
Key Takeaways:
- US Cybersecurity and Infrastructure Security Agency (CISA) has raised a red flag about a critical vulnerability in Citrix ShareFile.
- The flaw could be exploited by an unauthenticated attacker to compromise cloud-based Citrix ShareFile storage zones controllers.
- CISA has directed all federal agencies to apply patches for the vulnerability by September 6, 2023.
US Cybersecurity and Infrastructure Security Agency (CISA) has warned about a critical vulnerability present in Citrix ShareFile. CISA has mandated that all federal agencies undertake necessary measures to apply patches for the security flaw by September 6, 2023.
Citrix ShareFile is a cloud-based file sharing and storage platform that enables organizations to securely store, sync, and share files and documents. The service provides a secure environment to manage and share files with internal and external users. Citrix ShareFile offers several features such as access controls, file synchronization, audit trails, encryption, as well as integration with different productivity tools.
Citrix researchers first disclosed the security vulnerability (tracked as CVE-2023-24489) back in June 2023. It ranks 9.8 out of 10.0 on the CVSS scale, making it critical in severity. The researchers warned that the flaw could let an unauthenticated attacker remotely compromise the cloud-based Citrix ShareFile storage zones controllers. The tool allows organizations to store and manage files in on-premises environments.
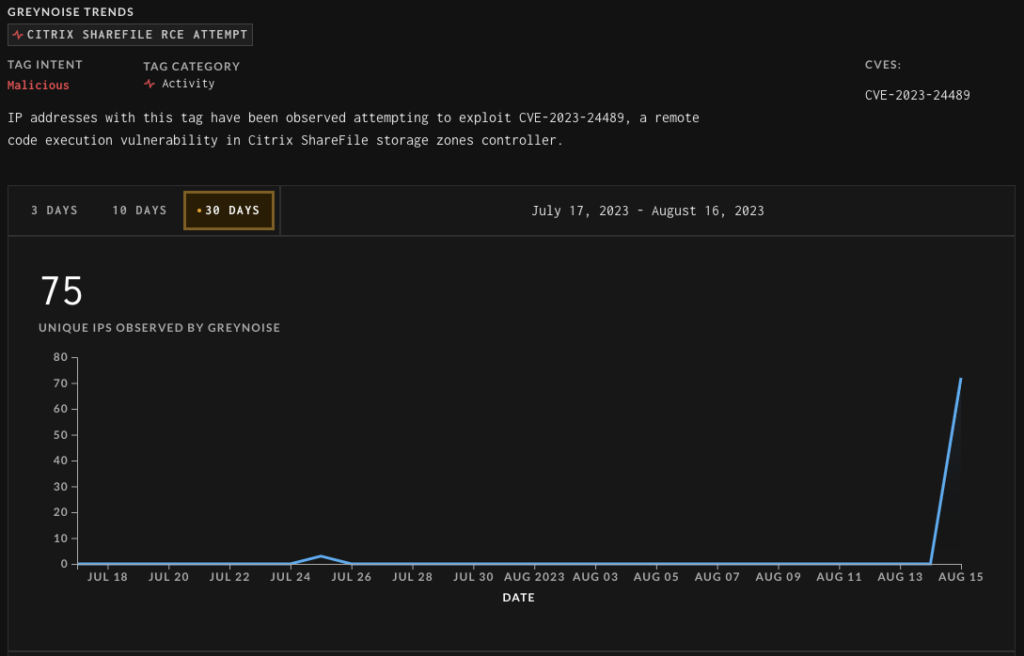
GreyNoise detects a spike in attacker activity
The Threat intelligence startup GreyNoise observed a significant spike in exploitation activity this week. As it turns out, the hackers can exploit a design flaw in the implementation of ShareFile’s AES encryption to target businesses.
“Attackers can exploit this vulnerability by taking advantage of errors in ShareFile’s handling of cryptographic operations. The application uses AES encryption with CBC mode and PKCS7 padding but does not correctly validate decrypted data.” GreyNoise explained. “This oversight allows attackers to generate valid padding and execute their attack, leading to unauthenticated arbitrary file upload and remote code execution.”
GreyNoise has published proof of concept (PoC) exploits for the vulnerability on GitHub. It’s recommended that organizations should upgrade to the latest version to prevent hackers from leveraging the flaw in future attacks.


