Protecting Microsoft 365 from Ransomware Attacks with Filewall

This year, especially as companies rapidly pivot to adopting cloud services to meet remote working needs, cybersecurity is a topic that should be at the forefront of people’s minds.
Ransomware attacks, or targeted attempts to compromise the internal systems of companies are becoming increasingly common. Email is used as a vector to sneak malware into an organization, gain the valid credentials of users, and implant malware to allow an outside attacker to rapidly exploit further vulnerabilities to gain complete control of corporate systems.
A vast amount of reactive digital transformation has taken place over the last year, and many companies are now attempting to catch up with cybersecurity. For some, it is too little, too late, and although they have followed good guidance such as recommendations provided by Secure Score, providing additional protection against complex threats arriving via email is essential.
Unfortunately, I have seen the effects of this first-hand at several organizations that have not thought about the complete threat vectors for their operations. Because of this, some of these companies have lost control over their on-premises estate and spent weeks regaining access, and months later are still implementing the type of controls they would have liked to implement prior to the attack.
Using third-party products to supplement Exchange Online Protection or Microsoft 365 Defender
A major frustration with looking for effective email add-on products is most solutions have a traditional model for protection that does not fit with Microsoft 365. Exchange Online Protection includes protection against known malware, and Microsoft 365 Defender includes phishing, URL, and attachment detonation. Therefore, if you want to provide a higher level of email attachment security, traditional email gateway products duplicate this functionality as well as providing their own, often similar products.
Additionally, as these act as a gateway for email in and out of the organization, they are not well suited to protecting against internal email threats.
A modern solution that can provide protection above and beyond Exchange Online Protection, and supplement Microsoft 365 Defender, needs to work in a modern, cloud-based model, and integrate with the product directly rather than sitting at the edge.
This is where the FileWall™ by odix for Exchange Online product sits and works well. FileWall for Exchange is designed to work using Microsoft’s Graph API and integrates directly with the service.
Fundamentally, this makes the integration simpler, as the service does not interfere with email delivery and instead interfaces directly with Exchange Online to perform scanning and remediation.
Filewall for Exchange Online provides the following functionality:
- Content disarm and reconstruction.
- Attachment scanning for internal and external emails.
- Nested scanning in ZIP files and other container-based attachments.
- Scanning and alerting on files disguising their true type.
- One-click deployment via Microsoft Azure or Appsource marketplaces
- Integrated with Microsoft Sentinel
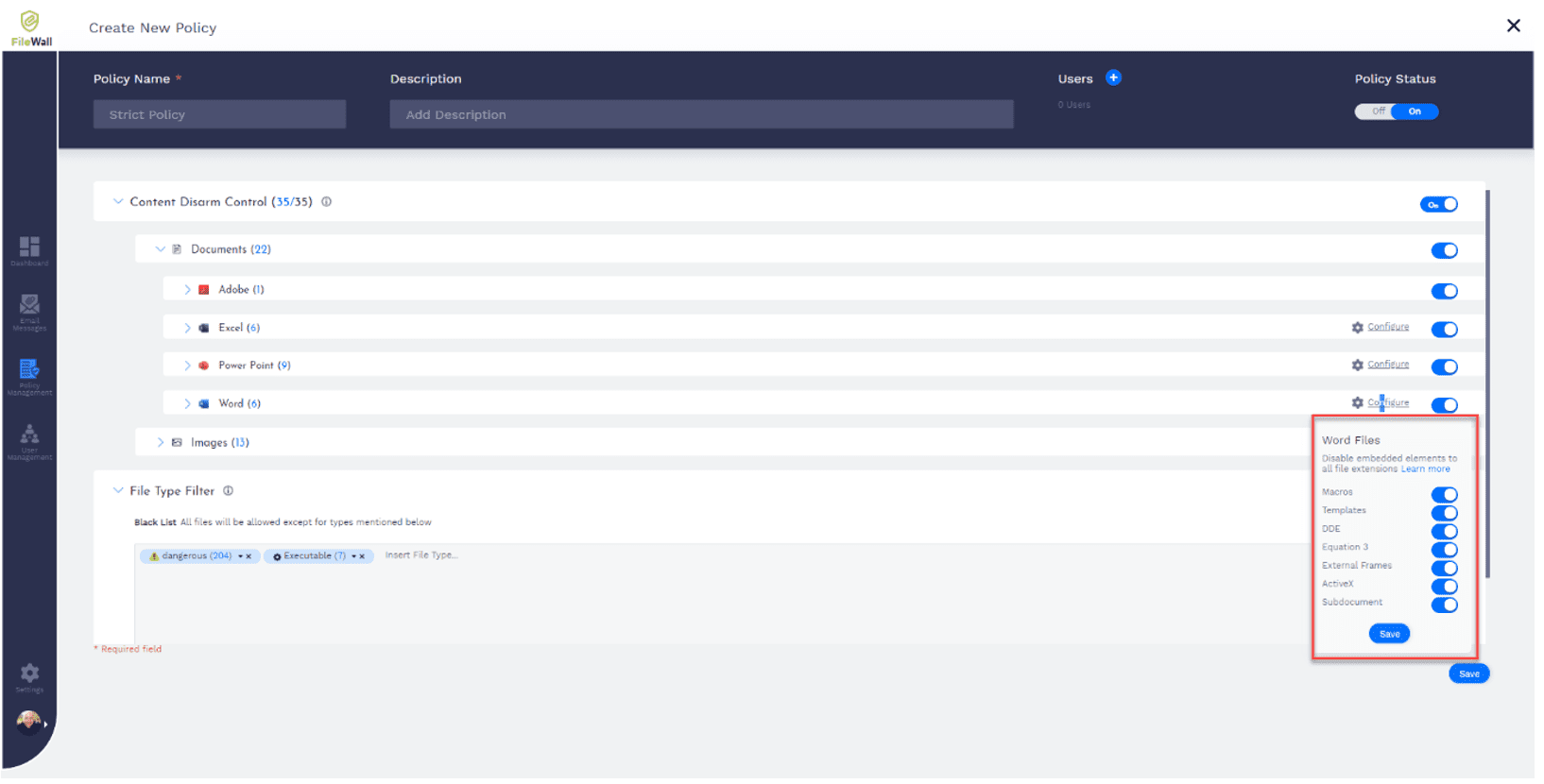
