How to Enable PowerShell Remoting in Windows 10
Unlike Windows Server, PowerShell Remoting isn’t enabled by default in Windows 10. PowerShell Remoting is a secure management protocol (WSMan) for connecting to and managing remote devices. In its default configuration, PowerShell Remoting secures traffic over HTTP. It’s primarily designed to be used in an Active Directory (AD) environment, which protects the authentication phase using a secure channel between devices and Kerberos.
You can optionally configure PowerShell Remoting to use HTTPS for securing connections to workgroup computers, i.e. devices not joined to AD. Regardless of which transport protocol you choose to use, communication between devices is always encrypted after the authentication phase.
HTTPS vs SSH
HTTPS is a pain to configure because it requires IT to acquire, provision, and manage certificates. To solve this problem, Microsoft introduced the ability to use SSH for PowerShell Remoting in PowerShell Core (PowerShell version 6 or higher). Older versions of PowerShell, and the version that is installed by default in Windows, is known as Windows PowerShell.
If you are managing AD domain-joined devices and you have direct network connectivity, either because you are connected to the same physical network or have a VPN configured for ‘manage out’ scenarios, then PowerShell Remoting over HTTP should work just fine. And it may be the easiest and best option. But if your goal is to manage remote devices that are disconnected from your management network, regardless of whether they are AD domain-joined, SSH is easier to set up and maintain than HTTPS.
PowerShell Remoting using HTTP
In this article, I’m going to show you how to enable PowerShell Remoting in Windows 10 using the default transport protocol, HTTP. We will also assume that the remote device is joined to your AD domain. In a future article, I will show you how to set up PowerShell Remoting using SSH in PowerShell 6.
Log in to the computer on which you want to enable PowerShell Remoting and then start a PowerShell session with administrator privileges:
- In the search box on the taskbar, type powershell and in the search results, click the arrow (>) to the right of Windows PowerShell. In the options on the right, click Run as Administrator. You may be prompted to enter administrator credentials or give consent to run PowerShell.
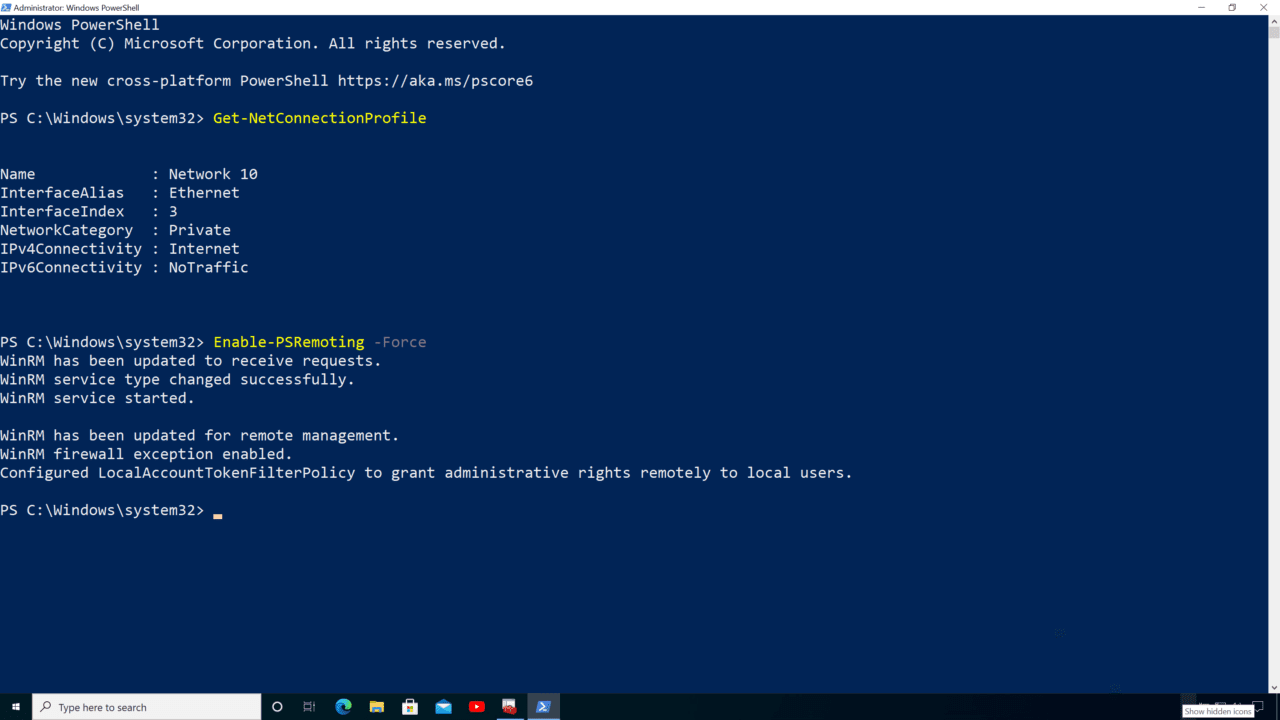
- In the PowerShell window, type Get-NetConnectionProfile and press ENTER. We need to check that the network connection profile is set to Private or DomainAuthenticated before enabling PowerShell Remoting.
- If NetworkCategory isn’t set to Private or DomainAuthenticated, you can set it to Private using the following command:
Set-NetConnectionProfile -NetworkCategory Private
- Now we can enable PowerShell Remoting using the following command:
