter LinkedIn credentials on behalf of the user, and then enter the username and password for the shared corporate account.
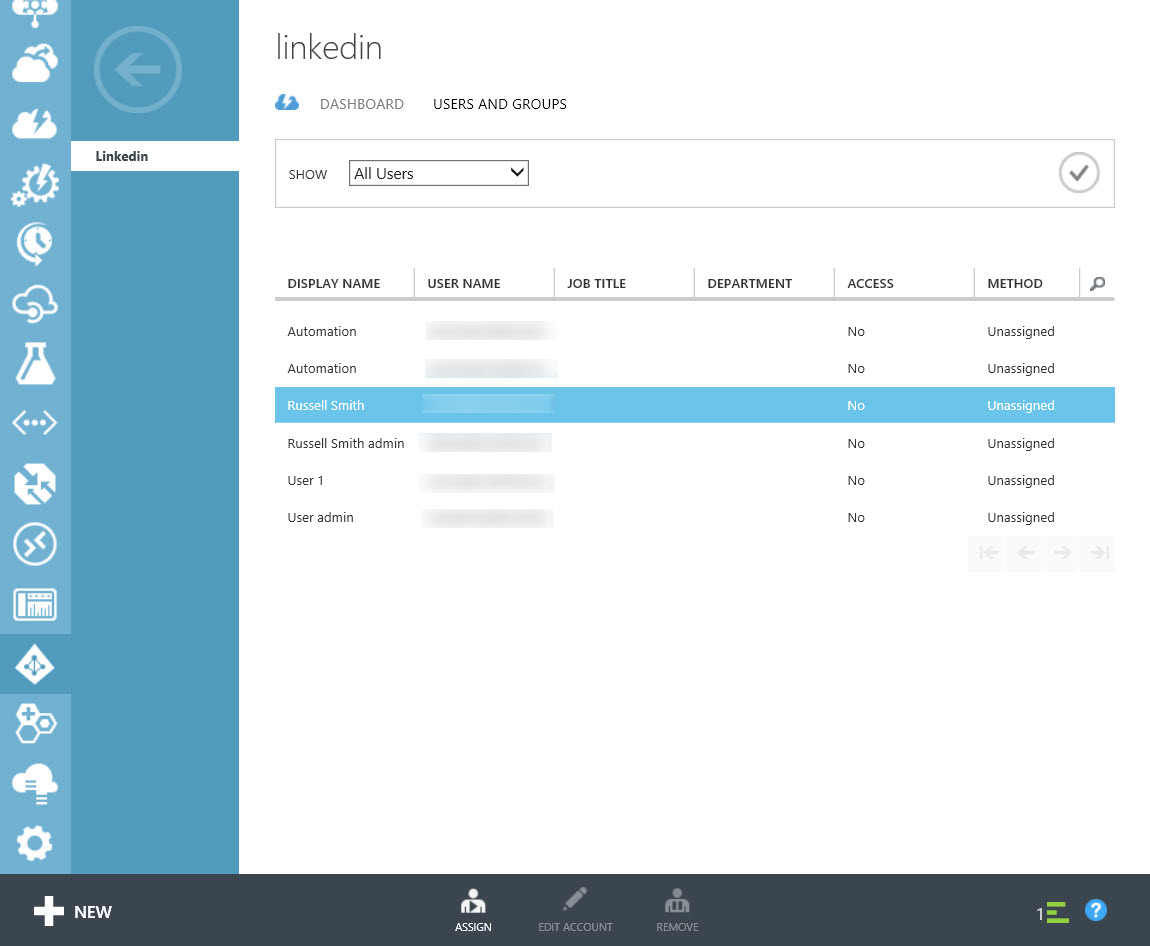
Optionally, you can check I want to enable automatic password rollover. This feature is currently in preview, and automatically changes the password for the corporate account according to a schedule you define. If you decide to let AAD manage the password for the corporate account, the only way to retrieve your login credentials is to use the password reset system provided by the application. Additionally, when password rollover is enabled, the app should only be accessed using the Access Panel, or single sign-on link for the app.
- Click the tick icon to continue. If you enabled password rollover, you’ll see a second screen where you can set the rollover frequency, which is four weeks by default. Click the tick icon again once you’re done.
Wait for the user to be assigned access. You’ll see a message when the operation is complete at the bottom of the management portal window.
Launch Apps using the Access Panel
Now that an AAD user has been assigned access to an app using a shared corporate account, they can use the Access Panel or use My Apps for Android or iOS devices to access the app.