In particular, FileWall’s content disarms, and reconstruction component is particularly useful. What this allows you to do is configure the solution to potentially dangerous elements and common threat vectors and remove it from the attachment without blocking the attachment itself – this is possible because of the flexible and granular controls provided by FileWall.
By using FileWall on its own, the technology is able to remove any potential threat from the attachment once received by Exchange Online, and reconstruct the file without dangerous components.
Real-life protection capabilities in action
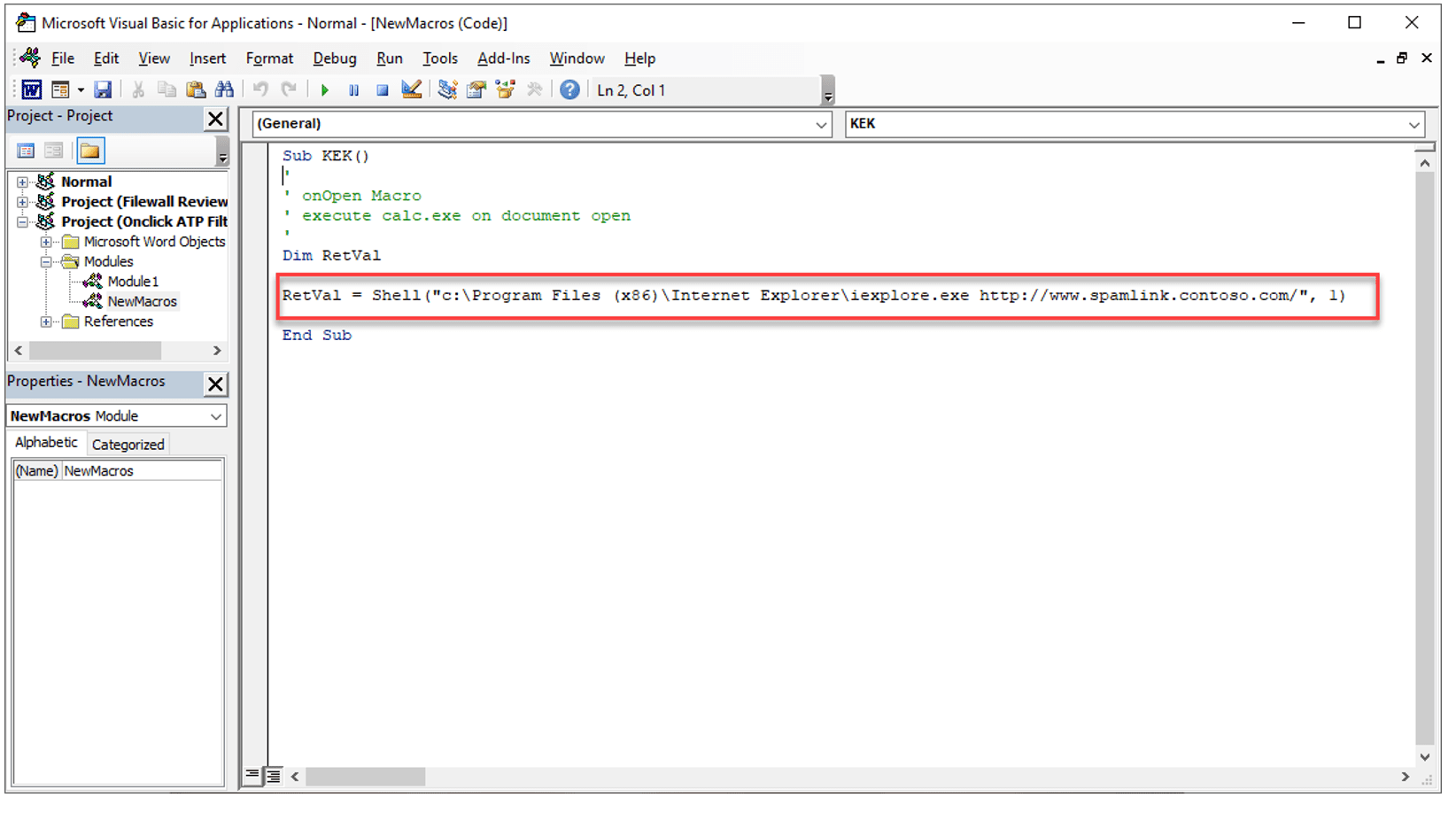
For example, this could include embedded executables or Macros designed to take users to malicious websites. To test this, in a tenant with Microsoft 365 defender’s safe attachments enabled, I created a Word Document with a macro, that when clicked, launched a web browser to Microsoft 365 Defender’s own test malicious URL:
This should be picked up in a similar way to a URL within a document or message, and in theory, you would expect Microsoft 365 Defender too, when opening the document in a sandbox, spot the Macro and its own malicious URL. Unfortunately, it did not which indicates that a malicious actor armed only with a single line of VB code would create a simple Word Document designed to encourage a user to click on a URL that will infect their PC.
Of course, without Microsoft 365 Defender it is far easier for a malicious threat to pass through to a user, and this is where FileWall comes into play.
Using the capabilities to disarm all dangerous content, FileWall achieves two simple things – it removes the possibility of a threat, and it enables a user to continue to receive nearly all attachments by replacing the dangerous content with a sanitized version.
