Microsoft Entra Privileged Identity Management Gets New Capabilities

Key Takeaways:
- Microsoft has released two new capabilities for Entra Privileged Identity Management.
- The PIM for Groups feature lets IT admins enable just-in-time access for all resources that support security group or Microsoft 365 group assignments.
- PIM Integration with Conditional Access allows administrators to enforce granular policies, ensuring strong authentication methods and device compliance.
Microsoft continues to raise the bar in cybersecurity by introducing two new features in its Entra Privileged Identity Management (PIM) solution. The latest update brings support for PIM for Groups and PIM integration with Conditional Access.
Microsoft Entra Privileged Identity Management is a service that allows IT admins to manage, control, and track access to sensitive corporate resources. It’s part of the Microsoft Entra ID Governance solution that helps customers to ensure compliance with security policies. The service provides just-in-time access to Microsoft Entra and Azure resources to mitigate the risk of unauthorized access and data leaks.
PIM for Groups
The new PIM for Groups capability enables IT admins to specify just-in-time group membership and ownership. The feature allows members to use group membership to access various resources in Microsoft Entra ID, Microsoft 365, Microsoft Intune, and other services.
“With the new just-in-time group membership capability, you can now further simplify least privilege access by enabling just-in-time access for all resources that support security group or Microsoft 365 group assignments. This includes support for a wide range of roles such as Microsoft Entra roles, Azure resource roles, Microsoft Intune and non-Microsoft application roles and services,” Microsoft explained.
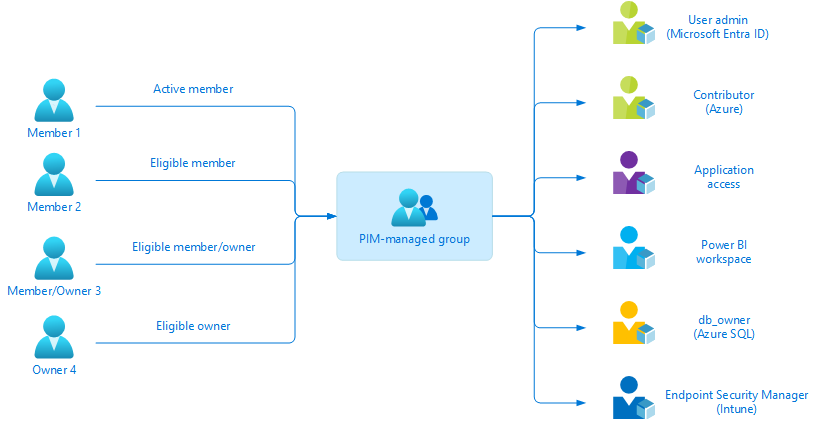
The PIM for Groups feature provides support for role-assignable and non-role-assignable groups. Microsoft has removed a previous limit that prevented IT admins from enabling more than 500 groups per tenant in PIM. Microsoft says that role-assignable groups can only be managed by the group owner, Privileged Role Administrator, or the Global Administrator. However, non-role-assignable groups can be managed by anyone with lower Microsoft Entra roles.
Privileged Identity Management integration with Conditional Access
Microsoft also announced that PIM integration with Conditional Access is now generally available for enterprise customers. The feature allows administrators to apply granular policies to sensitive data and actions. It’s also possible to use the feature to enforce specific requirements for PIM role activations.
Microsoft highlighted that the new integration allows organizations to require modern authentication methods and compliant devices. It also enables administrators to use Microsoft Entra ID Protection to block activation for specific risky users. The new PIM integration with Conditional Access can be used to validate the location of a particular user.


