Microsoft Teams External Access Vulnerability Lets Attackers Deliver Malware
Security researchers have recently discovered a new vulnerability in Microsoft Teams. The flaw could enable threat actors to deliver malware to Teams users through a federated chat.
The vulnerability was originally discovered by security researchers Max Corbridge and Tom Ellson from the JUMPSEC Labs’ Red Team. The researchers found that the flaw exists in the External Access feature in Microsoft Teams. It allows users to communicate with individuals outside their organization via Teams chat and video calls.
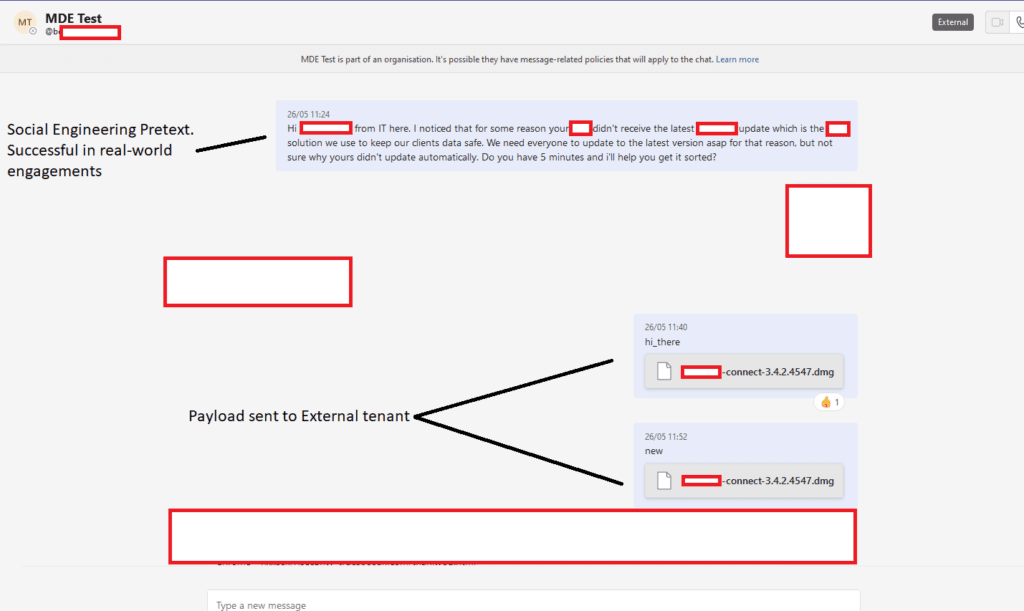
The Microsoft Teams vulnerability enables external users to inject malware into files sent to an employee’s inbox. The file comes with a specially crafted message that tricks users into opening it on their computers. The security flaw lets attackers bypass built-in security measures that protect Teams users against malware and phishing campaigns. It affects all enterprise customers that use the app in its default configuration.
“Exploitation of the vulnerability was straightforward using a traditional IDOR technique of switching the internal and external recipient ID on the POST request,” Corbridge explained in a security advisory. “When sending the payload like this, it is actually hosted on a SharePoint domain and the target downloads it from there. It appears, however, in the target inbox as a file, not a link.”
Microsoft Teams’ external access flaw won’t be quickly patched
The security researchers contacted Microsoft about the vulnerability before disclosing the details publicly. Microsoft, for its part, believes the exploit “does not meet the bar for immediate servicing.” The researchers advised that IT admins should disable the External Access setting in the Microsoft Teams Admin Center.
However, it’s important to note that some may organizations require regular communication with external tenants. In this case, it’s recommended that IT admins should configure Teams security settings to restrict external access to only a set of domains. This approach should make it harder for hackers to compromise user accounts in Microsoft 365 tenants.



