WireGuard VPN Gets Port to Windows Kernel but Don’t Run Out to Replace IPsec or OpenVPN
WireGuard is a Virtual Private Network (VPN) protocol that was first developed in 2016 by security researcher Jason A. Donenfeld. It was originally conceived for Linux. And as of kernel version 5.6, which was released in March 2020, WireGuard is integrated into Linux.
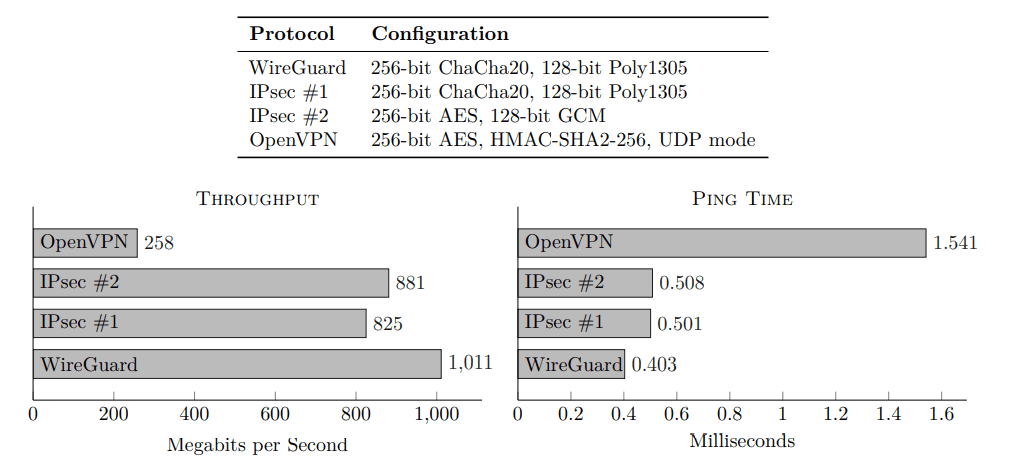
Designed to be a lightweight alternative to VPN protocols like IKEv2, OpenVPN, IPsec, and L2TP, WireGuard uses less than 4000 lines of code. And when compared to IPsec and OpenVPN, WireGuard claims that it delivers faster throughput and ping time, especially when compared to OpenVPN.
In addition to better performance, the less complex codebase means potentially fewer bugs, faster connection times, and better compatibility with IoT and small devices, such as routers and mobile phones. WireGuard also supports the latest encryption protocols, like BLAKE2, Curve25519, ChaCha20, and Poly1305.
Incorporating WireGuard into the Linux kernel brought many performance benefits. OpenVPN, for example, which works in the user-mode space, must translate each network request before it can be processed. Kernel-mode drivers and applications, like WireGuard on Linux, bypass the ‘context-switching’ of user-mode processes, leading to better performance.
WireGuard is coming to the Windows kernel
Ok, not quite in the same way as on Linux. WireGuard is being ported to a kernel-mode (kernel space) application on Windows, bringing the same performance benefits that are seen on Linux today.
Microsoft has nothing to do with the project. And WireGuard code isn’t being integrated directly into the Windows kernel. But the new codebase will be implemented into the Windows network stack – in the same way it happens today on Linux, OpenBSD, and FreeBSD – by means of a kernel-mode driver.
Jason A. Donenfeld launched a project at the beginning of August to rewrite WireGuard as a kernel-space application on Windows. The WireGuardNT project is currently in development and the author hopes that it will help WireGuard be adopted on Windows for more serious tasks.
Even at this early stage, it has been reported that WireGuardNT is much faster than the current WireGuard user-space implementation on Windows. And where current WireGuard users on WiFi can experience considerably lower performance than devices connected to ethernet, WireGuardNT levels out the playing field.
But don’t rush to implement WireGuard – it’s not for all VPN use cases
WireGuard may be a performant and a lightweight VPN solution. But it also misses many of the features that organizations expect in an enterprise-ready VPN solution. Firstly, WireGuard is unlikely to replace your current site-to-site VPN protocol because the big enterprise players, like Cisco, don’t support it.
And secondly, WireGuard isn’t going to be good for remote workers because it lacks so many features. There is no support for dynamic IP addresses. And while some consumer VPN products have got around this limitation with their own creative solutions, it is a problem for traditional VPN use in organizations. Here are some other features that IPsec VPNs have that WireGuard doesn’t yet support:
- Extensible cryptography
- User authentication with a password or SIM card with Extensible Authentication Protocol (EAP)
- A predefined way to configure and share keypairs
- Cipher negotiation
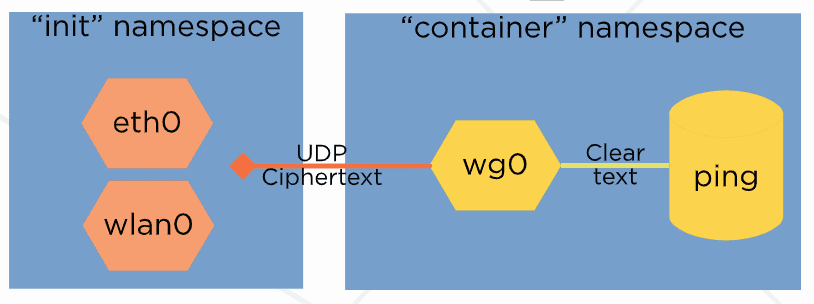
One potential exception to enterprise use of WireGuard is with containers. According to WireGuard’s website:
WireGuard uses a UDP socket for actually sending and receiving encrypted packets. This socket always lives in namespace A – the original birthplace namespace. This allows for some very cool properties. Namely, you can create the WireGuard interface in one namespace (A), move it to another (B), and have cleartext packets sent from namespace B get sent encrypted through a UDP socket in namespace A.
It’s always nice to see technologies that were developed for Linux get ported to Windows with proper attention to performance. And while WireGuard has its place in the VPN market, it isn’t and was never meant to replace the enterprise-ready VPN protocols that organizations rely on today more than ever.