What’s New in Microsoft Entra Certificate-Based Authentication

Key Takeaways:
- Microsoft Entra CBA now boasts increased flexibility with support for three additional username bindings.
- CBA affinity binding lets IT admins configure protection levels by leveraging certificate attributes during the user authentication process.
- Microsoft has integrated CBA into the Most Recently Used (MRU) methods.
Microsoft has detailed new features and capabilities added to its Entra certificate-based authentication (CBA) since its launch in October 2023. The company highlighted support for three additional username bindings, CBA affinity binding, CBA as Most Recently Used (MRU), and various other improvements.
Microsoft Entra certificate-based authentication (CBA) helps organizations configure phishing-resistant MFA that complies with US federal requirements. The service is designed to encourage customers to migrate their on-premises implementations to the cloud. Microsoft Entra can be either single-factor (SF) or multifactor (MF) based on the tenant configuration.
First off, Microsoft has added support for three additional username bindings to Entra certificate-based authentication (CBA). The list includes IssuerAndSerialNumber, IssuerAndSubject, and Subject Only.
“The username binding policy allows admins to customize how Entra ID will match the certificate being presented by the user with their user account in Entra ID. By default, we map Principal Name in the subject Alternative Name (SAN) attribute of the certificate to UserPrincipalName in the user object. An admin can override the default and create a custom mapping,” Microsoft explained.
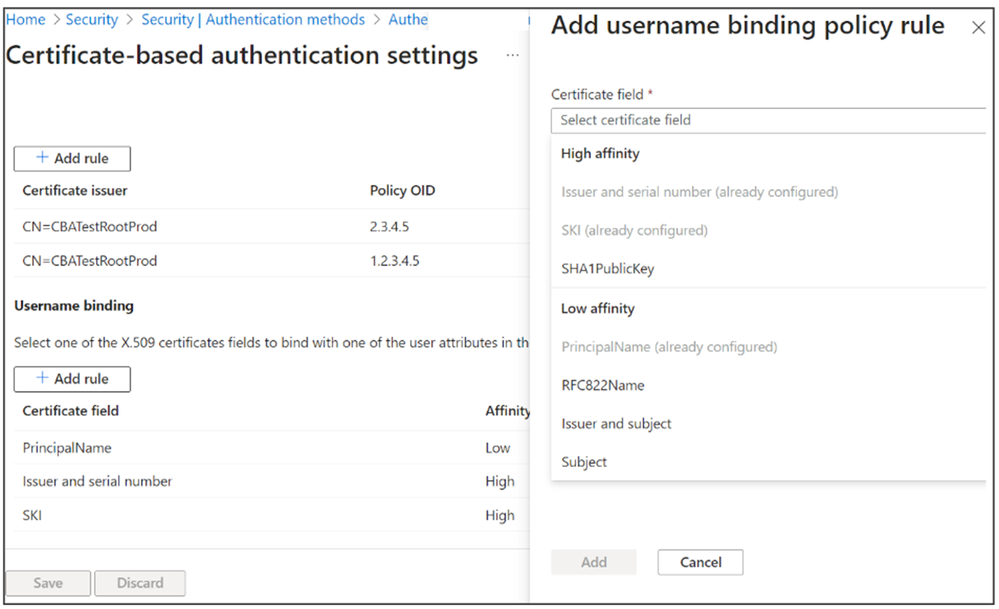
Microsoft Entra CBA Authentication policy rules
Microsoft Entra CBA authentication policy rules allow administrators to configure protection levels for certificates. These protection levels help Entra ID determine whether a certificate is single-factor or multi-factor. Microsoft Entra lets IT Pros set affinity bindings at the tenant level and create custom rules to use high or low affinity mapping. Affinity binding involves using certificate attributes to verify a certificate during the user authentication process.
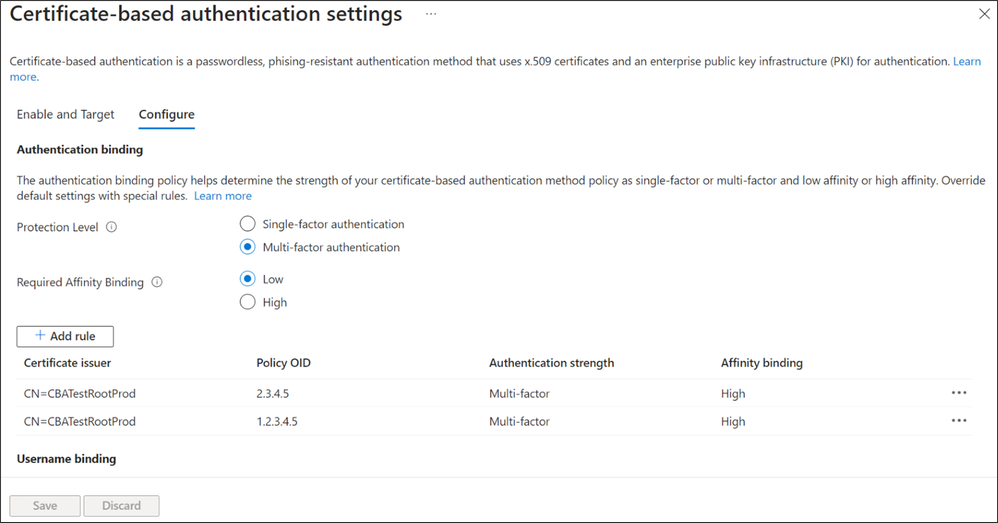
Lastly, Microsoft has announced that certificate-based authentication (CBA) can now be used as a secondary factor to meet multi-factor authentication (MFA) requirements for accessing Entra resources. The company has also added support for CBA in Most Recently Used (MRU) methods. When a user successfully verifies their identity, the system automatically updates the MRU authentication method to CBA. However, users can reset the MRU method anytime by clicking the “Other ways to sign in” button.


