Mitigate Security Threats: Monitor HTTP Requests with M365 Graph Activity Logs

Key Takeaways:
- Microsoft Graph Activity Logs introduces comprehensive monitoring of HTTP requests within the Microsoft 365 ecosystem, offering detailed insights into API interactions and client application behaviors.
- This new service allows IT admins to detect and mitigate potential security threats, such as suspicious API usage and unauthorized privilege escalations.
- The Microsoft Graph Activity Logs service comes with limitations, including the inability to view the activities of multitenant applications in other tenants and the lack of filtering capabilities in Azure Monitor for Microsoft Graph activity logs.
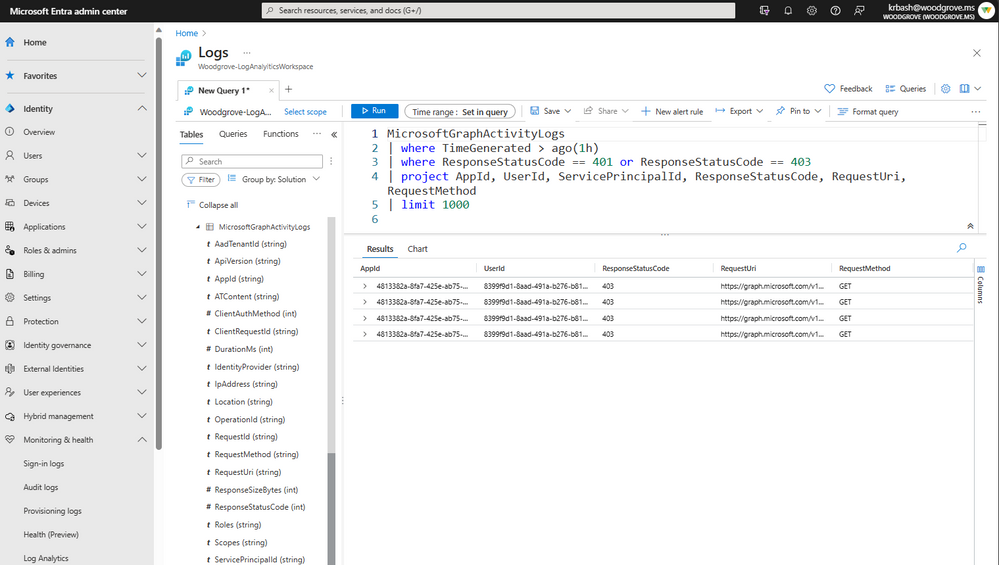
Microsoft has announced the public preview of Microsoft Graph Activity Logs. This new offering is designed to provide organizations with granular insights into HTTP requests processed within the Microsoft Graph service for a particular tenant.
Microsoft Graph Activity Logs offers detailed monitoring of all API requests from various Microsoft 365 apps, SDKs, API clients, and the Microsoft Entra admin center. The service provides valuable insights about the request and client application.
“You’re currently able to collect SignIn logs to analyze authentication activity and Audit logs to see changes to important resources. With Microsoft Graph Activity Logs, you can now investigate the complete picture of activity in your tenant – from token request in SignIn logs, to API request activity (reads, writes, and deletes) in Microsoft Graph Activity Logs, to ultimate resource changes in Audit logs,” Microsoft explained.
Common use cases of Microsoft Graph Activity Logs
The Microsoft Graph Activity Logs service enables IT admins to monitor all the activities that have been performed by a compromised user account within their tenants. The service also makes it easier to detect suspicious/malicious usage of Microsoft Graph APIs. For instance, any application makes probing requests with several 403 errors.
With Microsoft Graph Activity Logs, administrators can investigate unnecessary and unexpected privileged assignments of application permissions. It’s possible to detect problematic behaviors (like extreme call volumes) related to client applications. The service also provides sign-in details that help to correlate Microsoft Graph requests made by an app or a user.
Microsoft notes that administrators can configure to stream the logs through the Azure Resource Manager APIs or the Diagnostic Setting in the Entra portal. Moreover, IT admins can choose to store the logs in an Azure Log Analytics Workspace or use Azure Events Hubs to export to other SIEM tools.
Lastly, Microsoft has acknowledged a couple of limitations associated with Microsoft Graph Activity Logs. The service doesn’t allow users to view the activities of a multitenant application in another tenant. Secondly, it doesn’t support filtering Microsoft Graph activity logs via diagnostic settings in Azure Monitor.