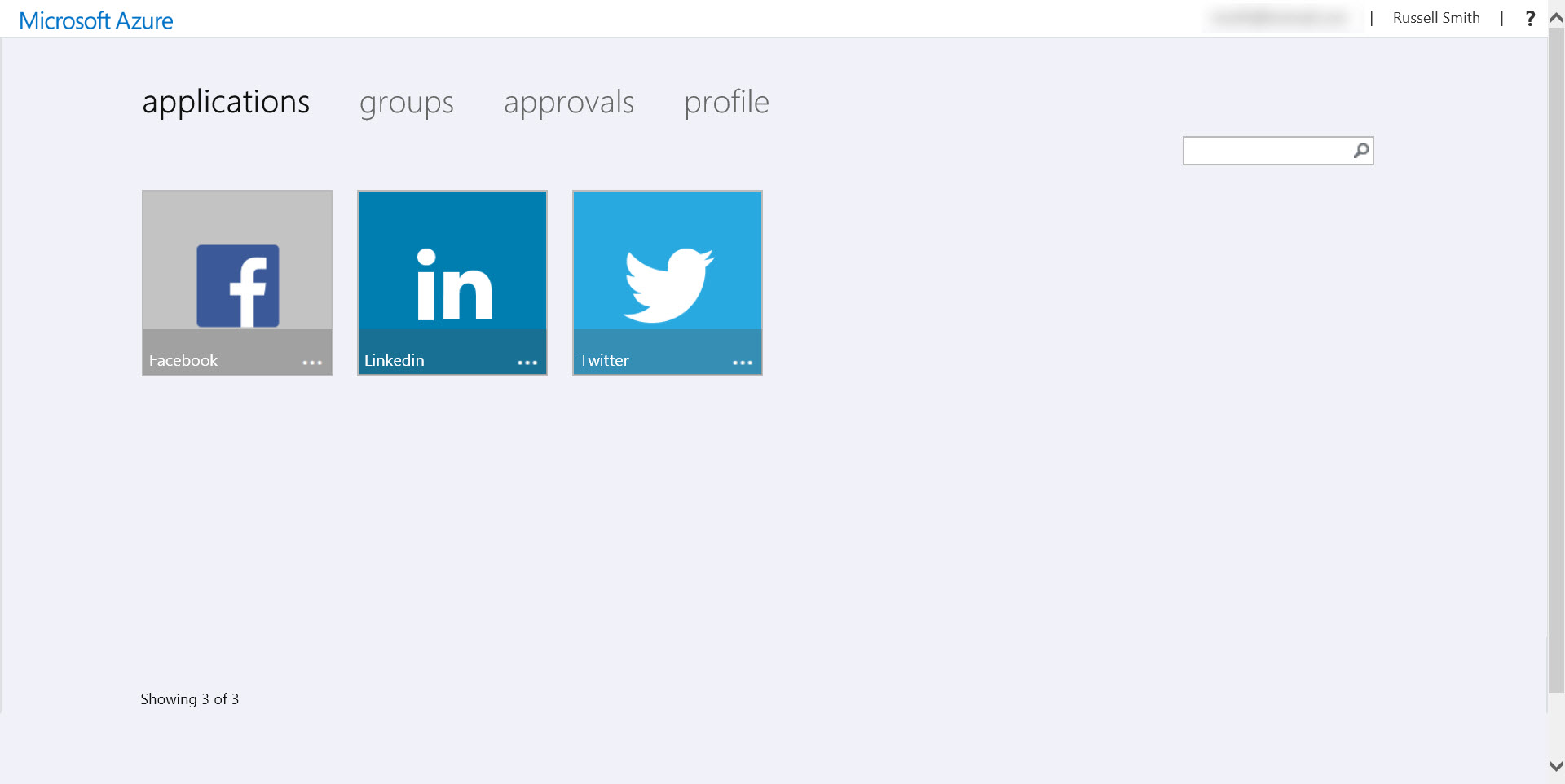
When using the Access Panel for the first time, users will be prompted to download and install the Access Panel extension, available for Internet Explorer, Firefox and Google Chrome. The extension requires local administrative privileges to install, and the browser must be closed while the extension is installing. Internet Explorer users will be prompted to enable the extension once the installer has completed.
In the Access Panel, users see a series of tiles for apps to which they’ve been assigned access. Click on an app, and a new tab will open where the user is automatically logged in using the shared credentials stored in AAD.



