Microsoft Shares More Details About Chinese Cyberattack That Breached Exchange Email Accounts

Last week, Microsoft confirmed that Chinese hackers gained unauthorized access to email accounts of U.S. government agencies and other sensitive organizations. On Friday, the company detailed a blog post to explain the cause of the security breach that compromised Exchange Online email services.
According to Microsoft’s Threat Intelligence team, the Storm-0558 hacking group abused three vulnerabilities in Exchange Online and Azure Active Directory (Azure AD). The threat actors started exploiting zero-day flaws in the Microsoft cloud services on May 15. They gained access to email data from 25 organizations and other consumer accounts.
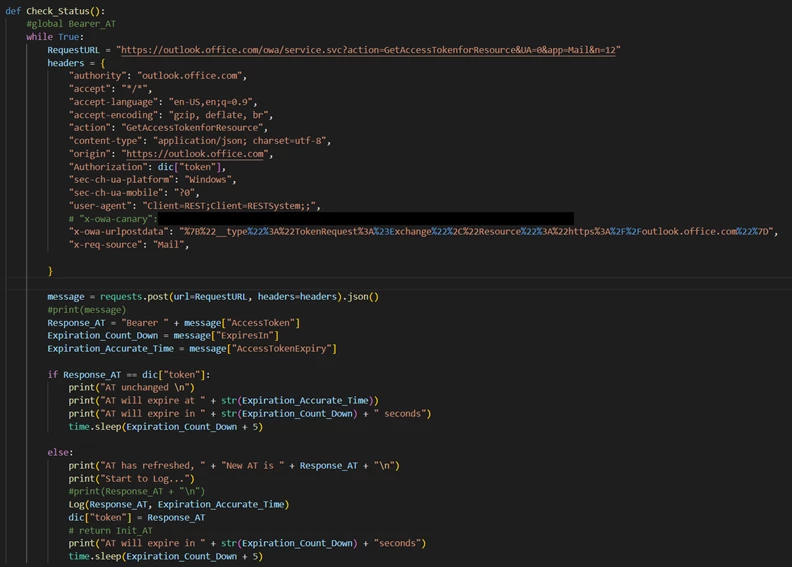
The researchers explained that Storm-0558 first acquired an inactive Microsoft accounts (MSA) consumer signing key. Then, the hackers managed to use it to forge email authentication tokens for Azure AD. The researchers noted that Storm-0558 used the token to access Exchange email accounts through Outlook Web Access (OWA).
“Once authenticated through a legitimate client flow leveraging the forged token, the threat actor accessed the OWA API to retrieve a token for Exchange Online from the GetAccessTokenForResource API used by OWA. The actor was able to obtain new access tokens by presenting one previously issued from this API due to a design flaw,” the Microsoft Threat Intelligence team explained.
Microsoft revokes MSA signing keys to block Exchange email attacks
Microsoft said that it was informed about the intrusion on June 16. The company has since blocked the tokens issued with the stolen signing key to address the issue for all customers. “This flaw in the GetAccessTokenForResourceAPI has since been fixed to only accept tokens issued from Azure AD or MSA respectively. The actor used these tokens to retrieve mail messages from the OWA API,” Microsoft’s researchers added.
Microsoft has found that the Storm-0558 group has now moved to other techniques to target enterprise customers. The company plans to continue to monitor potential malicious activities and boost protections for organizations.



