Microsoft Reveals Attackers Used Malicious OAuth Apps to Hack Exchange Online

Microsoft has unveiled a recent cybersecurity attack that allowed the threat actors to compromise Exchange Online. The attacker abused unsecured administrator accounts to gain access to the cloud tenants and created malicious OAuth applications to reconfigure the victim’s email server to send phishing emails.
OAuth is an open-standard authorization protocol that enables users to share specific data with third-party services without revealing their usernames and passwords. First of all, the threat actors targeted administrator accounts that didn’t have multi-factor authentication (MFA) enabled. With this unauthorized access, they created a registered Azure Active Directory (AD) application.
The hackers added the Exchange.ManageAsApp permission to the OAuth app’s service principal and assigned the global administrator and Exchange administrator roles. It allowed the app to manage Exchange Online and Microsoft 365 apps and services. The threat actors also updated the app’s credentials for authentication purposes.
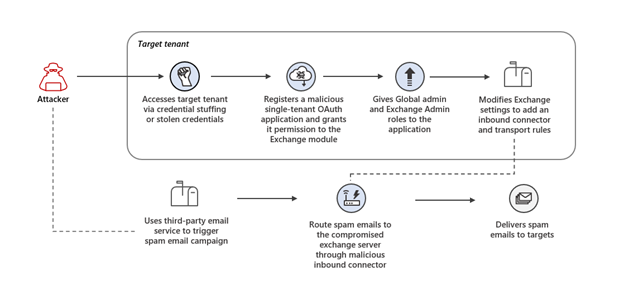
Microsoft says the hackers then used the app to connect to the Exchange Online PowerShell module and change Exchange settings. Finally, the email server routed spam from their IP addresses to trick recipients into providing credit card details. In some cases, the attacker left the app in place for months and used it multiple times for running spam campaigns.
“After each spam campaign, the actor deleted the malicious inbound connector and transport rules to prevent detection, while the application remained deployed in the tenant until the next wave of the attack (in some cases, the app was dormant for months before it was reused by the threat actor),” the Microsoft 365 Defender Research Team explained.
Exchange Online protection against credential-guessing attacks
Microsoft has detailed a couple of recommendations to help organizations prevent credential-guessing attacks. The company advises that organizations should use MFA and conditional access policies to protect their administrator accounts. It is also important to use tools such as Microsoft Defender for Office 365 and Microsoft Defender for Cloud Apps to automate the checking of audit records and app permissions.


