How to Use PowerShell Splatting to Make Code More Readable
- Blog
- PowerShell
- Post
There are a couple of ways you can make your PowerShell code more readable. In this article, I’m going to show you how to use splatting with the New-ADUser cmdlet to do just that, make your code more digestible. For yourself and for others to read.
Splatting can be used with any PowerShell cmdlet that accepts parameters. But in this example, we’ll stick to New-ADUser as it’s a cmdlet most Windows system administrators are familiar with. Here’s an example of a typical New-ADUser command. It’s long, difficult to read, and it never seems to end.
New-ADUser -Name 'Russell Smith' -Enabled $true –GivenName Russell –Surname Smith -Accountpassword (ConvertTo-SecureString PassW0rd! -AsPlainText -Force) -Path:"OU=Accounts,DC=ad,DC=globomantics,DC=uk" -ChangePasswordAtLogon $true -SamAccountName russellsmith –UserPrincipalName [email protected] -City London -Department Infotech
Using backticks for line continuation in PowerShell
One way that you can make the above command easier to read is using backticks. You often see this method used in documentation or script examples. Each line of code ends with a backtick if it will be followed by another line of code. I.e. the final line of code in the command doesn’t require a backtick.
New-ADUser -Name 'Russell Smith' -Enabled $true –GivenName Russell ` –Surname Smith -Accountpassword (ConvertTo-SecureString PassW0rd! -AsPlainText -Force) ` -Path:"OU=Accounts,DC=ad,DC=globomantics,DC=uk" -ChangePasswordAtLogon $true ` -SamAccountName russellsmith –UserPrincipalName [email protected] ` -City London -Department Infotech
Backticks can be problematic when copying and pasting code. If they end up out of place, the code will not work as expected. And some people consider use of backticks bad practice.
PowerShell Splatting
The best way to make the command shorter and easier to read is using splatting. Define the parameters you want to use in a separate code block and then pass them to the cmdlet as shown below. Each parameter is separated using a semicolon.
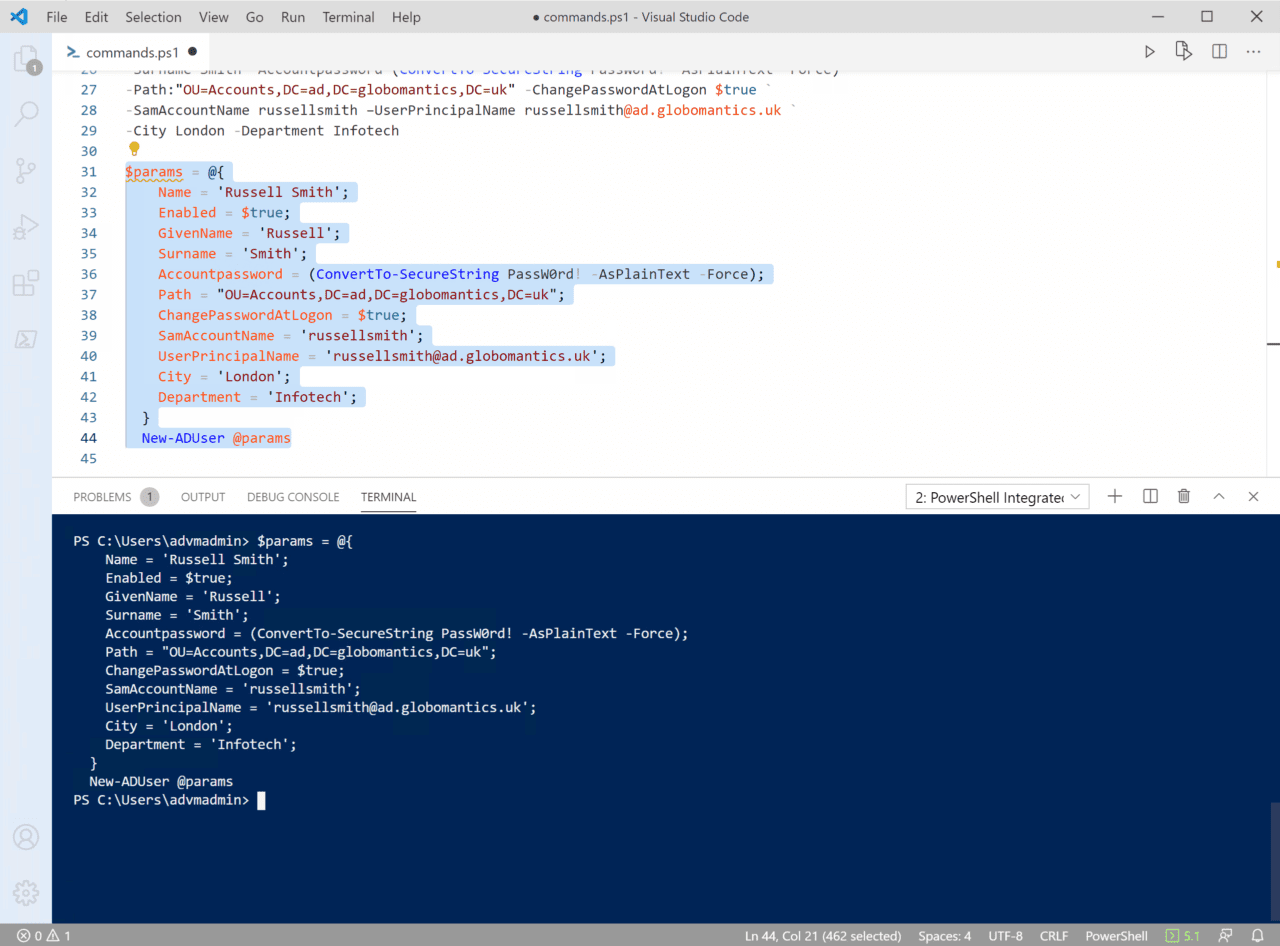
$params = @{
Name = 'Russell Smith';
Enabled = $true;
GivenName = 'Russell';
Surname = 'Smith';
Accountpassword = (ConvertTo-SecureString PassW0rd! -AsPlainText -Force);
Path = "OU=Accounts,DC=ad,DC=globomantics,DC=uk";
ChangePasswordAtLogon = $true;
SamAccountName = 'russellsmith';
UserPrincipalName = '[email protected]';
City = 'London';
Department = 'Infotech';
}
New-ADUser @params
The disadvantage of splatting is that you can’t use tab completion to determine what parameters can be used with a PowerShell cmdlet. So, if you are not sure what parameters to use, you might want to start by writing your command in the traditional long-form method as shown at the beginning of this article and then reformat it to use splatting.
It’s also worth noting that if you decide to use splatting, you’ll need to enclose parameter values in single quotes regardless of whether they include a space. For example, -Name ‘Russell Smith’ must always be enclosed with single quotes because it contains a space.
In a traditional PowerShell command, -GivenName Russell doesn’t need to be enclosed because there is no space in the string. But when using splatting, strings must always be enclosed.