
Atlassian has released new security updates to fix a critical flaw affecting its Confluence Server and Data Center products. The vulnerability, tracked as CVE-2022-26134, allows for unauthenticated remote code execution on unpatched servers.
The zero-day security flaw was disclosed by security company Volexity last week, and it impacts all supported versions (except those hosted on Atlassian Cloud) of the products. The researchers found that malicious actors are currently exploiting the vulnerability to install the Chopper webshell and other malware. This prompted the Cybersecurity & Infrastructure Security Agency (CISA) to encourage federal agencies to block all internet access to Confluence servers on their networks.
“The OGNL injection vulnerability allows an unauthenticated user to execute arbitrary code on a Confluence Server or Data Center instance. All versions of Confluence Server and Data Center prior to the fixed versions listed above are affected by this vulnerability,” Atlassian noted in its security advisory.
Security researchers also published a proof of concept (PoC) for the critical CVE-2022-26134 vulnerability on June 3. The proof of concept code demonstrates the process of creating new admin accounts, pushing DNS requests, collecting sensitive data, as well as generating reverse shells.
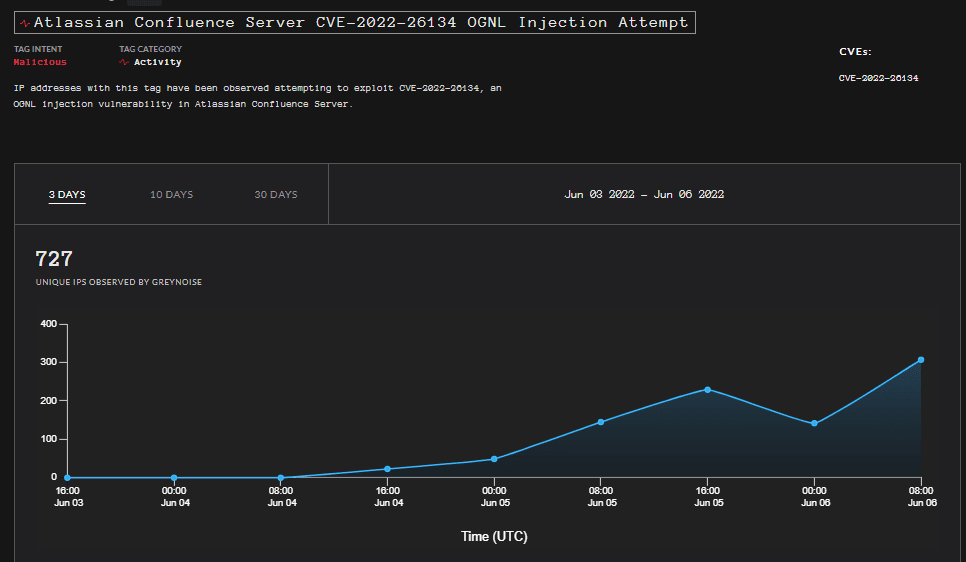
Additionally, the CEO of cybersecurity company GreyNoise revealed on Twitter that 727 unique IP addresses have already attempted to breach into Internet-exposed and unpatched Confluence servers.
Atlassian recommends customers to patch Confluence servers
Atlassian has rolled out security patches to address the flaw in versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, and 7.18.1. The company has advised all enterprise customers to upgrade to the latest version of Confluence. Meanwhile, IT administrators who cannot apply the patches immediately should update some JAR files on their Confluence servers.
It is important to note that this isn’t the first time a security exploit has been identified in Atlassian’s Confluence server. Last year, US Cybercom issued an alert about the mass exploitation of a high severity remote code execution vulnerability found in Confluence Server and Data Center.



