Understanding How Azure Sentinel and Entity Behavior Analytics Deliver Actionable Intelligence
- Blog
- Compliance
- Post
At Ignite in September, Microsoft announced the availability of User and Entity Behavior Analytics (UEBA) in preview for Azure Sentinel. UEBA takes user data from Azure Active Directory (AD), and combined with logs and alerts from connected data sources, it builds baseline behavioral profiles for entities like Azure AD users, hosts, IP addresses, and applications.
Using behavior analytics and machine learning, UEBA can identify unusual activity and help SOC teams identify if there is a compromised entity or a malicious insider. Microsoft says that additionally, UEBA can work out the relative sensitivity of your assets, peer groups of assets, and tell you the possible impact if a given asset gets compromised. Microsoft calls this an asset’s ‘blast radius’. With the extra information that UEBA provides, SOC teams can better prioritize investigation and incident response.
Before using the UEBA preview, you need to enable synchronization of Azure AD users and entities to create profiles for them in Sentinel. Once that’s done, configure some data sources to populate Sentinel with data like security logon events, Azure AD audit and sign-in logs, and Azure activity logs. The data sources you select will be processed, enriched, and profiled by UEBA.
For more information on how to set up Azure Sentinel and add data sources, check out Monitor Windows Server Security Using Azure Sentinel Part 1 – Set Up a Workspace and Data Connector on Petri.
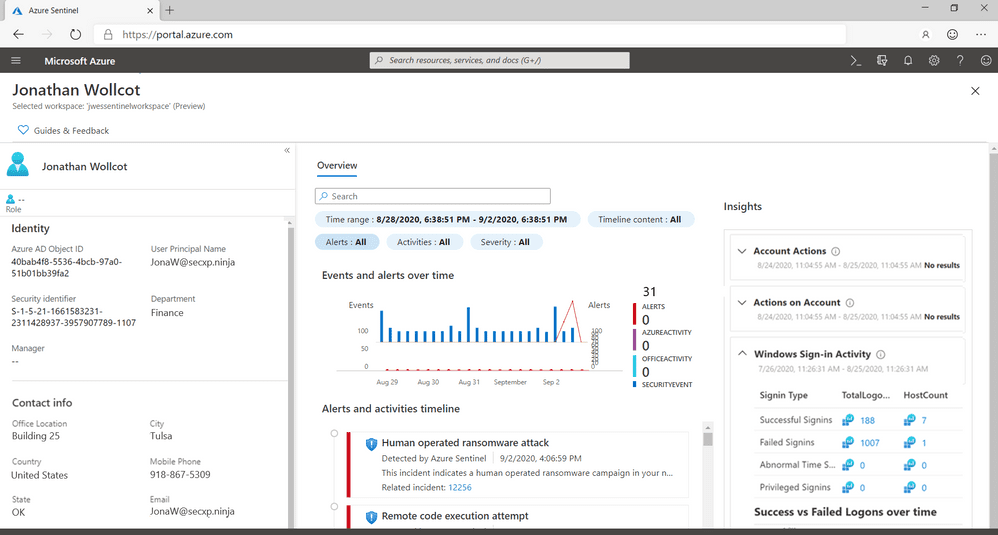
The profiles that UEBA builds provide a unified view of your organization’s entities. The SOC team can search by entity name, or another identifier, to open an entity profile. At the time of writing, entities are limited to users and hosts. But Microsoft says that there will be more entities available in the future. Each entity has an entity page, which is a datasheet containing useful information that includes a timeline of important events and insights on entity behavior.
UEBA workbook and Investigation Priority Score
As part of the preview, Microsoft has also released a UEBA workbook that is designed to aid SOC analysts with user investigation. The workbook is based on user-related incidents, alerts, and unusual behavior. The workbook shows analysts the top user to investigate. For example, the user might be suspected as compromised or considered an insider threat because the user’s behavior was different from its base profile.
Microsoft says that all its behavior and configuration anomalies are based on real-life attack scenarios and they are mapped to the MITRE ATT&CK framework. Each ‘anomaly’ is given an ‘Investigation Priority Score’ that helps to determine the likelihood of a user performing a specific activity. The score is based on behavioral learning of the user and the user’s peers.
UEBA enhances raw log data to make advanced threat hunting easier
UEBA adds useful information to raw log data and then updates customers’ log analytics so that SOC analysts can run complex queries easily. The results have contextual and behavioral information included in them, and all the hard work is done by the backend instead of the analyst. The Guides & Feedback panel provides analysts with useful information on how to make best use of UEBA, including the ability to share feedback with Microsoft’s Sentinel team via the user voice platform.