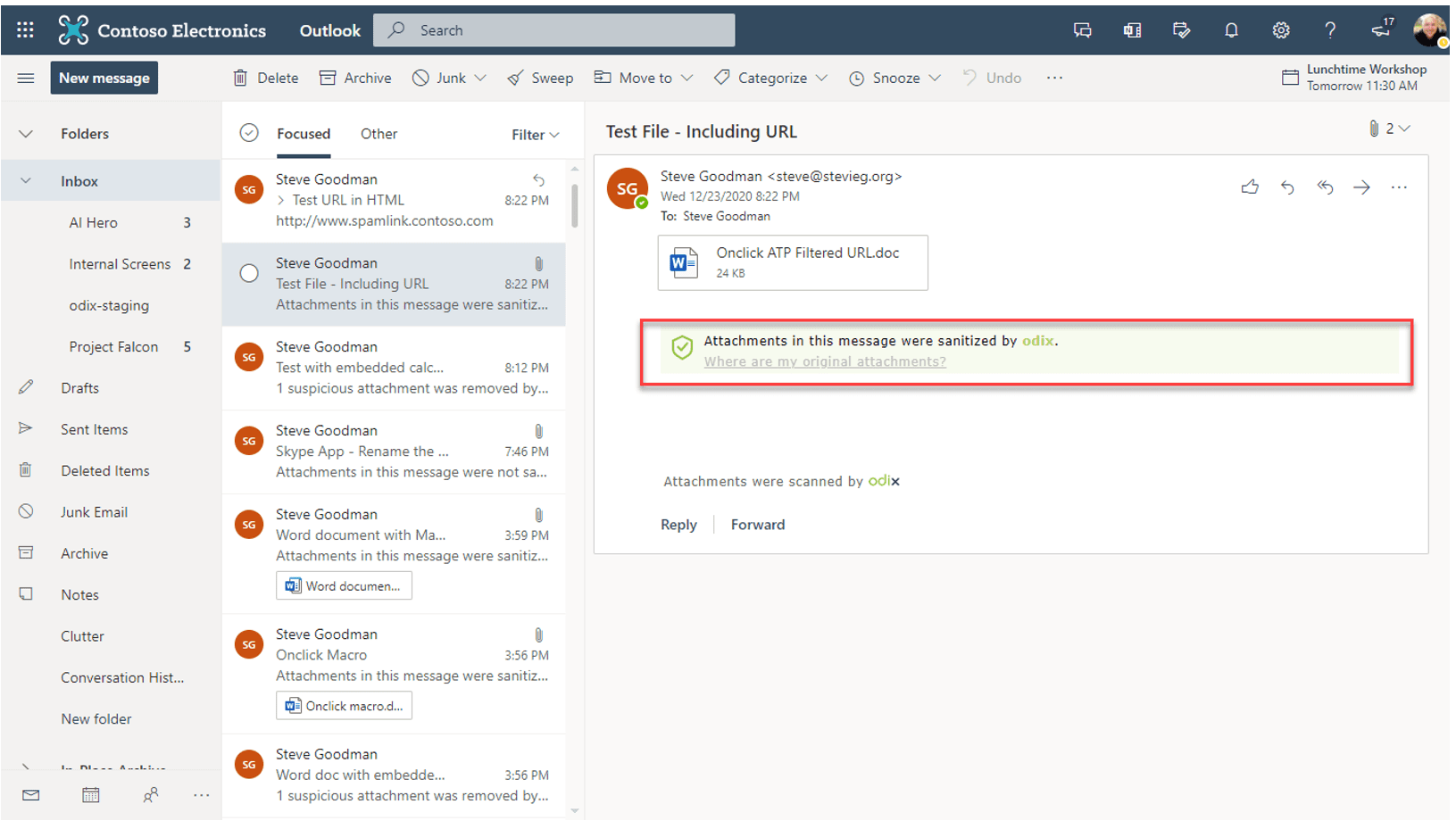
In the example above, the attachment was still received – but all dangerous code was removed. The user was informed this had happened, so if there is a legitimate reason for them to use something, such as a spreadsheet with code in it, IT can examine it first before releasing the document.
From an IT admin’s perspective, the reporting in FileWall is clean and focused on the task. This is a product designed to do one thing well – and as such the administrator portal is focused on the management of policies, users, and reporting on threats.
