Report: Stolen Microsoft Key Gave Chinese Hackers Widespread Access to Cloud Services

Microsoft has recently disclosed a security breach that allowed Chinese hackers to access the email accounts of around two dozen organizations. Now, security researchers have found that the stolen security key provided access to far beyond Outlook and Exchange Online email accounts.
According to Microsoft, the Chinese hacking group (dubbed Storm-0558) used forged authentication tokens and a stolen consumer signing key to log into Microsoft Cloud email accounts. The list of victims includes US government agencies, including the State Department.
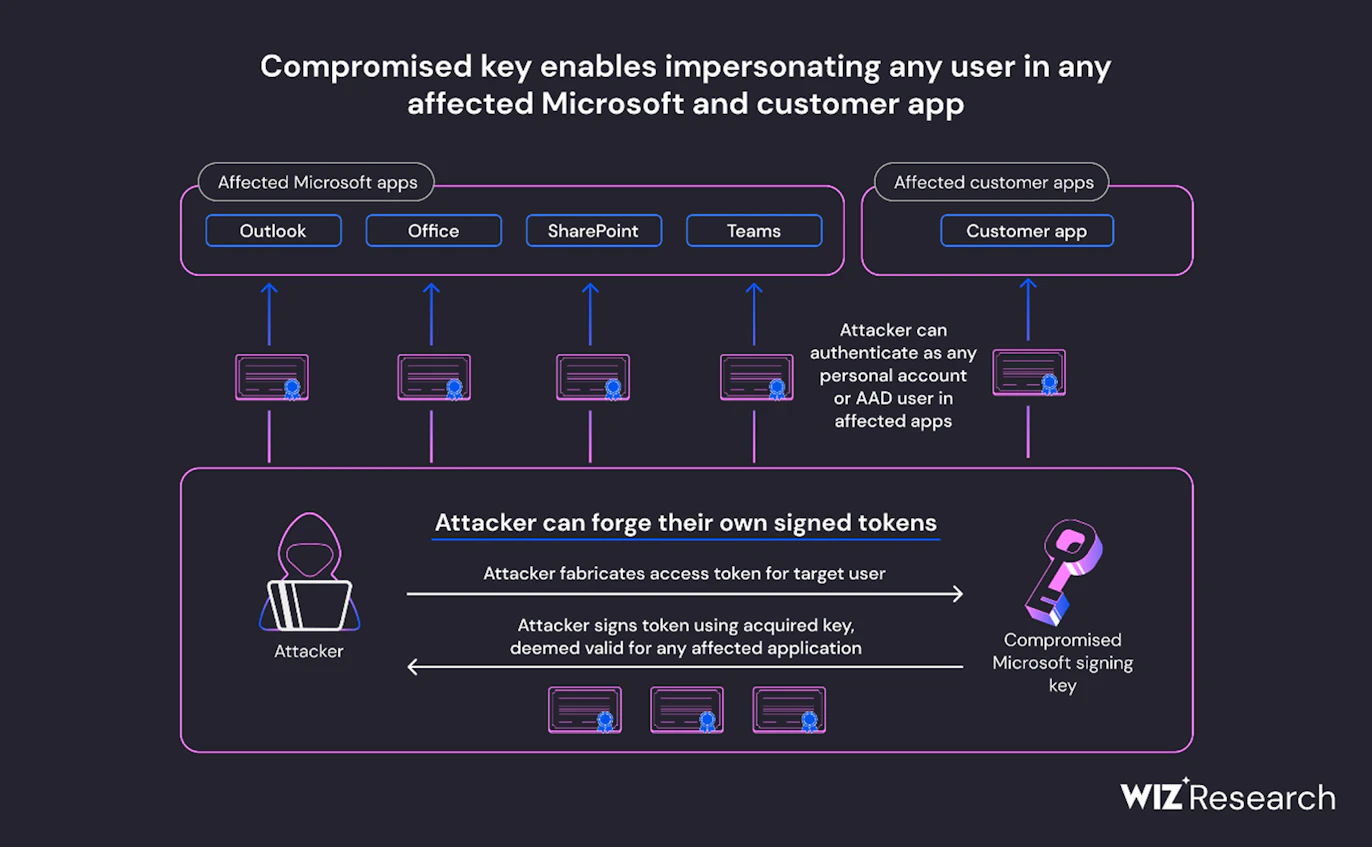
As it turns out, the Wiz security team found that the Chinese hackers could have used the private key to access several other Microsoft products. The attack potentially affected all Microsoft apps that utilize OpenID v2.0 access tokens for account authentication.
“Our researchers concluded that the compromised MSA key could have allowed the threat actor to forge access tokens for multiple types of Azure Active Directory applications, including every application that supports personal account authentication, such as SharePoint, Teams, OneDrive, customers’ applications that support the “login with Microsoft” functionality, and multi-tenant applications in certain conditions,” said Shir Tamari, Head of Research at Wiz.
Microsoft revokes the encryption key to protect Exchange Online and Outlook accounts
Microsoft has now blocked all tokens signed with the compromised encryption key. The company has also published a list of indicators of compromise to help IT admins detect and mitigate the impact in their organizations.
However, the researchers mentioned that the token authentication process would make it harder for customers to detect if malicious actors used the forged tokens to steal data from their applications. They said that it’s due to the lack of token verification log data.
The security researchers warned there’s still a chance that a sophisticated APT could have abused the access to deploy backdoors or establish persistence. Moreover, the applications that use local certificate stores and cached keys would still be vulnerable to exploitation. It’s recommended that customers should refresh those silos at least once a day.
Microsoft has pushed back on the claim
In a statement to The Register, Microsoft rejected the claim made in the research study. “Many of the claims made in this blog are speculative and not evidence-based. We recommend that customers review our blogs, specifically our Microsoft Threat Intelligence blog, to learn more about this incident and investigate their own environments using the Indicators of Compromise (IOCs) that we’ve made public,” a Microsoft spokesperson explained.
Last week, Microsoft announced its plans to offer free access to cloud security logs for all enterprise customers. Currently, this capability is only available for premium customers. The change is expected to take effect in September.


