SharePoint Online, OneDrive for Business, and Azure B2B Collaboration
Unexpected Side Effect of SharePoint Sharing
Recently I shared a document in a SharePoint document library with two Microsoft employees. Shortly afterwards, I noticed that Office 365 had created guest user accounts for the Microsoft employees in my tenant. This was a little surprising, but it’s the future norm.
Guest user accounts are heavily used by Office 365 Groups, Teams, and Planner to allow external access to their resources. Built on the Azure B2B Collaboration API, the implementations of guest user access in these applications is enormously successful and one of the reasons why Teams, in particular, has experienced such rapid growth.
SharePoint’s Route to Secure Sharing
SharePoint Online and OneDrive for Business have used different mechanisms for secure external sharing, notably one-time passcodes (OTP) introduced in 2017. In June 2018, OneDrive for Business started to create guest accounts when sharing happened with users in other Office 365 tenants.
One problem that’s always existed is the variety of possible sharing recipients. These can be broken down into four main categories:
- People inside the same tenant.
- People in another Office 365 tenant.
- People who have a Microsoft Services (MSA) account. For example, an Outlook.com account.
- People with an account in another directory.
Because the accounts belong to the same Azure Active Directory instance, secure sharing with someone inside the same tenant poses no problems. The same is largely true for accounts belonging to other Office 365 tenants, Microsoft Service Accounts, or sites that use Azure Active Directory but don’t have Office 365. In these cases, Microsoft runs the relevant directories and can make sure that guest access between tenants is a seamless affair.
Sharing with people whose account is in a non-Microsoft directory poses extra challenges of authentication and validation. SharePoint Online and OneDrive for Business use OTP to overcome the problem. If someone can’t respond with a time-limited code sent to their mailbox, then they can’t access the content shared with them.
Secure Sharing via Guest Accounts
What’s happening now is that Microsoft is on the road to more general use of guest user accounts as the basis for secure sharing. As explained in a “what’s new” document about external sharing published in July, sharing recipients with accounts in other Office 365 tenants will go through a OTP challenge to prove their identity and thereafter use guest accounts automatically created for them in the host tenant. This is what happened to create the guest accounts for the two Microsoft employees in my tenant.
Moving forward, SharePoint Online and OneDrive for Business will have an even deeper integration with Azure B2B collaboration (now in preview and accessible to all tenants except those in sovereign clouds). The integration delivers several advantages, such as removing the need for external recipients to have an MSA account and supporting federated authentication with the Google directory. Once the integration with Azure B2B collaboration becomes generally available, guest user accounts will be created for all types of sharing recipient and we’ll end up with the situations described in Table 1.
| Target Sharing Recipient | Sharing Steps | Guest account created |
| Microsoft (MSA) account | Sharing link sent.
User goes through account validation process. Sharing happens. |
Yes |
| Account in another directory (for example, Zoho Mail or Gmail) | Sharing link sent.
User redeems OTP. Sharing happens. User must redeem new OTP for each session. |
Yes |
| Account in another Office 365 tenant, or Azure Active Directory tenant without Office 365 (like Yandex.com) | Sharing link sent.
User redeems OTP. Sharing happens. User doesn’t need OTP for future access. |
Yes |
Table 1: Sharing in SharePoint Online
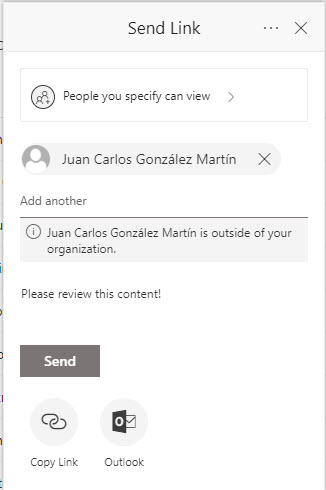
Guest accounts are created when someone shares a document, folder, or site with an external person. The sharing link (Figure 1) contains an invitation for that person, much like adding someone to a team or group creates a sharing invitation that the external person must accept before they can access resources. When the person uses the sharing link, the invitation is accepted, and the guest account becomes fully active.
Management Challenge
Basing secure external access on Azure B2B collaboration is a reasonable and logical approach. It makes sense to use the same mechanism across as many places as possible within Office 365 to avoid recreating the wheels beloved by so many application developers. However, the downside is that you might end up with many more guest accounts in your Azure Active Directory than you anticipate and might need to devote unexpected time to manage those accounts.