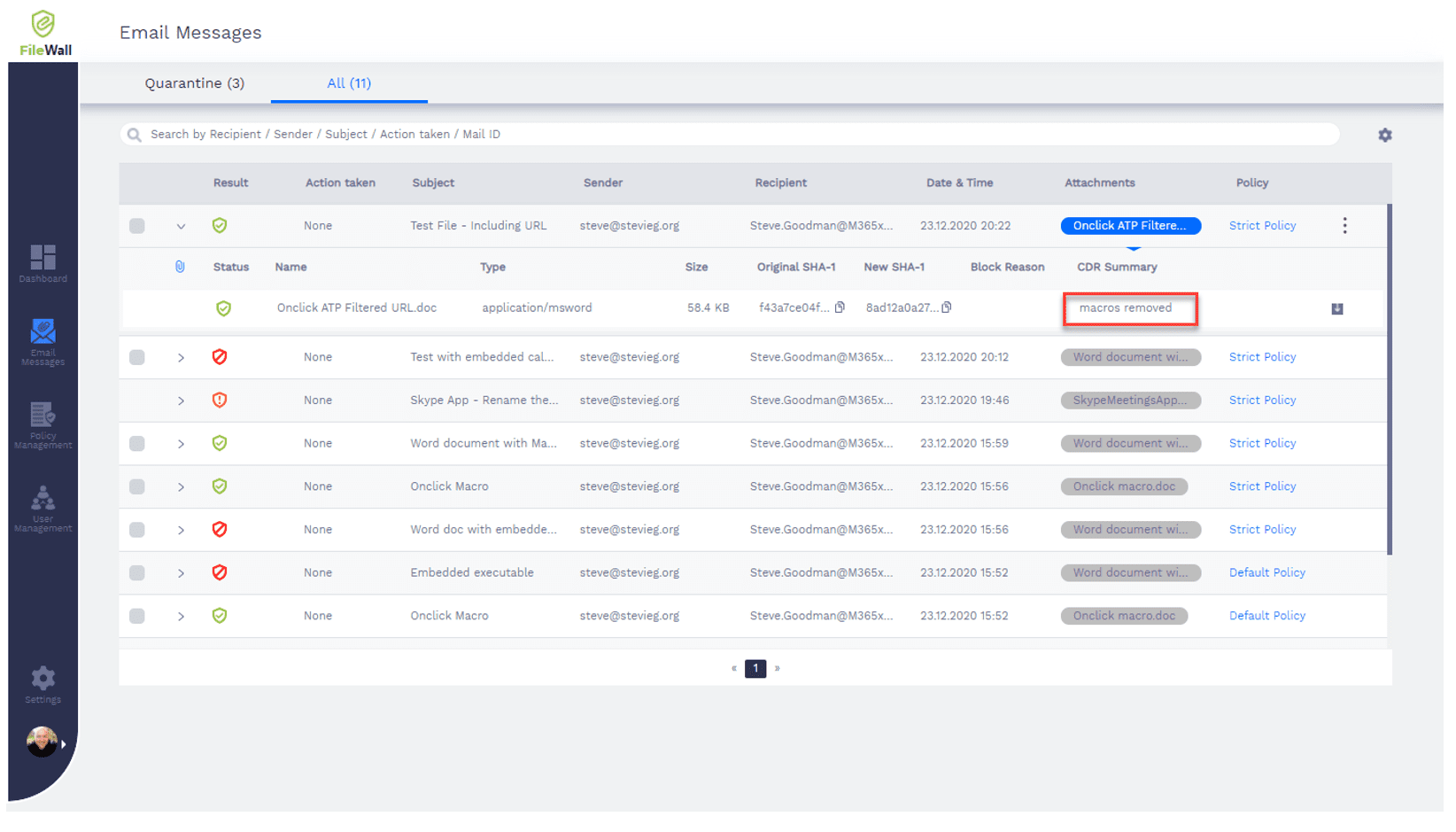
In our above example, we have the ability to drill-down into the scanned threat in its main reporting tab:
This allows us to see information, such as the email subject and recipient, and drill down into the message to see what actions were taken.
As our embedded link to the Microsoft 365 Defender test URL was within a macro, we can see that the macro was removed and the clean message was delivered to the user.
You will also notice that some messages have been quarantined – to comply with policies we’ve set, such as denying the ability for executables to be delivered in email. While Exchange Online Protection will block these, the examples above are those where this protection has been bypassed and FileWall has caught it after it passed through Exchange Online Protection’s defenses.
Final thoughts
Overall, FileWall for Exchange Online is a useful product and particularly suitable for organizations that do not have tools like Microsoft 365 Defender available to them.
While the base Microsoft 365 suite has built-in protection for many threats – such as known malware and alerts for potential phishing messages – these alone are not always sufficient. In particular, organizations without Microsoft 365 Defender will benefit more from FileWall for Exchange than a more expensive email gateway product that will not protect against internal senders. That’s not to say that if you have Defender you should not also take a look at FileWall, having both solutions in-place can help cover any potential gaps that Defender may overlook.
As organizations buy products like FileWall for Exchange, there is more potential as organizations use Teams and OneDrive to share files, for threats like our Macro examples, to propagate via these methods. Because odix is a modern product and uses the Graph API for access, it is a better-suited tool than others on the market to achieve comprehensive third-party protection for Microsoft 365 than its competitors.
This post is sponsored by odix, you can learn more about their Filewall solutions here.