IT Admins Can Now Manually Create Incidents in Microsoft Sentinel

Microsoft announced yesterday some important updates for Microsoft Sentinel. This release brings a new feature that allows IT admins to manually create incident reports for investigation and remediation.
Microsoft Sentinel is a cloud-based security information and event manager (SIEM) solution that helps organizations to analyze large volumes of data in enterprise environments. It leverages threat intelligence and machine learning technologies to detect and investigate security threats and proactively prevent sophisticated attacks. Microsoft Sentinel makes it easier for administrators to manage all their on-premises servers, devices, and applications.
Up until now, Microsoft Sentinel was able to automatically generate incidents based on the logs and alerts pulled from connected data sources such as Microsoft 365 Defender. However, some employees may report security breaches through other means like emails or phone calls.
This release enables security analysts to manually create incident reports for any type of security event to document investigations. It is also possible to manually delete duplicate or faulty security incidents if needed.
“With the “manual incident creation” feature, analysts can now create an incident manually in the Sentinel portal and also by using the new “Create incident (preview)” LogicApp action,” Microsoft explained. “If an incident was mistakenly logged, or is an exact duplicate of another incident, it can now be deleted from the grid using the new “delete” option or using an API – leaving only audit information in the Log Analytics table.”
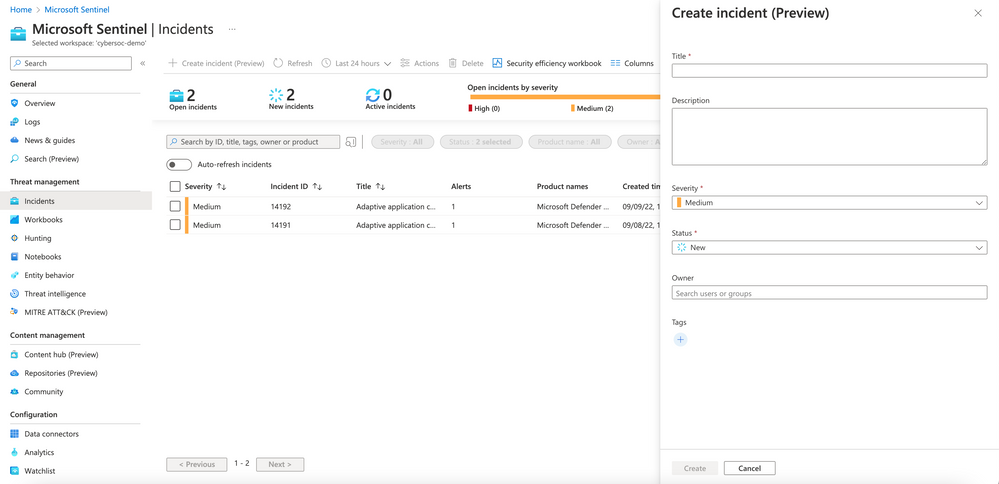
Manual incident creation in Microsoft Sentinel is available in public preview
The new incident creation and deletion capabilities are currently available in preview for Microsoft Sentinel customers. Going forward, Microsoft plans to bring more features to the tool, such as the ability to relate entities or alerts and add evidence. You can learn more about how to manually create incidents in Microsoft Sentinel on this support page.