Enable-PSRemoting -Force
According to Microsoft’s website, when you run Enable-PSRemoting it performs the following tasks:
- Starts the WinRM service
- Sets the startup type on the WinRM service to Automatic
- Creates a listener to accept requests on any IP address
- Enables a firewall exception for WS-Management communications
- Registers the Microsoft.PowerShell and Microsoft.PowerShell.Workflow session configurations, if it they are not already registered
- Registers the Microsoft.PowerShell32 session configuration on 64-bit computers, if it is not already registered
- Enables all session configurations
- Changes the security descriptor of all session configurations to allow remote access
- Restarts the WinRM service to make the preceding changes effective
And that is it! Now you should be able to connect to the device from a management workstation using PowerShell Remoting, providing that you are physically located on the same network or you have a VPN configured for ‘manage out’ scenarios.
For more information on how to connect to devices using PowerShell Remoting, check out PowerShell Remoting Basics on Petri.
Enabling PowerShell Remoting on public networks
Running Enable-PSRemoting turns on a default Windows Firewall rule called Windows Remote Management (HTTP-In). It opens inbound HTTP access on port 5985 for Domain and Private network connection profiles. It is possible to add the -SkipNetworkProfileCheck parameter to Enable-PSRemoting if you want to turn on PowerShell Remoting for use with Public network connection profiles.
By default, -SkipNetworkProfileCheck configures Windows Firewall to allow remote connections from devices on public networks in the same local subnet. If you want to allow connections from devices on public networks from any location, you’ll need to modify the WINRM-HTTP-In-TCP firewall rule using Set-NetFirewallRule as shown below.
Set-NetFirewallRule -Name 'WINRM-HTTP-In-TCP' -RemoteAddress Any
PowerShell Remoting is better for managing servers
If you need to manage a small number of client devices, PowerShell Remoting might be option for your organization. But it is better suited to managing servers because they are static, always available, and they are typically connected directly to your management network and devices.
In contrast, client devices are not always available, and they may connect from different networks and different types of network connection. Services designed for managing endpoints, like Microsoft Intune and Microsoft Endpoint Configuration Manager, allow devices to connect when they come online and regardless of their network location. Microsoft Endpoint Manager helps to ensure that devices are always configured according to company policy without having to wait for an engineer to connect via PowerShell Remoting.
Related article: How to Add Computers to a Domain Using PowerShell